
Ransomware in February 2025—Cl0p and RansomHub run riot
The Cl0p ransomware group posted data on 335 victims in February 2025, by far the largest one month total any gang has ever recorded.
In February 2025 the Cl0p gang listed 335 victims on its leak site, the most attacks ever recorded by an individual ransomware group in a month. Cl0p’s extraordinary haul is a result of the group’s unique and highly dangerous tactics.
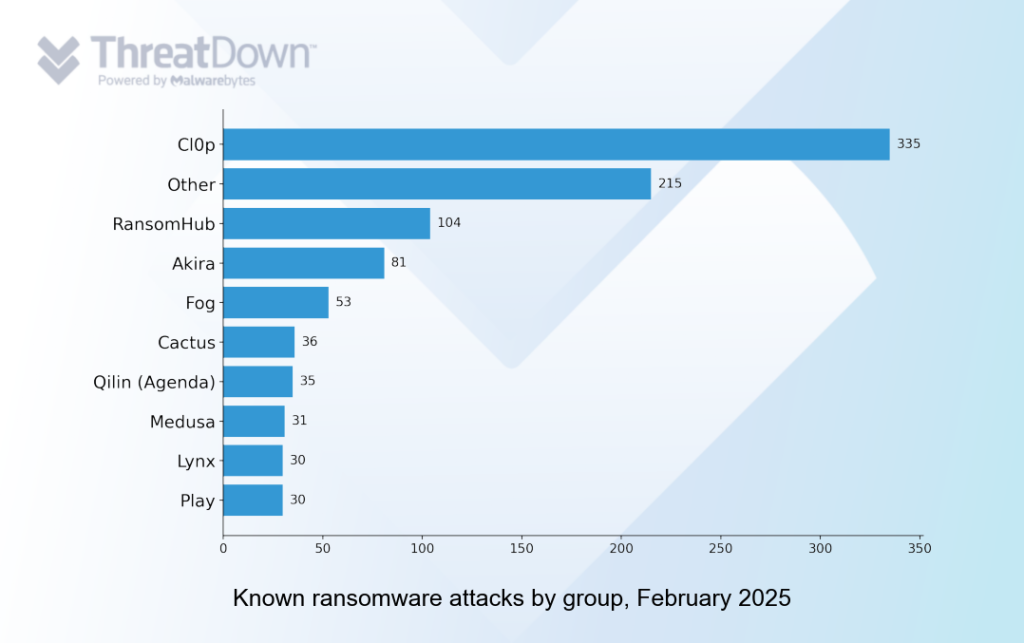
Although it was dwarfed by Cl0p in February, RansomHub’s 104 known attacks would be headline news in any other month. Since the demise of LockBit and ALPHV a year ago, RansomHub has emerged as the dominant force in ransomware, and its 104 victims in February 2025 is the largest monthly total it has ever posted.
Most large ransomware groups, such as RansomHub, use a software-as-a-service model to scale their operations, providing infrastructure and software to a collection of affiliates who carry out attacks. The affiliates break into organizations and use hands-on-keyboard tactics to conduct “double extortion” attacks where they steal copies of the oranization’s data, and encrypt the original files, giving themselves two forms of leverage over their victims.
As a result, individual groups tend to operate at a steady cadence, and report a similar number of known attacks each month (RansomHub averages about 60 known attacks per month, for example).
Collectively the bulk of ransomware groups use similar tactics, so a good defense against one is a good defense against all. But there is an exception—Cl0p.
Cl0p’s sporadic and unpredictable approach is unlike any other mainstream ransomware gang. The group is often inactive for several months, and then erupts into life using an automated attack based on a zero-day exploit. It uses smash-and-grab tactics, extracting whatever data it can pull from the compromised software without encrypting anything. Rather than accumulating victims at a steady state, it can affect hundreds of organizations in just a few days.
The group has a particular liking for file transfer software, and following successful campaigns against GoAnywhere MFT and Progress MOVEit Transfer in 2023, the gang returned in December 2024 after a long hiatus with an attack against Cleo software.
However, while Clop surged into life and RansomHub consolidated its position, another famous ransomware group, 8Base, ran out of road following a coordinated international law enforcement action. Europol reports that as a result of the operation, four of the individuals suspected of leading the group have been arrested, 27 of its servers have been taken down, and law enforcement agencies were able to warn more than 400 companies of ongoing or imminent ransomware attacks.
