
140 Ascension facilities still reeling from ransomware attack
140 Ascension healthcare units have been disrupted by the Black Basta ransomware group.
Two weeks after the Black Basta ransomware group attacked Ascension, one of the largest private healthcare systems in the United States, the strain is beginning to show. The non-profit organization runs 140 hospitals and senior care centers across 19 states in the US, and health workers—who have had to resort to fax machines for ordering prescriptions, lab work, and imaging—are worried about the consequences of the attack.
In an earlier statement the organization said that:
The care teams are trained for these kinds of disruptions and have initiated procedures to ensure patient care delivery continues to be safe and as minimally impacted as possible.
But healthcare professionals have told The Record that the lack of access to electronic records is creating a dangerous situation.
Without access to electronic record systems, nurses have also struggled to know what blood tests or medications correspond to which patients. Healthcare workers have to use text threads and Google Docs to track medications and patients are being asked to bring in their own documentation to help.
Also, waiting times have reportedly tripled as hospital workers wait longer for test results.
Some ransomware groups claim that they won’t attack organizations actively involved in healthcare, such as hospitals. Apparently, Black Basta has no such compunctions.
Only recently, the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), Department of Health and Human Services (HHS), and Multi-State Information Sharing and Analysis Center (MS-ISAC), released a joint Cybersecurity Advisory (CSA) about the Black Basta group. The advisory reports that threat actors using the ransomware have encrypted and stolen data from at least 12 out of 16 critical infrastructure sectors, including the Healthcare and Public Health (HPH) Sector.
The advisory provides a lot of Indicators of Compromise (IOCs), as well as tactics and techniques related to Black Basta, and is worth a read.
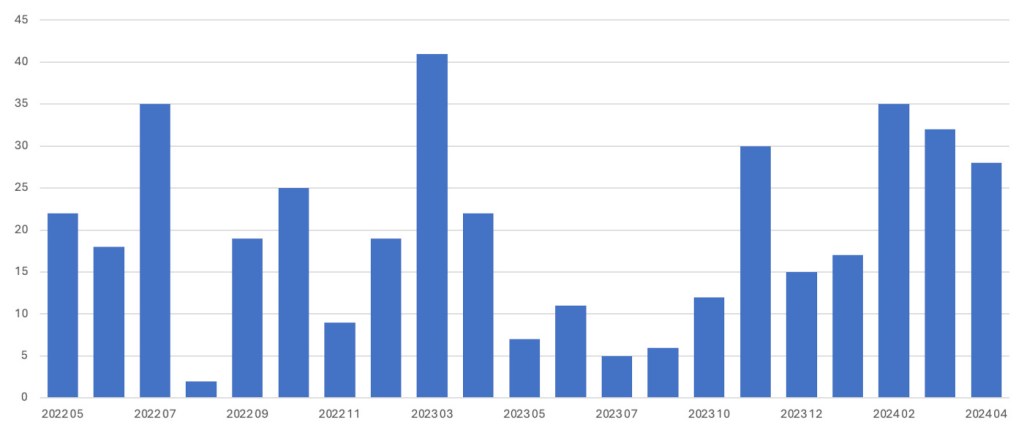
ThreatDown telemetry shows that Black Basta has reported more attacks in the last three months than at any other time in the last two years.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.




