
How the world’s worst ransomware gang avoids detection
Look at a real example of how LockBit used LOTL techniques on a ThreatDown MDR client.
The ThreatDown MDR team recently stopped a LockBit ransomware attack in its early stages—but not without first tackling a series of Living off the Land (LOTL) techniques used by the attacker.
LOTL techniques are when attackers leverage legitimate system administration tools (i.e PowerShell, WMI, etc) to carry out their attacks, making it difficult for IT teams to detect signs of malicious activities. With LOTL techniques becoming increasingly popular with ransomware gangs, organizations should be aware of how gangs like LockBit use them in their attacks.

Let’s look at a real incident response case where LockBit extensively used LOTL techniques for evasion, lateral movement, and attempted payload delivery on a ThreatDown MDR client.
Stage 1: Reconnaissance
The attack began with the adversary compromising an endpoint within the Windows multi-domain/forest environment. Utilizing the Nltest command (nltest /domain_trusts), they enumerated domain trust relationships to map out the network’s topology. This reconnaissance step aimed to identify potential paths for lateral movement, crucial for spreading the ransomware to other critical systems.
LockBit objective: Understand the network’s structure and identify potential paths for lateral movement.
Legitimate command used: Nltest
Command line:
nltest /domain_trustsLOTL use: Nltest is a built-in Windows command that shows how different sections of the network are connected and allowed to share information. Ransomware attackers use this information to find pathways they can use to move through the network. These trusted connections often allow access without raising alarms, making it easier for attackers to spread unnoticed.
Stage 2: Propagation
Following the reconnaissance, LockBit used Windows Management Instrumentation Command-line (WMIC) to initiate remote processes. By executing the command (wmic /node:10.10.1.23 process call create "c:\\sc.exe"), they attempted to create processes on remote systems, thereby facilitating the spread of the ransomware. This step aimed to broaden the attack’s reach and prepare for the deployment of malicious payloads.
LockBit objective: Initiate and control processes on remote systems to propagate the ransomware across the network.
Legitimate tool used: Windows Management Instrumentation Command-line (WMIC)
Command Line:
wmic /node:10.10.1.23 process call create "c:\\sc.exe"LOTL use: WMIC is a legitimate Windows tool that allows administrators to manage and troubleshoot systems remotely by running commands and scripts. Ransomware attackers use WMIC to execute malicious commands on remote computers within the network.
3. Payload delivery
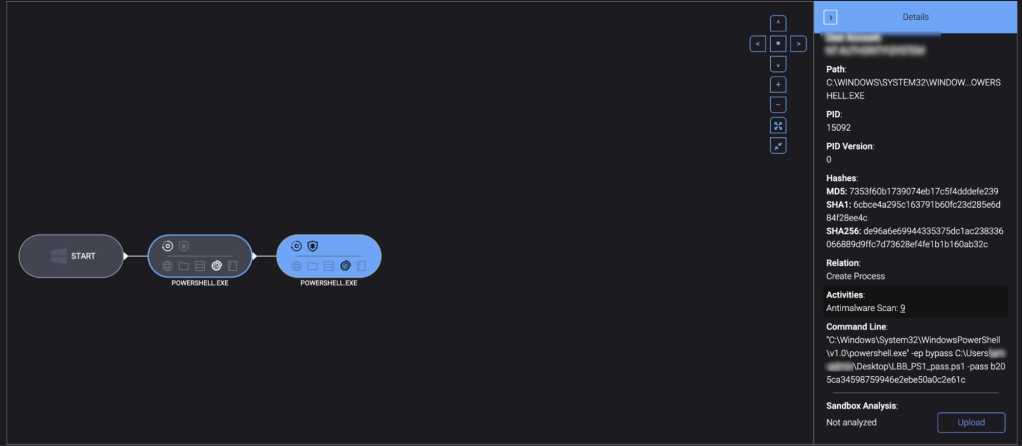
The adversary then executed a malicious PowerShell script (LBB_PS1_pass.ps1) on another endpoint. This script was likely used to bypass execution policies, run the malicious script with administrative privileges, and prepare the environment for the final payload execution.
LockBit objective: Prepare the ransomware payload for execution.
Legitimate tool used: PowerShell
Command Line:
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\**\Desktop\LBB_PS1_pass.ps1 -pass b20 5ca34598759946e2ebe50a0c2e61cLOTL use: PowerShell is a legitimate Windows tool that administrators use for automating tasks and managing configurations. Ransomware attackers exploit PowerShell because its powerful scripting capabilities allow them to execute commands and scripts that can manipulate system settings, download additional malicious payloads, or escalate their privileges.
4. Final payload execution
In the final observed stage of the attack, the adversary employed Rundll32 to execute functions from a DLL file. By running the command (rundll32 C:\Users\[REDACTED]\Desktop\LBB_Rundll32_pass.dll,gdll -pass 6fc09a56f5211c80ab7761587b702020), they aimed to execute malicious code embedded within the DLL.
LockBit objective: Execute the ransomware binary to encrypt files and finalize the system compromise.
Legitimate tool used: Rundll32
Command Line:
rundll32 C:\Users\[REDACTED]\Desktop\LBB_Rundll32_pass.dll,gdll -pass 6fc09a56f5211c80ab7761587b702020LOTL use: Rundll32 is a legitimate Windows tool used to run functions from DLL files. Ransomware attackers use Rundll32 because it allows them to execute malicious code within DLL files, leveraging its capabilities to avoid detection and run their payloads as part of regular system operations.
Detecting evasive ransomware attacks with ThreatDown MDR
The use of LOTL techniques is one of the most dangerous trends the ThreatDown MDR team has observed in ransomware attacks as of late.
In this case, LockBit used four different legitimate commands or tools—Nltest, WMIC, PowerShell, and Rundll32—to not only help them evade detection but also perform key attack functions such as reconnaissance and payload delivery.
Fortunately, the ThreatDown MDR team detected and mitigated the early stages of the LockBit ransomware attack before any damage could be done. Three endpoints were isolated: two domain controllers and one file server. By isolating these endpoints, the team was able to stop the attack before the ransomware was deployed.
The customer is now rebuilding the three endpoints and resetting the compromised user accounts found during the investigation.
Purpose-built for organizations with small (to non-existent) security teams that lack the resources to address emerging threats like Akira ransomware, the ThreatDown Ultimate Bundle includes award-winning technologies and 24x7x365 expert-managed monitoring and response from the ThreatDown MDR team.