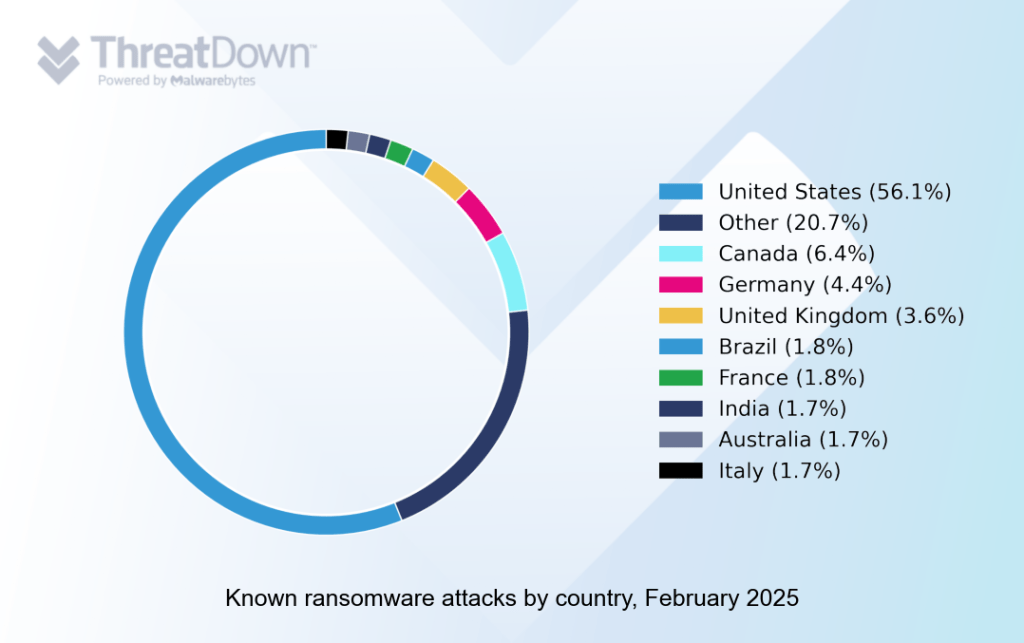
As ever, the USA was by far the biggest target for ransomware gangs, with known attacks inside the USA outnumbering attacks on the rest of the world combined.
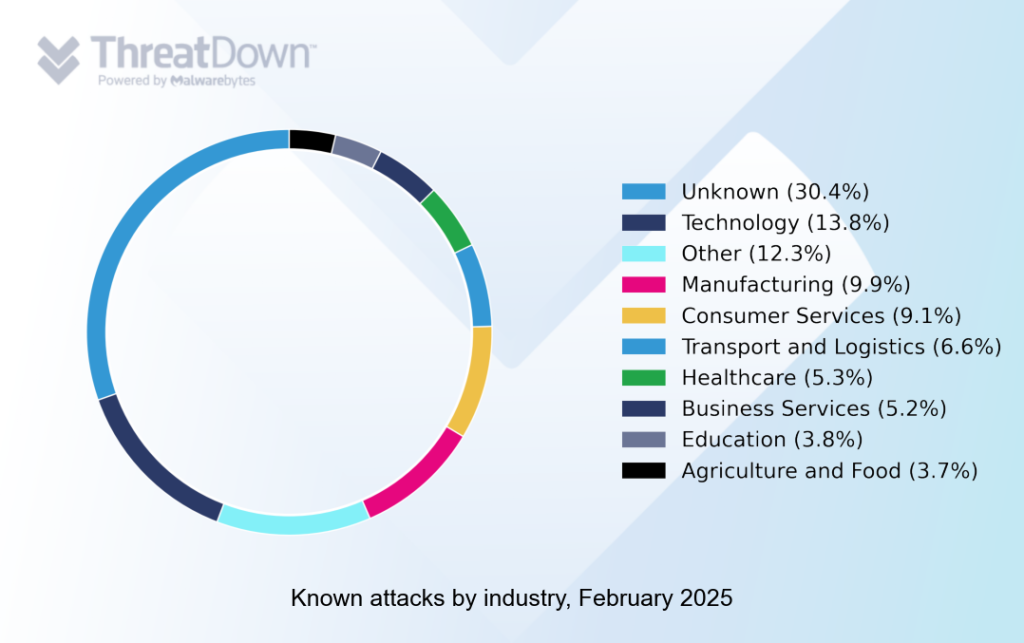
Technology was the most affected industry sector in February 2025, while manufacturing continues to occupy a surprisingly high position in the list.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
To learn more about ransomware and how to defend against the Living Off the Land tactics used by ransomware gangs, download the 2025 State of Malware report.
Cybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of MalwareCybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of Malware


