
Process Explorer: part two
For Windows operating systems (OS), especially those up to and including Windows 7, Process Explorer is an excellent replacement for Task Manager. After publishing part 1: an introduction I received some questions, requests and comments that I will try to cover here.
(Stop) Replacing Task Manager
First of all I was asked to mention that undoing the replacement of Task Manager by Process Explorer is just as easy as applying the setting. If you have replaced Task Manager with Process Explorer you will find the option “Restore Task Manager” under “Options” in the main menu of Process Explorer.
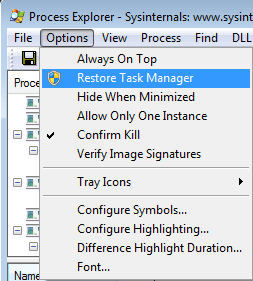
To be able to use it you will need Administrator privileges. Effectively this removes the IFEO key that took care of the interception of calls to taskmgr.exe.
Malware running as svchost.exe
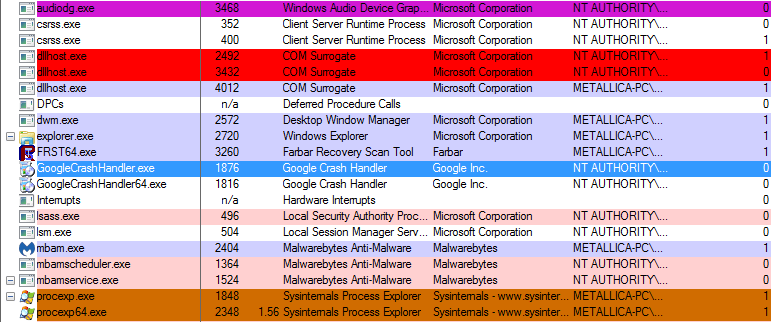
A popular name and process to abuse for malware is svchost.exe. One of the reasons for that is that you will see many instances of it running in your list of processes.
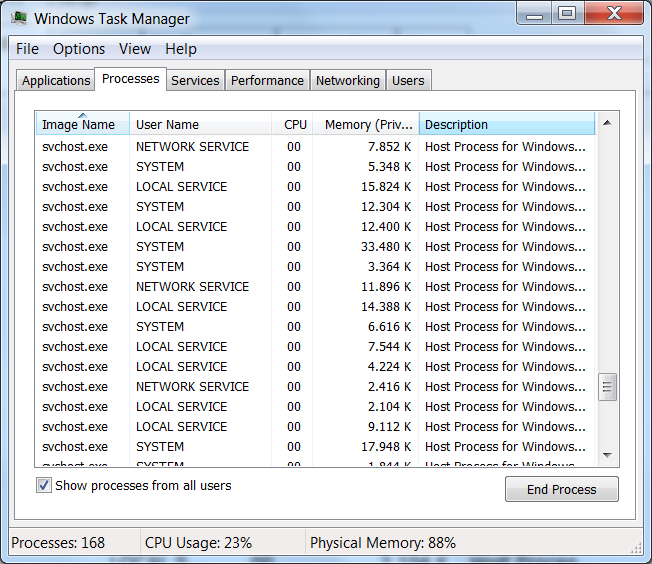
Not a good place for a game of whack-a-mole
None of the above happen to be malware, but how can Process Explorer be helpful if we want to identify a malware process in that long list?
First note that there are two ways of displaying the list of processes in Process Explorer (three actually to be completely accurate) which you can toggle by clicking on the Process bar above the list which switches between alphabetical, reverse alphabetical and one view that shows the parent > child relations as shown below. Legitimate svchost.exe processes should be children of services.exe.
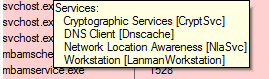
Also, if you hover over the svchost.exe process you should notice that a tooltip displays which services are running under that svchost.exe process.
