
Ransomware group disguises SharpRhino trojan as Angry IP Scanner
Researchers have uncovered more details of a Hunters International campaign that uses search ads to spread the SharpRhino RAT.
Researchers have uncovered more details of a malware campaign by the Hunters International ransomware group that uses search ads to spread the SharpRhino remote access trojan (RAT) that can be used to deploy ransomware. The new research builds on work by Malwarebytes’s Senior Director of Research, Jérôme Segura, and other researchers.
The search ads target people looking for the Angry IP Scanner (typically system administrators), and lead them to fake Angry IP Scanner websites with malware-infected downloads.
Since Microsoft made it harder for criminals to smuggle malicious macros into Office Documents in 2022, ThreatDown has seen a surge in the use of malicious advertising to spread malware. By using search ad infrastructure, criminals can target their malware at specific search terms, demographics and geographies, using ads and websites that are indistinguishable from legitimate ones.
One of the groups they target is system administrators, because of the highly privileged access they have to corporate networks. They do this by targeting apps that will appeal to system administrators, such as IP scanners.
Jérôme had previously flagged the early stages of this attack, and the new research shows that this led to ransomware, and attributed it to Hunters International.
Victims who visit the fake Angry IP Scanner site are tricked into downloading SharpRhino, with the misleading filename ipscan-3.9.1-setup.exe. One of the features of SharpRhino is that it can be used to execute Powershell commands on an infected machine, which can be used for all kinds of malicious tasks, including retrieving a system administrator’s credentials.
In short, the malware helps the Hunters International ransomware group to gain access, elevate their privileges, execute commands, and with all that done, deploy ransomware.
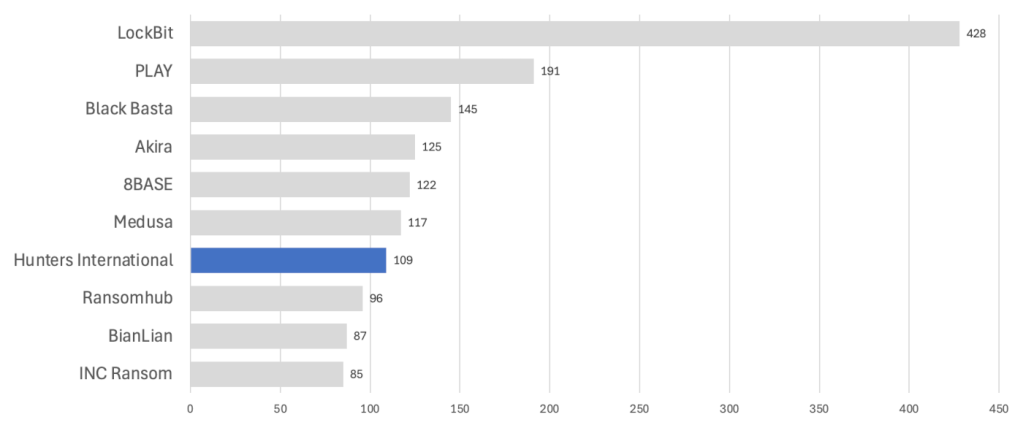
Between January and June 2024, Hunters International has been the seventh most active ransomware group, globally.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.





