
ThreatDown DNS Filtering updates: New changes to domain blocking rules and setup process
After popular request, the ThreatDown Product Engineering team has added the ability for Nebula users to block top-level domains (TLD) and result IP addresses in ThreatDown DNS Filtering. Additionally, the setup process for DNS Filtering has been condensed into a more intuitive two-step flow.
Let’s dive into the new changes.
New blocking criteria
Admins can now block domains by top-level domain (e.g. .com, .gov, .edu, etc.), which allows filtering entire domain types like commercial sites, government sites, or TLDs from specific countries due to political reasons or to comply with national sanctions. They can also block by resolve IP address, enabling filtering based on the specific numeric IP address a domain resolves to.
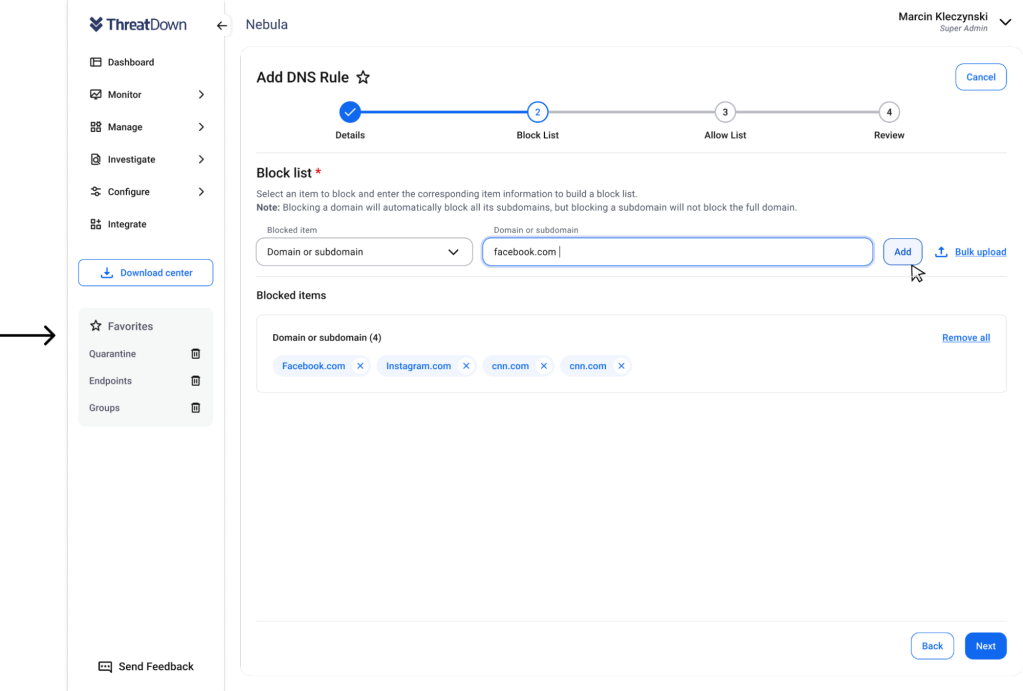
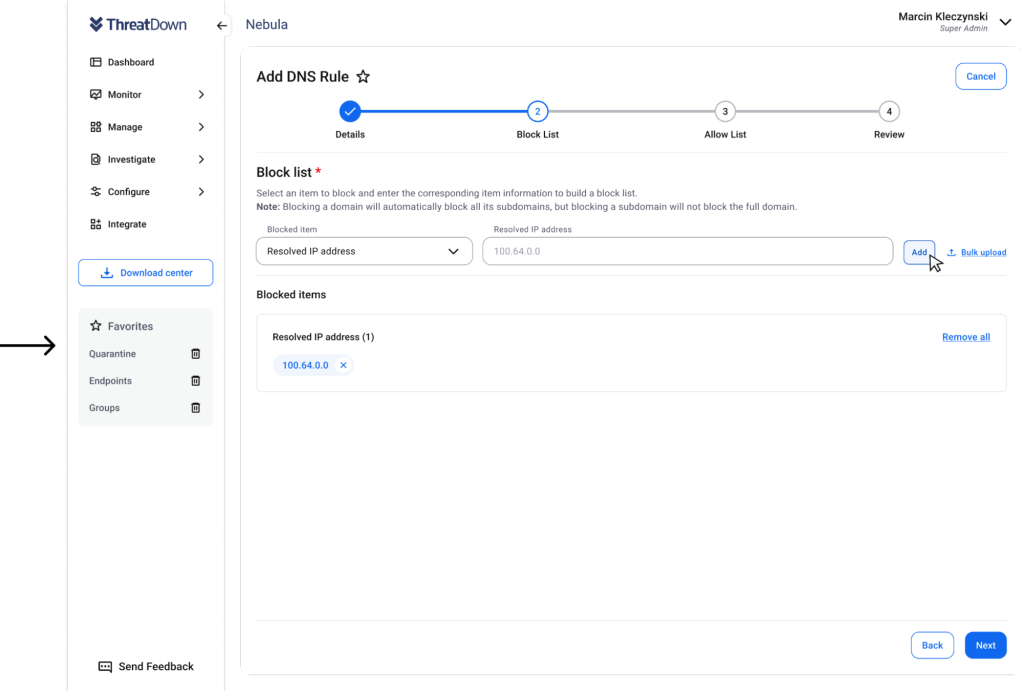
Streamlined rule creation
