
Ransomware in April 2025—RansomHub is gone
While DaVita and Marks & Spencer reel from devastating attacks, the most dominant ransomware group of the last year has disappeared.
In April 2025, dialysis giant DaVita suffered a high-impact ransomware attack at the hands of the lesser-known “Interlock” gang. Oregon’s state environmental agency refused to pay a $2.5 million ransom, so the attackers retaliated by leaking confidential patient data stolen from the company.
Around the same time, one of the UK’s biggest retailers, Marks & Spencer, was forced to suspend its online orders after a “cyber incident” disrupted its e-commerce operations. Bleeping Computer reports that the threat actors behind the attack are believed to be part of the Scattered Spider network. The publication believes that the threat actors cracked password hashes from a stolen NTDS.dit database to allow lateral movement through the organization, before using the DragonForce encryptor to attack VMware ESXi hosts.
In Germany, recycling company Eu-Rec GmbH filed for insolvency after being attacked by the SafePay ransomware group.

The most startling feature of April’s known ransomware attacks by group chart is the absence of the RansomHub group, which emerged as the successor to LockBit and ALPHV in 2024 as the most dominant ransomware gang.
The RansomHub dark web leak site is currently down, and it’s reported that the DragonForce ransomware group recently announced on its own leak site that RansomHub had “decided to move to our infrastructure.” Currently, the DragonForce leak site simply says “We will be up soon”.

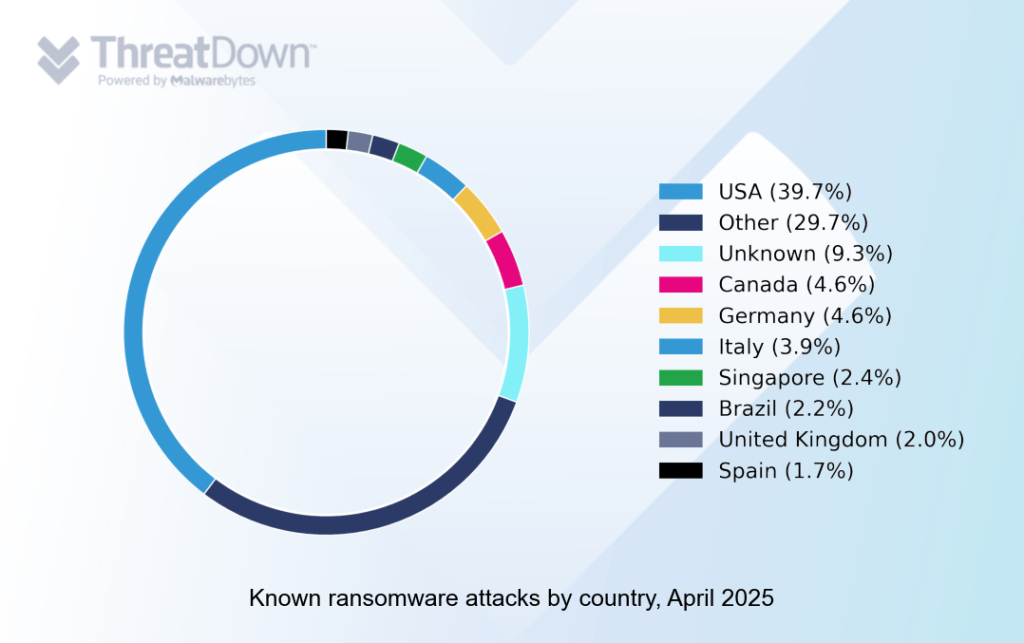
In April, the USA remained by far the most actively targeted country.
Manufacturing was the most attacked sector in April 2025, surpassing even the technology sector. The number of attacks on manufacturing has increased steadily over the last few years.

How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
To learn more about ransomware and how to defend against the Living Off the Land tactics used by ransomware gangs, download the 2025 State of Malware report.
Cybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of MalwareCybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of Malware