Another thing to look at is the “User Name” the process is running under. If you enable the column “User Name” under “View” > “Select Columns” and are running Process Explorer as an Administrator then you can check the “User Names” for svchost.exe processes. They should be one of these:
- NT AUTHORITYSYSTEM,
- LOCAL SERVICE
- NETWORK SERVICE
Also, when running Process Explorer as administrator and checking the “Properties” of a process, looking at the “Command line” field on the “Image” tab, the command line should start with “C:WindowsSystem32svchost.exe –k” for Windows processes.
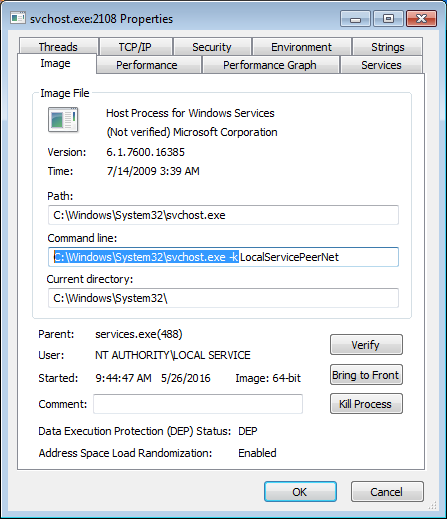
Another useful column when researching svchost.exe processes is the “Session” column. Every legitimate svchost.exe process should have a “0” in that column. The same is true for spoolsv.exe which is another process-name often mimicked by malware.
Color coding
Process Explorer uses color coding as extra information about the processes. The colors and their meaning:
- The color purple in Process Explorer is an indication that the files may be packed.
- The color red means that the process is exiting (being stopped).
- The color green means the process was freshly spawned (just loaded).
- The light blue processes are those run by the same account that started Process Explorer.
- The dark blue indicates that the process is selected (by clicking or otherwise).
- The color pink indicates that the process is a service (like our friend svchost.exe).
- If you “Suspend” a process it will turn dark grey until you “Resume” it.
Procexp64
If you’re running on a 64-bit OS, you may have noticed a second executable in the folder containing Process Explorer called ‘procexp64’. This is a temporary file especially created for 64-bit machines and it should disappear when you close Process Explorer.
Handles
Handles come in handy when you are looking to find out which process is stopping you from removing a file. To see the “Handles” click “View” > enable “Show Lower Pane” and select “Handles”.
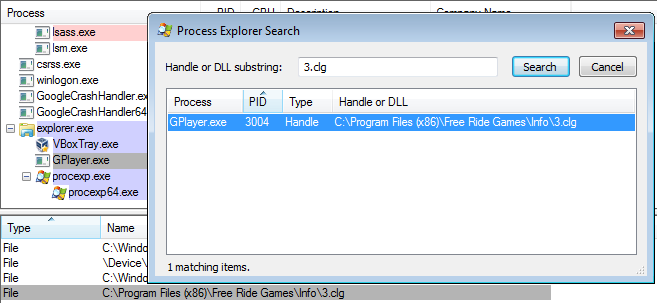
To look up which process is keeping a file open, you can click “Find” > “Find Handle or DLL…” and then type the name of the file you want to check on. Click the “Search” button and Process Explorer will show you a list of processes that have the file in use. Select the one you want to terminate and this will select the handle in the lower pane. Right-click the handle in the lower pane and choose the option “Close Handle”. When the handle no longer shows up in the search results, you should be able to delete the file.
Summary
This post is a follow-up about Process Explorer, among others we discuss the color coding, handles, and finding more information about services.
Links
Understanding Process Explorer
How To Delete, Move, or Rename Locked Files in Windows
Malwarebytes Managed Detection and Response (MDR) simply and effectively closes your security resources gap, reduces your risk of unknown threats, and increases your security efficiency exponentially. Malwarebytes MDR staffs highly experienced Tier 2 and Tier 3 analysts who are hands-on with customer endpoints, ensuring critical threats are quickly identified and a thorough response is rapidly deployed.
Learn more about what ThreatDown has to offer.




