
Don’t touch TP! How ransomware gangs are unplugging your EDR
Tamper Protection stops ransomware gangs from messing with your EDR, unless they get a helping hand.
There are two methods for getting past the laser-triggered machine guns of Fort Knox.
One way is to flash your handheld mirror at them and hope for the best. The other way is to dress as a guard, sneak in, and turn them off from inside the building.
An EDR platform is sort of like those laser-triggered machine guns. It’s seriously bad news for an intruder, but if the intruder can shut it off, it can’t offer any protection.
Disabling an EDR should, in theory, be just as hard as disabling the defenses of Fort Knox. If your EDR Tamper Protection (TP) is misconfigured, though, ransomware gangs have a chance of turning off your organizations’ ‘machine guns’.
ThreatDown Incident Response (IR) data suggests misconfigured Tamper Protection settings are among the prime contributors to successful ransomware attacks. More specifically, the two biggest misconfigurations we see are disabling Tamper Protection altogether and password reuse.
The cost of disabling Tamper Protection
Let’s look at a recent example where a customer was attacked by the Medusa ransomware gang.
When Medusa tried to execute its payload (gaze.exe) at 4:01 AM, the real-time protection layer of ThreatDown EDR stopped it.
Understanding that they couldn’t encrypt any data as long as ThreatDown was watching, Medusa used PDQDeploy (an IT admin deployment software) to run PowerShell scripts across the network that disabled it.
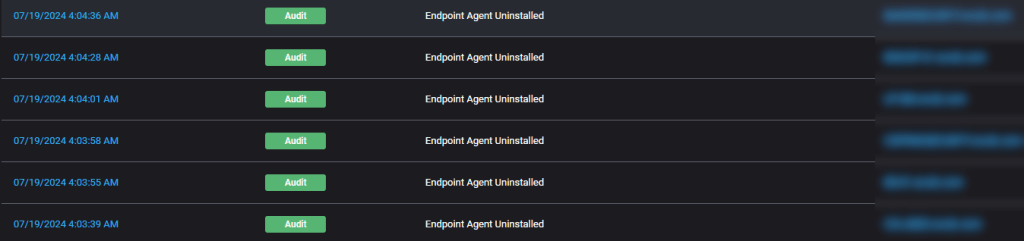
Lo and behold, around 4:06 AM, ThreatDown EDR picked up on Medusa uninstalling the Endpoint Agent across the customer’s environment. This ultimately allowed the gang to deploy the ransomware payload and encrypt data in an unprotected environment. The out-of-the-box Tamper Protection would have stopped this.
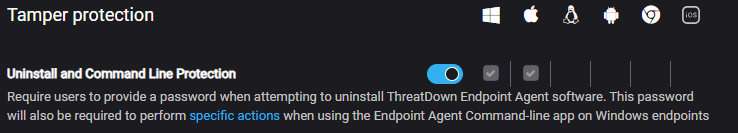
Tamper Protection, which is enabled in any new ThreatDown EDR policy by default, requires users to provide a password when attempting to uninstall the ThreatDown Endpoint Agent software. The default password is 24 characters and contains upper case, lower case, numbers, and symbols. Any custom password must meet the same requirements.
Customers can disable Tamper Protection by turning off the toggle, however, which can be useful for troubleshooting purposes—with the important caveat being to always toggle it back on immediately afterward.
In this instance, the customer had toggled Tamper Protection off, allowing Medusa to disable the Endpoint Agent without entering a password.
Don’t reuse passwords, especially for Tamper Protection!
Besides just simply disabling Tamper Protection to begin with, protecting it with reused credentials is another huge misconfiguration the ThreatDown IR team has seen.
In one case, an IT department reused credentials across several critical systems, including Active Directory (AD) admin accounts and Tamper Protection configurations. After an attacker successfully infiltrated the environment, they used credential dumping to obtain the AD admin password. Using the same password, the threat actor bypassed Tamper Protection, allowing them to disconnect the endpoint agents without hindrance.
In other words, if you reuse credentials across your environment, it doesn’t matter how complex your password is: A successful credential dumping effort can result in your entire security stack getting unplugged.
Tamper Protection best practices
To ensure Tamper Protection is properly configured:
- Just don’t mess with ThreatDown Tamper Protection, it’s on by default.
- Always toggle Tamper Protection back on if you temporarily disable it.
- Never use a password you’ve used elsewhere.
By following these steps, you can confidently say you’ve configured Tamper Protection correctly.
Remember, just like the laser-triggered defenses of Fort Knox, your EDR is only as strong as its configuration. Don’t hand your adversaries the power to disable it.



