New in Nebula & OneView: CVE Tags for Ransomware-Linked Vulnerabilities
Joana Pereira, Product Manager Asset & Email Security
Joana Pereira, Product Manager Asset & Email Security
In February 2025, ransomware groups like Cl0p and RansomHub ran riot — targeting organizations across sectors with a mix of zero-days and known vulnerabilities. (Full breakdown here)
To help security teams stay ahead of threats, our Nebula and OneView consoles now display information directly from the Cybersecurity and Infrastructure Security Agency (CISA) regarding vulnerabilities exploited in ransomware campaigns.
Why This Update Matters
CISA curates the Known Exploited Vulnerabilities (KEV) Catalog — a trusted source for vulnerabilities confirmed to be actively exploited in the wild.
CISA added a crucial new indicator: “Known To Be Used in Ransomware Campaigns” – (more information here). This highlights vulnerabilities that have been linked to real ransomware activity in the field. These aren’t theoretical risks — they’re the same CVEs leveraged in attacks like the ones we saw just weeks ago.
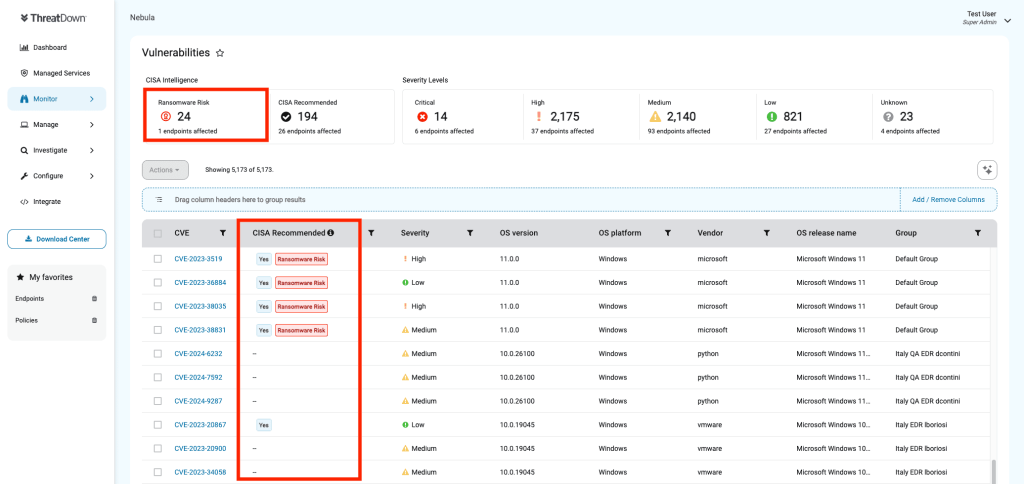
What You’ll See in Nebula & OneView
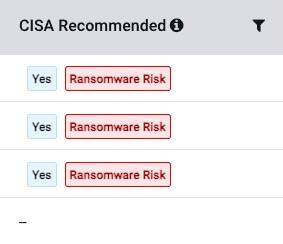
- New “Ransomware Risk” label added to CVEs confirmed by CISA as used in ransomware campaigns
- An info icon that informs these were sourced directly from CISA’s Ransomware vulnerability warning
- All visible in your Vulnerabilities page and CVE detail slide-outs

What You Can Do Now
This integration helps your team identify and prioritize ransomware-linked CVEs faster — so you can patch what matters most, sooner.
Login to Nebula or OneView to see which CVEs in your environment carry this extra layer of risk. And if you missed it, read our full analysis of ransomware in February 2025 to see how these threats are evolving — and what defenders need to know now.
ThreatDown Support articles links:
Cybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of MalwareCybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of Malware