
London Drugs closes retail stores after ransomware attack
Canadian pharmacy retail giant London Drugs is reeling from a cyberattack.
On Sunday, Vancouver-based London Drugs closed all its stores and its ecommerce site was unavailable after a weekend cyberattack disrupted its operations. The Canadian company operates 79 stores, most of them in British Columbia and Alberta, as well as in Saskatchewan and Manitoba.
It says that pharmacists are on site even though the stores are temporarily closed, so, if you have a prescription pickup, you can get a pharmacist to fetch it for you.
In a tweet on Monday April 29, 2024 it stated:
On April 28, 2024, London Drugs discovered that it was a victim of a cybersecurity incident. Out of an abundance of caution, London Drugs is temporarily closing stores across Western Canada until further notice. Upon discovering the incident, London Drugs immediately undertook counter measures to protect its network and data, including retaining leading third-party cybersecurity experts to assist with containment, remediation and to conduct a forensic investigation.
At this time, we have no reason to believe that customer or employee data has been impacted.
Pharmacists are standing by to support any customers with urgent pharmacy needs. We advise customers to phone their local store’s pharmacy to make arrangements. We apologize for any inconvenience caused and we want to assure you that this incident is the utmost priority for us at London Drugs.
Thank you for your patience.
London Drugs says it has hired external experts to investigate the cyberattack, but it has all the hallmarks of a ransomware attack.
There are thousands of “big game” ransomware attacks like this every year—large scale cyberattacks that can bring entire organizations to a halt, and Ransomware attacks on US healthcare and healthcare-related businesses have doubled year over year.
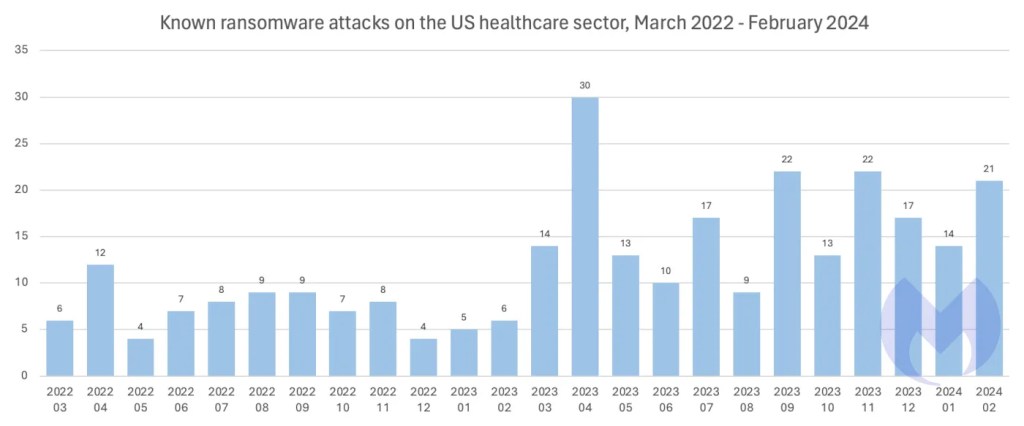
Ransomware attacks are always damaging, and they always cause pain, but when they hit the healthcare system, the consequences—particularly the risk to life—are often more immediately obvious and shocking. Besides the disruption, it’s very likely that sensitive data has been stolen and will be used as leverage to extract a ransom demand.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
Our business solutions remove all remnants of ransomware and prevent you from getting reinfected. Want to learn more about how we can help protect your business?




