
Alabama State Department of Education stops ransomware attack but the assault on US education continues
More than 60% of global ransomware attacks on education happen in the USA.
Alabama’s education superintendent has disclosed a data breach which happened during a ransomware attack. Although the ransomware attack was noticed and stopped, the attackers managed to steal some data and caused a minor disruption.
Initially, the department disclosed on its website:
On June 17 [2024], Information System (IS) staff at the Alabama State Department of Education (ALSDE) interrupted and stopped an attack on the department’s computer system. IS professionals were able to interrupt and stop the attack before the hackers could access all the targeted servers and lock down our own computer system.
Despite the staff’s intervention, the attackers were able to breach some data and disrupt some services.
On July 3, 2024, superintendent Eric Mackey held a news conference and made assurances that the people affected by the breach will be notified once the compromised is identified.
Because the investigation is still ongoing, the full impact is not clear yet.
While we still do not know the exact content of the information, it is possible that the hackers breached both student and employee data, including some personally identifiable information. We are working with the FBI and other experts to monitor the situation.
Sadly, the situation faced by ALSDE is not unusual. The education sector accounts for 7% of known ransomware attacks in the USA—more than twice the rate faced by the rest of the world.

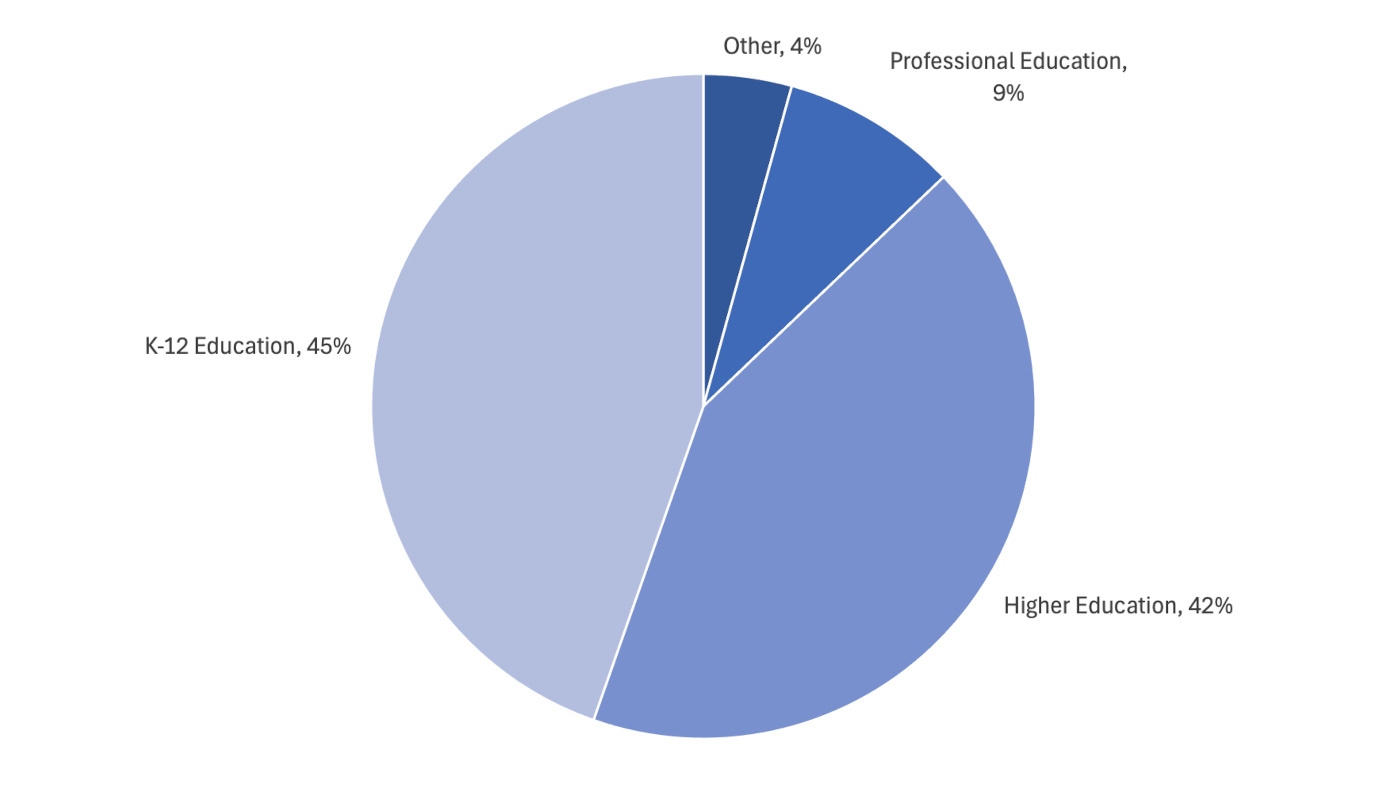
More than 60% of global ransomware attacks on education happen in the USA, and they are split more-or-less evenly between K-12 and higher education. However, there are roughly 130,000 K-12 schools in the USA, and only about 4,000 higher education institutions, so the rate of attacks on higher education is much higher.
