
Ransomware in March 2025
March 2025 saw a huge number of ransomware attacks, and the Pennsylvania State Education Association quietly notify over 500,000 current and former teachers that hackers infiltrated its networks last year.
On March 17, 2025, the Pennsylvania State Education Association quietly notified over 500,000 current and former teachers that hackers from the Rhysida gang had infiltrated its networks in July 2024 and stolen personal data including Social Security numbers, driver’s-license details, and health-insurance records.
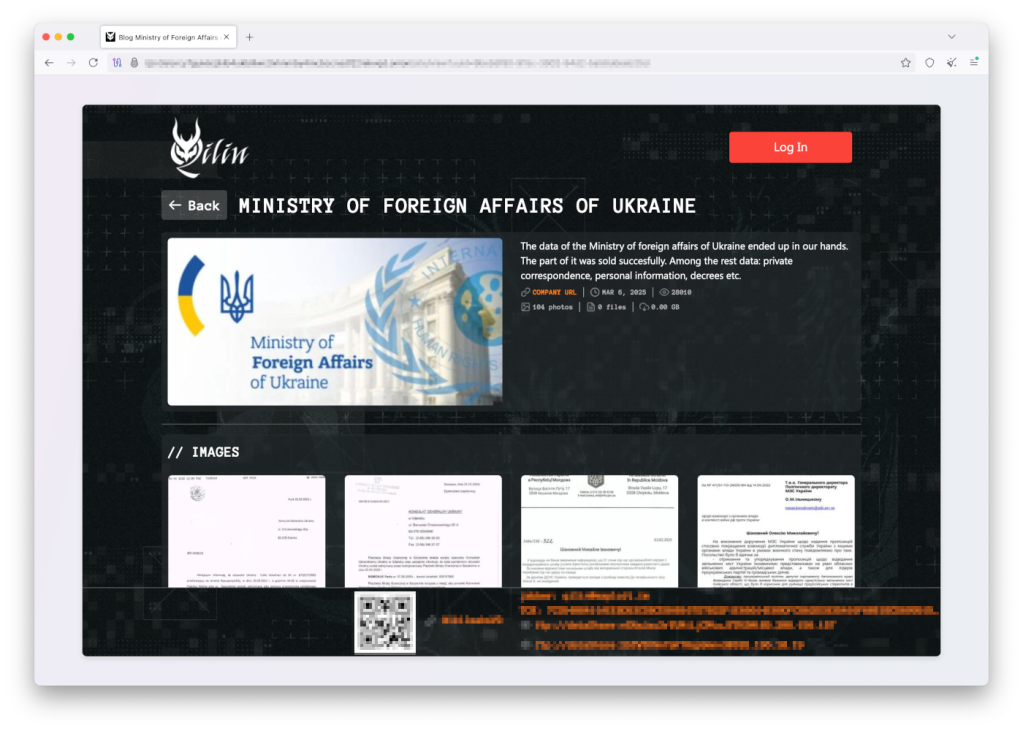
Less than a week earlier, the Moscow-linked Qilin ransomware group took credit for breaching Ukraine’s Ministry of Foreign Affairs, boasting on its dark web leak site that it had stolen private correspondence, official decrees and personal staff data.
In mid-March, the newly emerged Hellcat gang attacked Swiss telecoms specialist Ascom, which confirmed in a March 16 press release that its “technical ticketing system” was breached.
March was also notable for what did not happen—there were no new attacks attributed to the Cl0p ransomware gang. The gang’s sporadic and unpredictable approach means that it is often inactive for several months, before it erupts into life with an automated, zero-day attack. After a few months of breathless activity, the group now seems to have entered one of its dormant phases.
With Cl0p quiet, the list of the top ten most active groups resumed a more typical order. Despite the recent noise and fury from Cl0p, RansomHub remains the most consistently active group.
