
Ransomware review: April 2024
In March, we recorded a total of 389 ransomware victims—the most so far all year.
Threat Intelligence Team
This article is based on research by Marcelo Rivero, Malwarebytes’ ransomware specialist, who monitors information published by ransomware gangs on their Dark Web sites. In this report, “known attacks” are those where the victim did not pay a ransom. This provides the best overall picture of ransomware activity, but the true number of attacks is far higher.
In March, we recorded a total of 389 ransomware victims—the most so far this year. After a turbulent February that saw the disruptions of the two biggest ransomware gangs, March brought calmer waters from which the full implications of the takedowns could be assessed. The picture that emerged is a complex one, revealing ransomware gangs are alternatively less and more resilient than we originally thought.
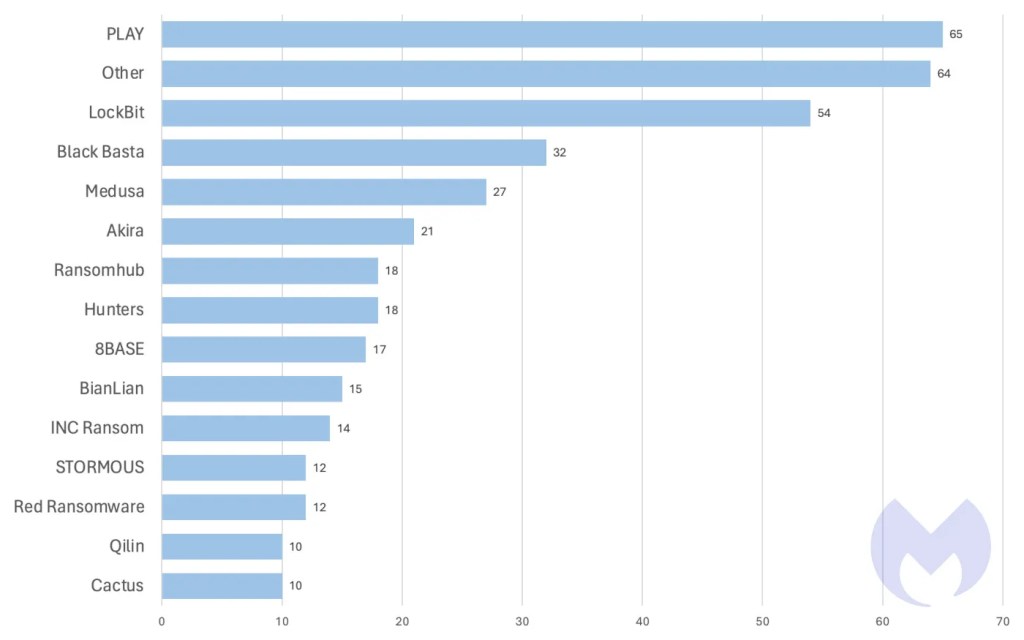
Not long after a devastating law enforcement action in late February, for example, LockBit appears to have resaddled itself in March—albeit not without some scratches and bruises. Their 54 victims in March might be some of their lowest numbers in months, but nevertheless, the victim count points to the still-beating heart of a Goliath in decline. Instead of rebranding, as many ransomware gangs do after going bust, LockBit quickly set up new infrastructure and resumed attacks using updated encryptors.
Of course, given the reputational blow they suffered at the hands of the law, LockBit has a vested interest in projecting itself as more resilient than it actually is. Some of the data posted on their leak site last month is from companies attacked in 2022 and 2023, according to an analysis from Valéry Marchive, indicating that at least a portion of their “activity” in March is mere chest-puffing. Nevertheless, to see LockBit on this month’s charts at all—especially as their affiliates only continue to be arrested—is surprising, and suggests that the group is determined to claw their way to the very bitter end, a mentality we cannot take for granted from busted gangs, considering how another top gang, ALPHV, went down.
If the fork in the road for busted gangs is either “double-down” or “rebrand,” than ALPHV represents a complicated third-option of “Self-implode, exit-scam, and ultimately blame it all on the Feds.” But by our lights, while we might have seen the end of “ALPHV, the gang,” what happens to “ALPHV, the criminals,” remains to be seen. After all, “ALPHV, the gang” is just the latest in a series of rebrands from a group of cybercriminals who at one point in time called themselves “DarkSide” (shut down in 2021) and at another called themselves “BlackMatter” (also shut down in 2021). Only time will tell if the group reassembles under yet another banner or decides to abandon ransomware altogether.
The real winner after all of these major busts, though? It may not be law enforcement, or even victims and defenders of ransomware attacks in general; it may just be rival gangs. In the midst of ALPHV’s demise and LockBit’s stumbling back onto its feet, top gangs such as PLAY, Black Basta, and Medusa sense an opportunity to poach affiliates from both gangs. It’s no different from how any other business might take advantage of the downfall of a competitor. At the end of the day, affiliates don’t care where they get their ransomware-as-a-service from, and smaller ransomware gangs are happy to pick up where more “popular” alternatives left off. This is clear from PLAY’s historic 65 attacks last month to occupy the top spot in our monthly charts for the first time. Affiliates may just be defaulting to the second- or even third-best options, indirectly creating new paradigm shifts in the ransomware landscape.
New ransomware gangs
Red Ransomware Group
The Red Ransomware Group (also known as Red CryptoApp) is a new ransomware group that pushed 12 victims on their leak site last month.
RA World (RA Group rebrand)
RA World, previously known as RA Group, is a new ransomware group that primarily attacks the healthcare and finance sectors
Donex
Donex is a new ransomware gang that primarily attacks organizations in United States and Europe.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.




