
One in five Fortune 500 companies had leaked credentials in the past 30 days
Stolen credentials can open the door for ransomware and Business Email Compromise (BEC).
Research by Malwarebytes shows that 111 Fortune 500 companies (the 500 largest organizations in the USA) have had employee credentials leaked in just the last 30 days.
Leaked credentials can occur for a number of reasons, including phishing, password reuse, brute force password guessing, and data leaks. Losing control of an employee credential represent a serious danger. Cybercriminals can exploit stolen credentials to gain unauthorized access to corporate systems and for lateral movement inside a network—perfect preparation for data theft and ransomware.
Looking further back than 30 days, the number of Fortune 500 companies with leaked credentials in the Malwarebytes data goes up to 363. Which means that 73% of these companies have lost control of at least one employee credential at some point.
The financial impact of ransomware can be devastating. Aside from the ransom itself, recovery can involve legal fees, regulatory fines, operational downtime, and opportunity costs. Beyond financial losses, organizations face reputational damage as customers and stakeholders lose trust in their ability to safeguard data.
Stolen credentials can also open the door for financial fraud like business email compromise (BEC) where cybercriminals impersonate someone inside an organization an employee trusts—like a CEO, vendor, lawyer, or business partner—to trick them into making a fraudulent payment or providing sensitive data.
The situation is even more serious when it comes to user credentials—credentials belonging to people who use services provided by those 500 organizations. A staggering 456 (91%) of Fortune 500 companies have had users’ credentials leaked.
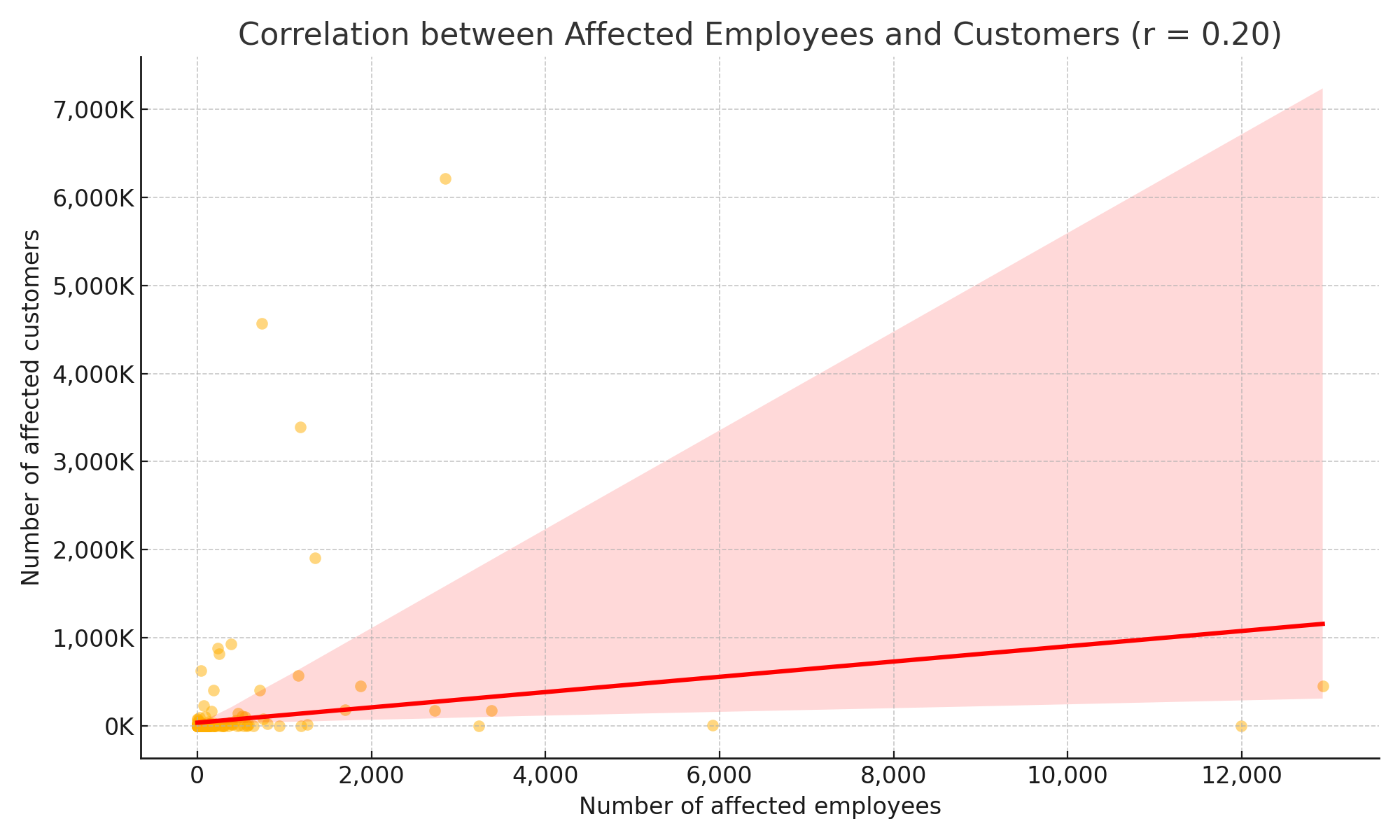
And even though leaked customer credentials are not always the affected companies’ fault, it does seem as if there is a relationship between the number of leaked employee credentials and the number of leaked customer credentials, suggesting that some companies are more resistant to credential leakage than others. (In the graph below, the “r” value refers to the Pearson correlation coefficient. A value of 0.20 indicates a weak positive correlation.)
Countermeasures
To address these risks of leaked customer and employee credentials, organizations must adopt proactive security measures:
- DNS Filtering to protect against phishing.
- Endpoint Detection & Response (EDR) to protect against information stealers, and password guessing.
- Managed Detection & Response (MDR) to ensure EDR is monitored by skilled professionals 24×7.
- Real-time credential monitoring, to detect leaked credentials on the dark web.
- Application blocking to make it harder for attackers to operate inside your network.
- Security awareness training to educate employees on the dangers of leaked credentials.
Cybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of MalwareCybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of Malware


