
K-12 district hit with $500k Medusa ransomware attack
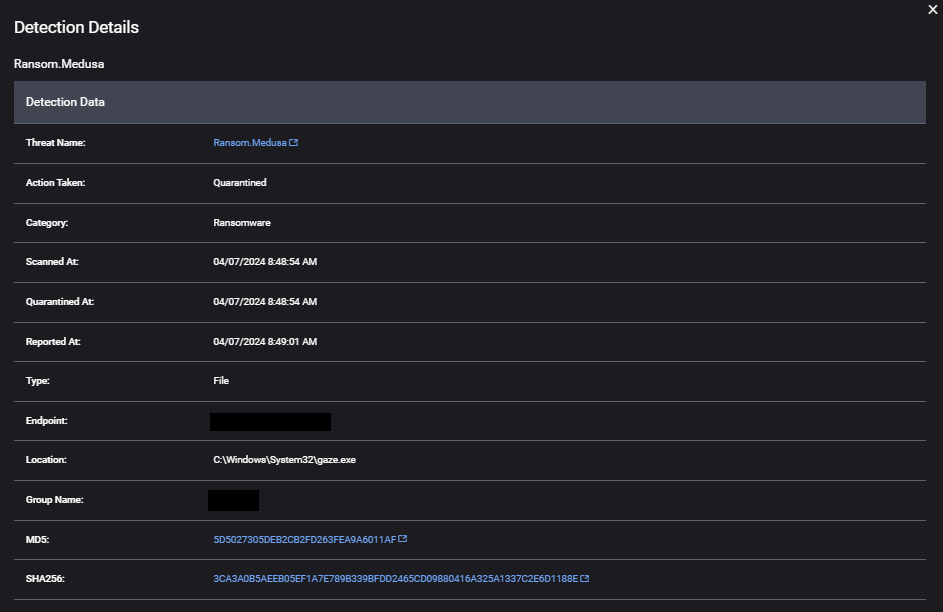
The Medusa ransomware gang claims it has stolen 1.2 TB of data from a large K-12 district.
In late March, Traverse City Area Public Schools (TCAPS) experienced a severe network disruption that shut down schools the following Monday and Tuesday. On April 13th, the ransomware group Medusa announced on their data leak website that they were responsible for the attack, claiming to have stolen 1.2 terabytes (TB) of data and demanding a $500,000 ransom.

Based out of Traverse City, Michigan, TCAPS comprises 11 elementary schools, 2 middle schools, 3 high schools, 1 alternative high school, and 1 Montessori school. It serves a total of 8,908 students and employs 932 staff members.
This incident is part of a broader trend of increased ransomware attacks on educational institutions. According to ThreatDown research, 2023 saw the highest number of ransomware attacks recorded in the education sector, with a 70% increase from the previous year, escalating from 129 incidents in 2022 to 265 in 2023. The number of ransomware attacks on K-12 schools specifically (as opposed to K-12 and higher education combined) rose by 92%, from 51 attacks in 2022 to 98 in 2023.
The majority of these ransomware attacks on education occurred in the US, with 169 attacks reported last year.
Moving into 2024, LockBit is the leading perpetrator of ransomware attacks on education, with 14 confirmed attacks so far.
Medusa has quickly become a major player in the ransomware arena since being first profiled by the ThreatDown intelligence team in March 2023. The group has executed 194 confirmed attacks since then. The education sector is one of Medusa’s primary targets, accounting for 19 of these attacks, making them the 6th most prevalent ransomware group attacking educational institutions since February 2022.
Stopping Medusa ransomware
Medusa has made a big name for itself in a short amount of time.
While it looks like Medusa will attack anyone they think is an easy target, it’s safe to say that educational organizations in the USA should be particularly wary of Medusa considering their strong focus on that country and sector.
ThreatDowns’ EDR anti-ransomware layer constantly monitors endpoint systems and automatically kills processes associated with ransomware activity, including Medusa ransomware.
In our ThreatDown K-12 Bundle, you’ll find everything your district needs to protect staff and student devices from ransomware attacks. Learn more.




