New integration: Nebula and OneView with Google Chronicle SIEM
Users can now act on critical threat insights more effectively.
We’re excited to introduce the integration of ThreatDown Nebula and OneView with Google Chronicle SIEM, designed to streamline detection data management and enhance security analysis for IT teams.
With this integration, IT teams can perform advanced filtering with precise search parameters, streamline data import, and gain deeper insights into suspicious activities with Google Chronicle’s Unified Data Model.
Let’s dive into how to set it up.
How to set up the integration
Here’s a simple step-by-step guide to configuring the Nebula and OneView integration with Google Chronicle SIEM:
1. Generate Google Chronicle SIEM Feed Credentials
- In Google Chronicle SIEM, go to Settings > SIEM Settings > Feeds.
- Click Add New and configure the following:
- Feed Name: Malwarebytes
- Source Type: Webhook
- Log Type: Malwarebytes EDR
- After submitting, copy the Webhook URL and Secret Key for later use.
2. Obtain Google Cloud API Key
- In your Google Cloud Project, navigate to API & Services > Credentials.
- Select Create Credentials > API Key and store the key.
- Restrict the API Key to Chronicle API in the settings.
3. Configure Nebula or OneView
- In Nebula or OneView, go to the Integrate page.
- Find Google Chronicle SIEM and click Configure.
- Enter the Webhook URL, Secret Key, and API Key from previous steps.
- Click Save to complete the configuration.
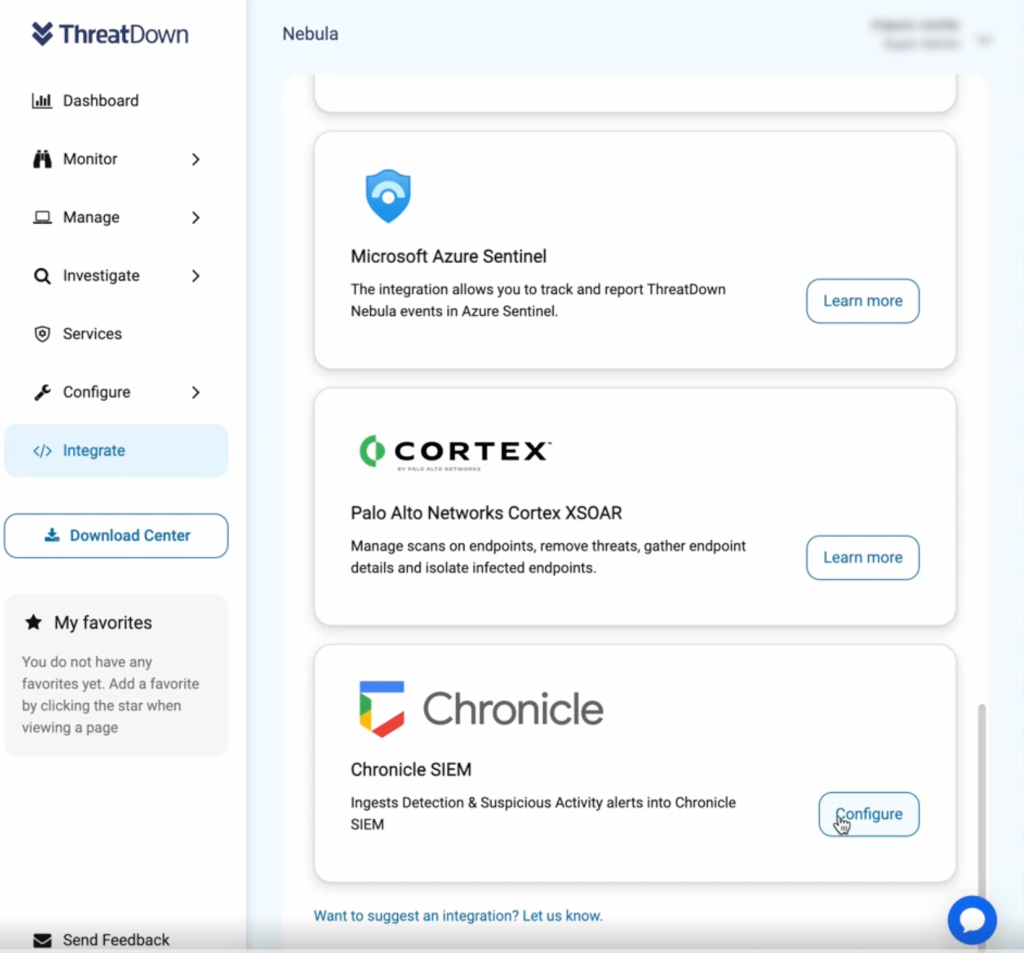

Once the integration is configured, Nebula and OneView will start exporting logs directly into Google Chronicle SIEM. This enables users to access comprehensive data on suspicious activities and other detection events.
Using the integration
With the integration active, you can now use the advanced filtering capabilities within Google Chronicle SIEM to search and analyze data. For instance:
- Go to Investigation > SIEM Search.
- Use a query like:
metadata.vendor_name = "Malwarebytes" and metadata.log_type = "MALWAREBYTES_EDR". - Select the date parameters and run the search.
- View results under the Events tab, where Nebula data will be displayed using a Unified Data Model (UDM).
Try the Google Chronicle SIEM integration today
The Google Chronicle SIEM integration extends Nebula and OneView’s detection data retention beyond their native limitations, offering IT teams long-term storage and analysis, and giving them greater control to act on critical alerts.
For more information on the integration, check here.