
Cleo, the next MOVEit and GoAnywhere?
The CL0P ransomware gang has claimed responsibility for attacks exploiting a vulnerability in Cleo file sharing products.
In 2023, the CL0P ransomware gang broke the scalability barrier and shook the security world with a series of short, automated campaigns, hitting hundreds of unsuspecting targets simultaneously with attacks based on zero-day exploits in file sharing software like MOVEit Transfer and GoAnywhere MFT.
By weaponizing zero-day vulnerabilities in file sharing software, the CL0P ransomware gang was able to rack up hundreds of victims in one-off campaigns. And it looks as if it’s on the verge of repeating it.
Cleo is a business-to-business (B2B) tech platform provider that specializes in managed file transfer (MFT) solutions, like Cleo Harmony, VLTrader, and LexiCom.
In October 2024, Cleo patched a critical vulnerability (CVE-2024-50623) in its products. This vulnerability allowed for unrestricted file uploads and downloads, potentially leading to remote code execution (RCE).
When telemetry showed the attacks on fully patched systems continued, at first the patch was thought to be incomplete. But more research learned that the attackers were using another vulnerability, now tracked as CVE-2024-55956. This vulnerability allows an unauthenticated user to import and execute arbitrary Bash or PowerShell commands on the host system by leveraging the default settings of the Autorun directory.
Exploitation of this vulnerability led to the deployment of a previously unknown Java backdoor named Malichus on compromised Cleo servers. Malichus allows attackers to steal data, execute commands, and move laterally across a compromised network.
CL0P, which previously exploited file transfer services MOVEit Transfer and GoAnywhere in its 2023 campaigns, was an immediate suspect, and its dark web leak site—where it normally lists victims—now mentions “attack of CLEO.”
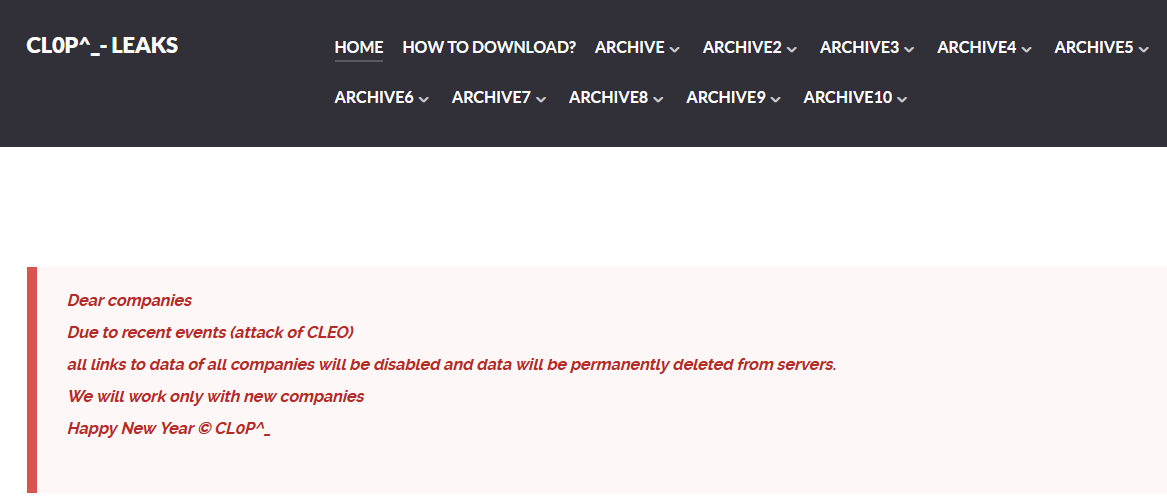
The announcement reads:
Dear companies
Due to recent events (attack of CLEO)
all links to data of all companies will be disabled and data will be permanently deleted from servers.
We will work only with new companies
Happy New Year © CL0P^_
Does this mean CL0P has infiltrated so many victims with the Cleo vulnerabilities that it needed to make room? We can only hope not.
On the leak site, there are no new victims listed yet. CL0P has advised that it will delete, as per usual, all data belonging to government services, research institutions, and healthcare organizations.

Cleo has released patches, and advised those that are unable to patch to disable the Autorun feature by going into System Options and clearing out the Autorun directory. Although this will not block the attacks, it reduces the attack surface.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like Malwarebytes EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.





