
MITRE breached through Ivanti Connect Secure vulnerabilities
MITRE was breached by a threat actor leveraging two Ivanti Connect Secure vulnerabilities.
As a perfect example that it can happen to anyone, MITRE has disclosed that it experienced a breach.
MITRE is a not-for-profit corporation that focuses on four key areas: data acquisition, data processing, system sciences, and computer programming. It wants to bring security focused communities together to develop more effective cybersecurity. It’s well known for running the CVE database of known vulnerabilities, and for the widely respected MITRE ATT&CK framework.
The MITRE ATT&CK framework is a knowledge base of offensive tactics and techniques based on real-world observations. It contains information about malicious groups and techniques, and it’s open and available to any person or organization for use at no charge. It’s used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community.
MITRE also does independent testing of security products called ATT&CK Evaluation, where it tests a solution’s effectiveness against real world attack scenarios. Last year, the evaluation tested 30 vendor solutions against Turla, a sophisticated Russia-based advanced persistent threat (APT) group with victims in over 45 countries.
MITRE noticed a breach of its systems in January 2024 that was initiated by chaining two Ivanti VPN zero-days. After detecting suspicious activity on its network, an investigation indicated compromise by a foreign nation-state threat actor. The investigation is still ongoing, including research to determine the scope of information that may be involved. But there is no indication that MITRE’s core enterprise network or partners’ systems were affected by this incident.
Jason Providakes, president and CEO, MITRE said:
No organization is immune from this type of cyber-attack, not even one that strives to maintain the highest cybersecurity possible. We are disclosing this incident in a timely manner because of our commitment to operate in the public interest and to advocate for best practices that enhance enterprise security as well necessary measures to improve the industry’s current cyber defense posture. The threats and cyber-attacks are becoming more sophisticated and require increased vigilance and defense approaches. As we have previously, we will share our learnings from this experience to help others and evolve our own practices.
Even though MITRE followed best practices, vendor instructions, and the government’s advice to upgrade, replace, and harden their Ivanti system, the actions were insufficient.
In a detailed graph which we will explain below, MITRE shows the attack flow, using its own Att&ck Techniques terminology.
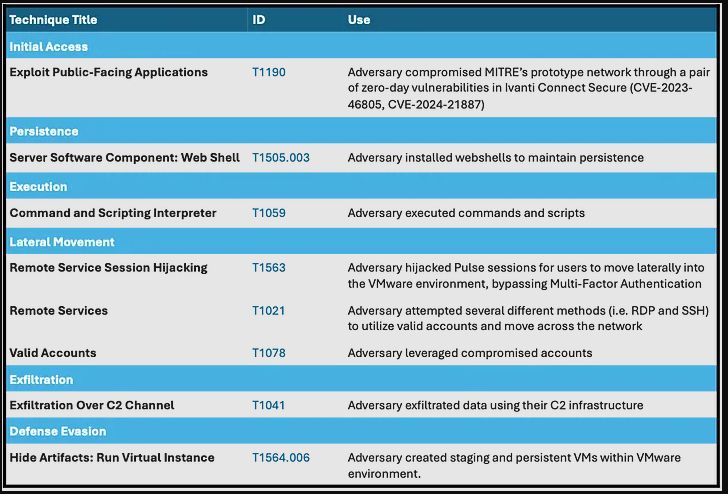
Initial access was gained by exploiting vulnerabilities in public facing applications. On January 10, 2024, Ivanti released advisories about two actively exploited vulnerabilities in all supported versions of Ivanti Connect Secure and Ivanti Policy Secure Gateways. Active exploitation was recorded dating back as far as December 3, 2023. These vulnerabilities were listed as CVE-2023-46805 and CVE-2024-21887.
The vulnerabilities allowed the attacker to install web shells on an openly accessible web server. A web shell is a script that can be used by an attacker to run remote commands and gain persistence on an already compromised system.
The attacker abused command and script interpreters to execute commands and scripts. These interfaces and languages provide ways of interacting with computer systems and are a common feature across many different platforms.
For lateral movement, the attacker hijacked Pulse sessions to bypass Multi-Factor Authentication (MFA) and move laterally into the VMWare environment. They attempted several different remote access protocols (i.e. RDP and SSH) to utilize valid accounts. Compromised credentials can be used to bypass access controls placed on various resources on systems within the network.
Data were stolen by using the attackers’ own Command and Control (C2) infrastructure.
To hide their activity, the attackers created staging and persistent Virtual Machines (VMs) within the infiltrated VMWare environment. Adversaries can carry out malicious operations using a virtual instance to avoid detection. By running malicious code inside of a virtual instance, adversaries can hide artifacts associated with their behavior from security tools that are unable to monitor activity inside the virtual instance.
MITRE says this is a necessarily incomplete list as the investigation is still ongoing. But from the detailed description, we can tell this was certainly the work of a sophisticated attacker. Other early exploits of these Ivanti vulnerabilities were attributed to a Chinese state sponsored group known as UNC5221.
Recommendations
MITRE lists the following strategies to detect this type of sophisticated attack.
- Anomaly Detection: Monitor VPN traffic for unusual patterns, such as spikes in connections or unusual geographic locations.
- Behavior Analysis: Look for deviations in user behavior, such as unusual login times or accessing unfamiliar resources.
- Network Segmentation: Segmenting networks can limit lateral movement, making anomalous activities more apparent.
- Threat Intelligence Feeds: Stay updated with threat intelligence feeds to identify known malicious IP addresses, domains, or file hashes.
- Adversary Engagement: Deploy adversary engagement resources in your environment, such as deception environments and honey tokens that not only trigger detection but provide deeper insights into adversary TTPs.
As we have said before, to discover atypical behavior, it’s necessary to establish a baseline for normal activity. And a dedicated team of professionals to monitor for unusual behavior is not something every organization has at its disposal, although you can always hire one.