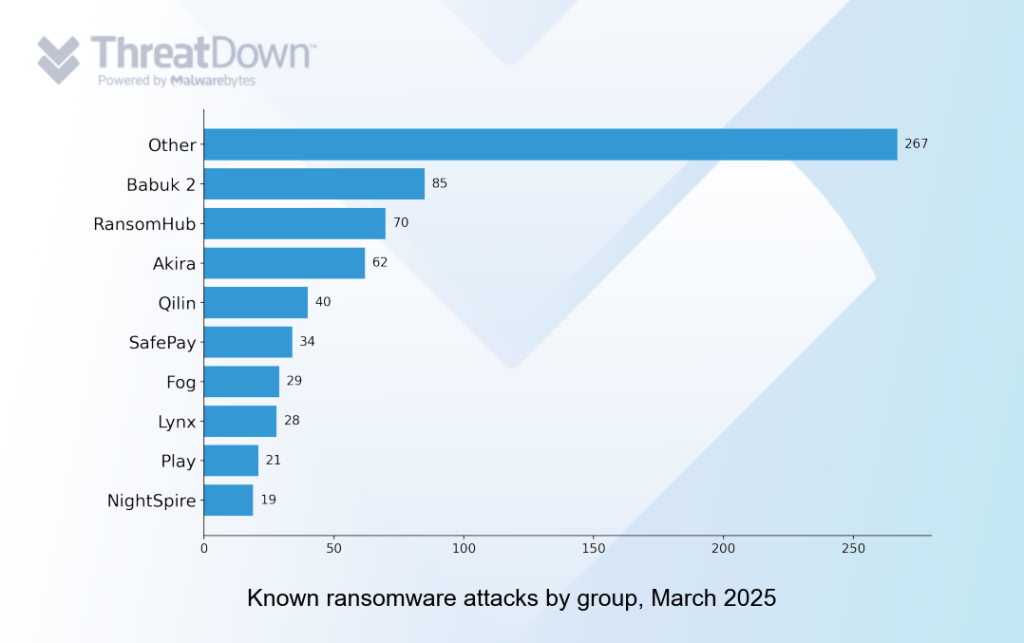
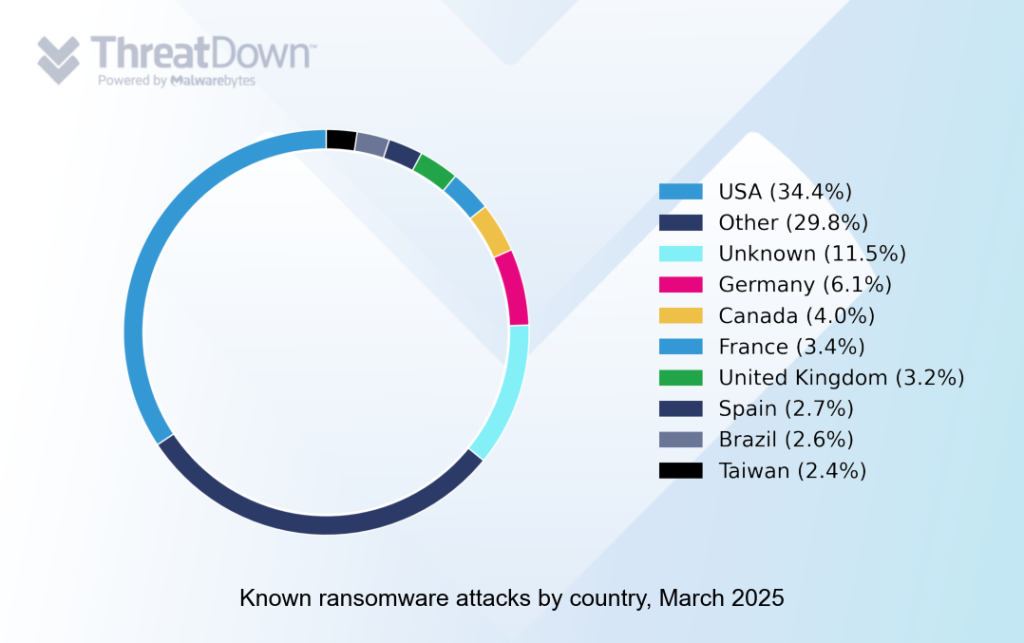
The USA was the biggest target for ransomware gangs in March, as it normally is, but the month saw the USA’s usual share of attacks cut by a surge in ransomware activity in countries outside the top 10.
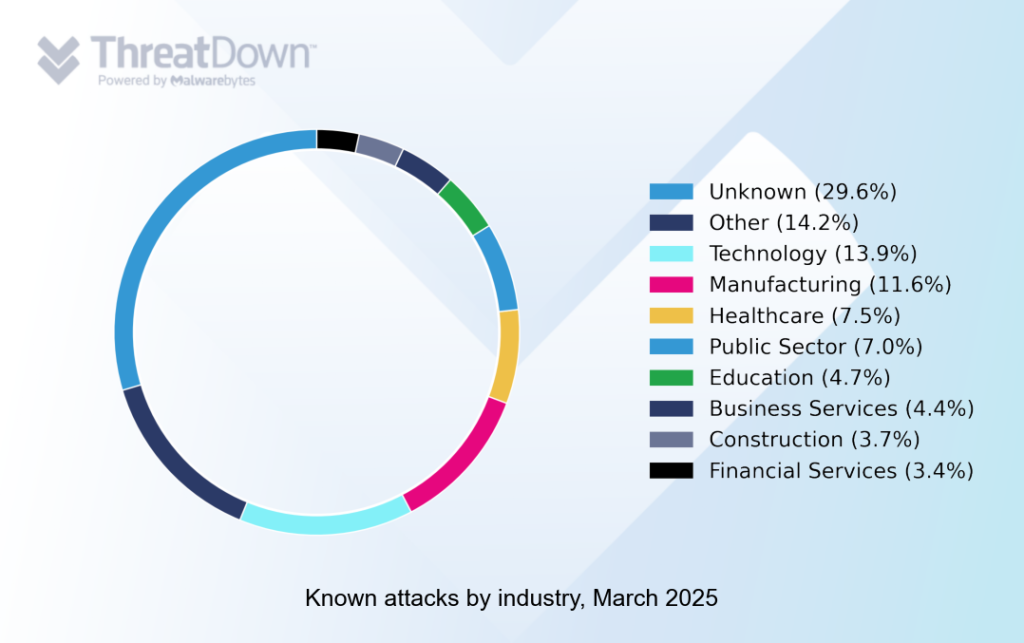
Technology and manufacturing were the most frequently attacked industries in March.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
To learn more about ransomware and how to defend against the Living Off the Land tactics used by ransomware gangs, download the 2025 State of Malware report.
Cybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of MalwareCybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of Malware


