
Phishers go “interplanetary” to get company login credentials
An ongoing campaign to harvest company login credentials is using IPFS to host its phishing pages.
The InterPlanetary File System is a decentralised, peer-to-peer storage system. Unlike regular storage, it doesn’t rely on a single storage location—files are stored “everywhere” rather than “somewhere”.
Conveniently for cybercriminals, having no one specific location for their phishing sites makes them more difficult to take down.
Since most users won’t have the software they need to access IPFS, criminals who want to host their phishing sites on it rely on gateways that provide IPFS data with HTTP addresses.
In one phishing campaign, things start off pretty normally, with a fake DocuSign email urging the target to download an invoice. (Another campaign starts with a message claiming to come from the mail administrator and links to the same site.)

Clicking the download link opens a phishing site hosted on the IPFS, where the target is asked to confirm their email address.
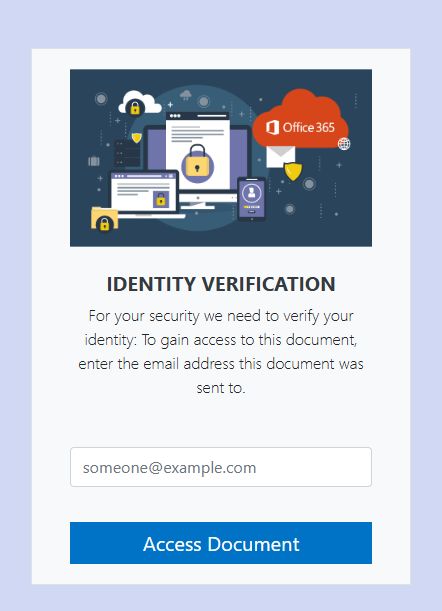
If the target enters their email address and clicks “Access Document”, the site extracts the domain name from the email address and uses it to load an appropriate company logo from logo.clearbit.com, to provide a branded login page.
In our case, we used a malwarebytes.com address and got a Malwarebytes branded login page.
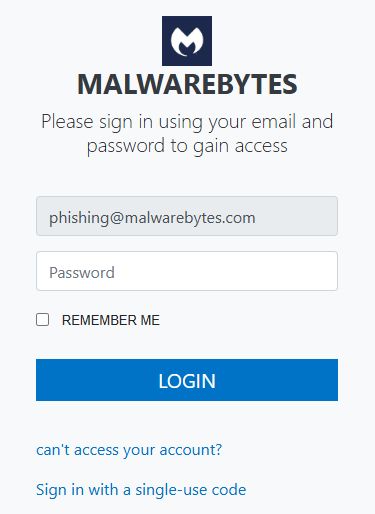
If the target enters a password, it’s sent to the attacker via the Telegram secure messaging app. This is a common tactic in modern phishing campaigns—Telegram provides anonymity for the attacker, and the platform’s bot API makes it easy to automate the collection process.

IPFS is working hard to get the phishing pages removed, but, no surprise for a platform that’s designed to be robust and decentralised, it seems they can’t keep up. New IPFS phishing sites are popping up on a daily basis.





