Ransom.Samas
ThreatDown is now the name of the Malwarebytes line of business products. References to Malwarebytes below reflect the amazing technology used to first identify the threat.
Short bio
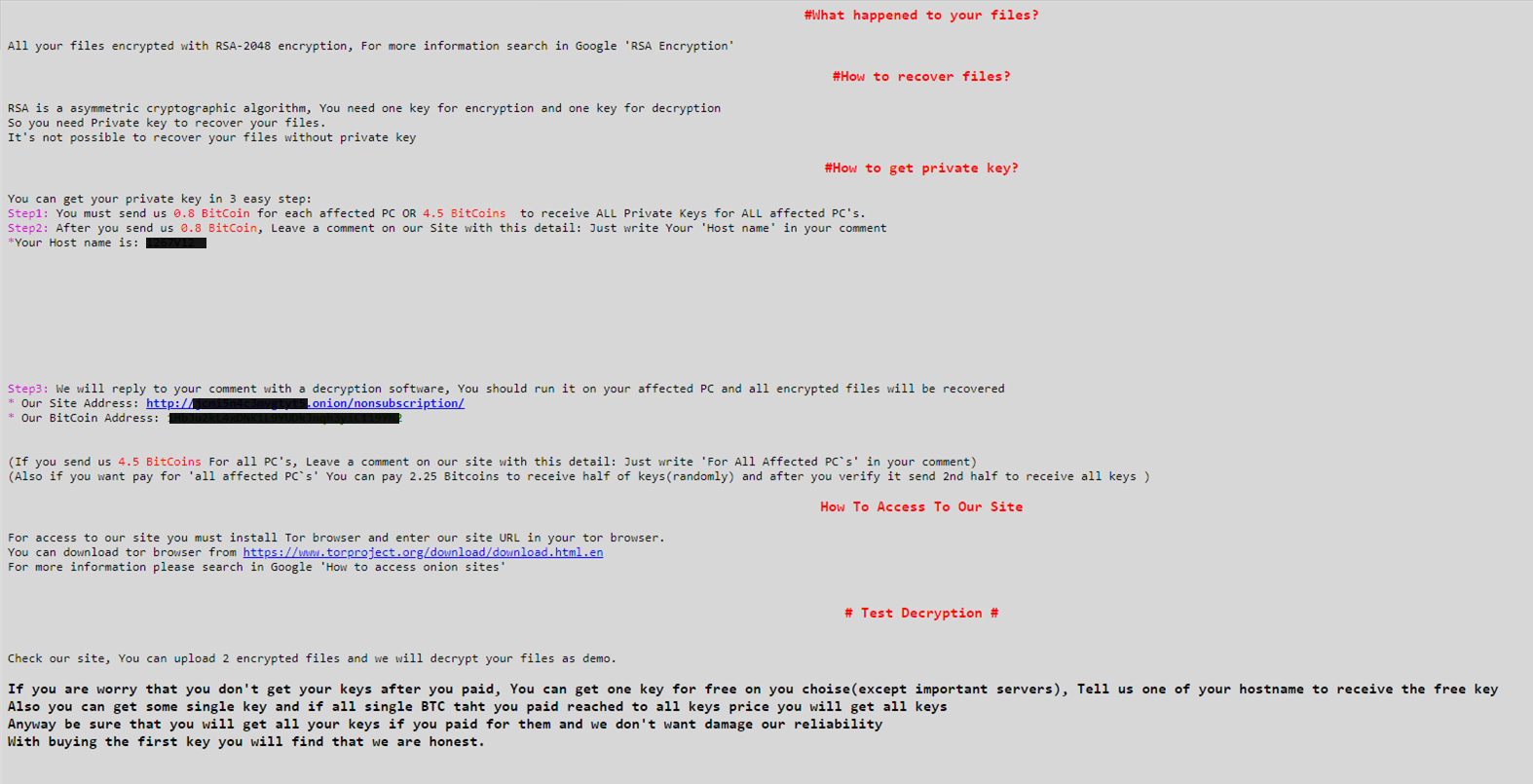
Ransom.Samas is Malwarebytes’ detection name for a family of ransomware applications also known as SamSam ransomware.
Type of infection
Ransom.Samas in general encrypts your files, then forces you to pay a ransom to get them back. The threat actors have been known to target cities and hospitals among others. Ransom.Samas knows several variants, but most of them are spread by brute-forcing RDP endpoints.
Business remediation
To remove Ransom.Samas using Malwarebytes business products, follow the instructions below.
How to remove Ransom.Samas with Malwarebytes Endpoint Protection
- Go to the Malwarebytes Cloud console.
- To allow you to invoke a scan while the machine is off the network, go to Settings > Policies > your policy > General.
- Under Endpoint Interface Options, turn ON:
- Temporarily enable Anti-Rootkit scanning for all invoked threat scans. Go to Settings > Policies > your policy > Endpoint Protection > Scan Options
- Set Scan Rootkits to ON.
- Once the endpoint has been updated with the latest policy changes:
If you have infected machines that are not registered endpoints in Malwarebytes Endpoint Protection, you can remove Ransom.Samas with our Breach Remediation tool (MBBR).
After removing the infection and restoring any lost files (if necessary) it is imperative to find out how the threat-actors gained access. Close the access and scan for any tools or backdoors they may have lft behind.
Home remediation
Malwarebytes can detect and remove Ransom.Samas without further user interaction.
- Please download Malwarebytes to your desktop.
- Double-click MBSetup.exe and follow the prompts to install the program.
- When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantine to remove the found threats.
- Reboot the system if prompted to complete the removal process.
Take note, however, that removing this ransomware does not decrypt your files. You can only get your files back from backups you made before the infection happened.