Florida hospital takes entire IT systems offline after ‘ransomware attack’
Tallahassee Memorial Healthcare (TMH), a major hospital system in northern Florida, has reportedly been experiencing an “IT security issue” since Thursday evening, which impacted some of its IT systems. When TMH learned of the issue, it took its entire IT systems offline as a precaution and contacted law enforcement.
In a news post on its website, the hospital says it’s making progress managing the security incident while it continues to operate under IT system downtime protocols, which includes the use of old fashion pen and paper.
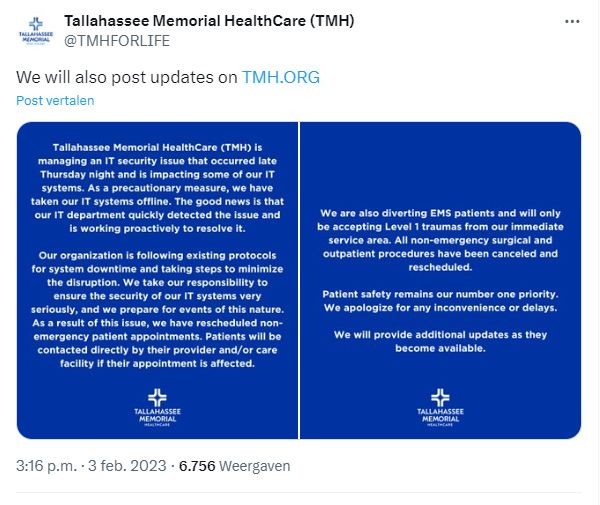
Tallahassee Memorial’s official Twitter account said in a statement on Friday:
While TMH has yet to reveal details about the issue, major news outlets have begun speculating that it could have been hit by a ransomware attack. According to a source who spoke with CNN, Tallahassee Memorial’s CEO Mark O’Bryant told staff on Friday that the system suffered a “cyberattack”.
The hospital has been regularly posting updates about the issue, even if there are no real updates. It says staff is working round the clock to resolve the incident and get the system back up and running as quickly as possible.
TMH has cancelled and rescheduled non-emergency surgical and outpatient procedures, rescheduled non-emergency appointments, and diverted some emergency medical services patients. It says it is continuing to accept Level 1 traumas. The hospital provides healthcare across 21 counties in northern Florida and Georgia.
TMH is the second US hospital victim to suffer from such an attack this year, following Atlantic General Hospital which was hit by ransomware in January.
How to avoid ransomware
There is no doubt hospitals remain under a bullseye, and attackers can strike at any time. Thankfully, there are ways organizations can help reduce their risk of suffering from a ransomware attack.
- Have an incident response (IR) plan. Organizations should accept the fact that a cyberattack is likely to affect them at some point, whether they’re the direct victim or part of a supply chain. An IR plan can direct your responders on what to do in the event of a cybersecurity attack. This should include restoring from backups, client outreach, and reporting to law enforcement among others.
- Educate your staff. Awareness goes a long way, and everyone in the company has a responsibility to keep the organization’s network safe. Staff should be taught social engineering tactics and red flags of a system attack, so they can alert the right personnel quickly should an attack occur.
- Patch as soon as you can. Many threat actors get into networks by exploiting unpatched vulnerabilities. Have a patching plan in place to ensure that your organization’s network is protected against the latest and most exploited weaknesses.
- Backup your files. Backups have saved a lot of organizations after a ransomware attack—provided they work. When you make a plan, ensure you also have provisions for backup testing.
- Get an EDR solution. ThreatDown Endpoint Detection and Response offers built-in ransomware protection, 72-hour ransomware rollback, and zero-day ransomware protection.
Stay safe!