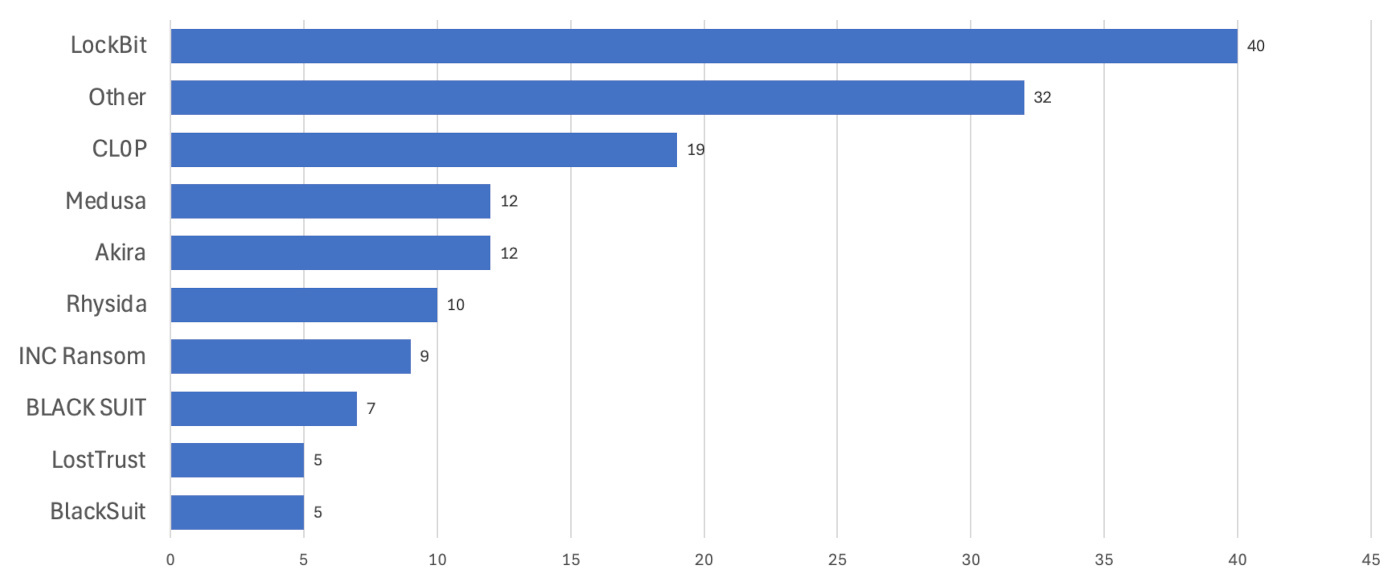
There are at least 31 different ransomware groups responsible for attacks on US education in the last year, and while LockBit is the most active, there is no one group responsible for the extreme percentages.
The high numbers in the US are not new. In 2022, the US Government Accountability Office reported that 647,000 American students were affected by ransomware attacks on K-12 schools in 2021.
Schools are tempting targets for ransomware gangs because they have limited budgets for security, their networks contain sensitive data belonging to both students and parents, and closing them creates immediate disruption for a large group of people.
It’s no wonder then that 2023 was the worst year on record for ransomware in education, with the sector enduring a staggering 70% surge in attacks.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.