Previously, the DNS rule creation wizard walked administrators through three distinct steps: selecting content/security categories, defining the allow list, and then the block list. The team has streamlined this process to be more straightforward. Now, rather than separate steps, the category selections are directly included as part of the block list step. This simplifies rule setup into a two-step workflow of defining the block list first, followed by the allow list.

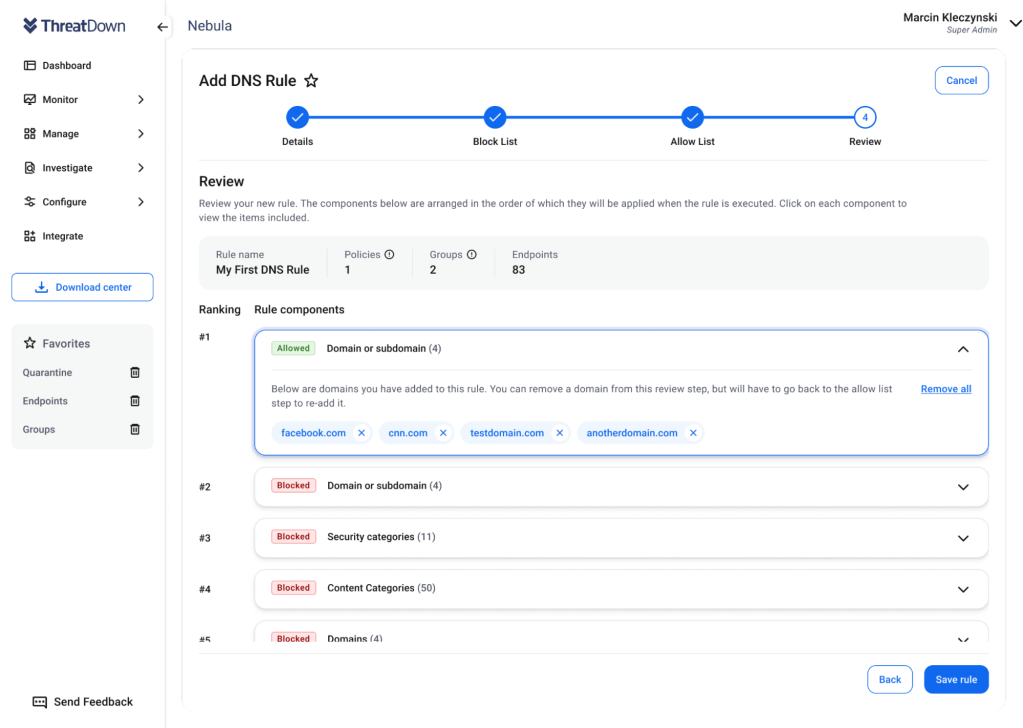
New Review step added
A new review step has been added that allows users to understand the order/hierarchy by which the rule components in a rule are executed. Previously, it was less clear how to resolve conflicts in the rule components (like if a specific domain was allowed but it was in a blocked category).
Try ThreatDown DNS Filtering today
ThreatDown DNS Filter is included in the ThreatDown Ultimate Bundle, which combines crucial technologies and services—such as Patch Management, Ransomware Rollback, and Managed Detection and Response (MDR)—into one cost-effective package. Learn more.




