
Beluga phishing campaign targets OneDrive credentials
The Beluga phishing campaign uses .htm files to capture your company OneDrive credentials.
Recently, we found an online example of the Beluga phishing campaign—a highly customizable campaign with your company’s OneDrive credentials in its sights.
Beluga phishing campaigns use an .htm form in an email attachment that’s tailored for the target, showing them their own email address pre-filled, and the logo of their company.
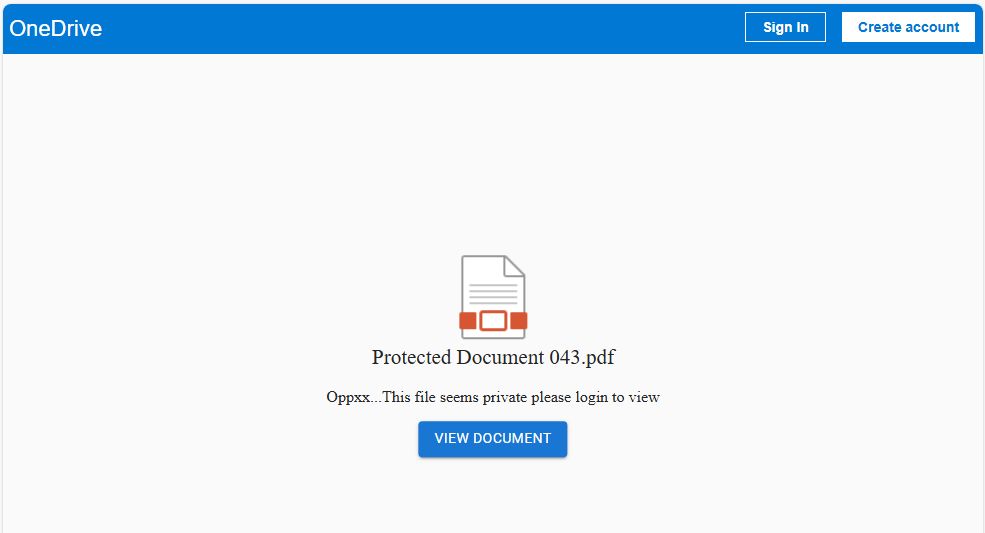
In the campaign that we discovered, the .htm file looks like a OneDrive page that instructs readers to log in to view a PDF called “Protected Document 043.pdf” by clicking a “VIEW DOCUMENT” button. One clear giveaway that this is a scam is that the “Sign In” and “Create account” buttons don’t work.
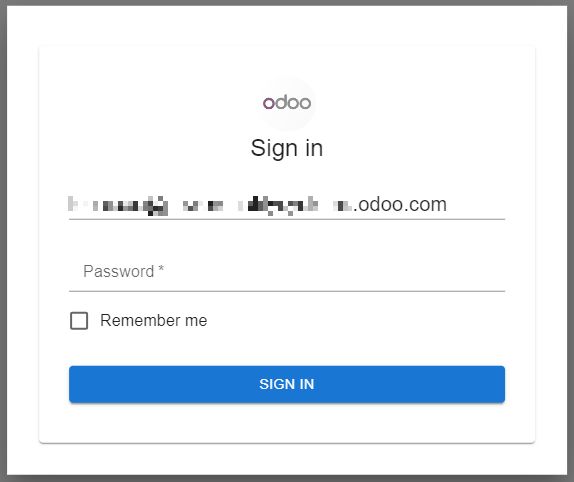
If the target decides to click the “VIEW DOCUMENT” button on the .htm file, they will see a personalized login form with their email address already filled in, alongside the logo of the company the email address belongs to, adding some extra credibility. Another sign that this is a scam is that, unlike a real login form, the email address cannot be changed.
Whether you feed the form the correct password or not, it will tell you that the password you entered was wrong.
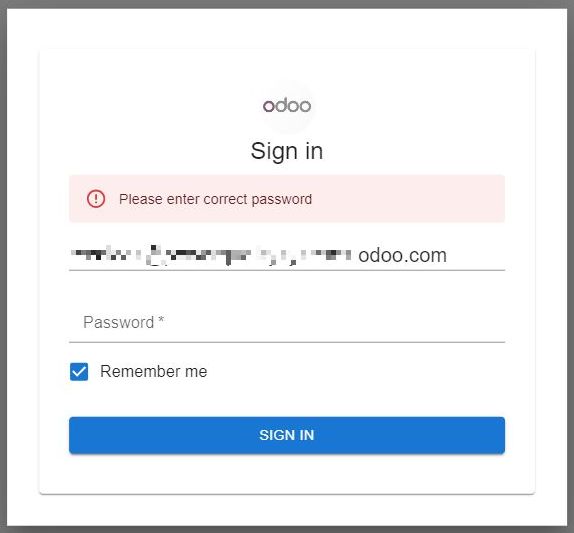
Behind the scenes, however, your password is sent in an HTTPS request to a Telegram bot, along with your email and IP address.

Telegram bots are programs that run inside the Telegram messaging platform, performing tasks like sending messages, retrieving information, or interacting with users.
Cybercriminals, particularly phishers, have increasingly turned to Telegram bots as a tool for gathering credentials and conducting large-scale scams. Using Telegram provides them with easy way to collect and manage the data they steal, and to automate various aspects of their phishing campaigns.
With a set of company OneDrive credentials, the cybercriminals have a variety of options:
- They can look for sensitive data stored in OneDrive, including confidential documents, financial information, and intellectual property.
- They can exploit the synchronization feature of OneDrive to infect local devices connected to the compromised account.
- Ransomware gangs could delete possible backups or encrypt important files stored in the OneDrive account.
To mitigate these risks, organizations should implement strong security measures such as two-factor authentication, regular security audits, and access control for which files and folders can be shared with specific users.
IOCs
api.telegram.org/bot7205263787
api.telegram.org/bot7207687399
“Protected Document 043.pdf” is a constant
Advance Remmittance(Pdf).htm
EFT Payment 04091988 PDF.htm





